- Types of Telecom Fraud You Need to be Aware Of
- Subscription Fraud
- Call Termination Fraud
- Wangiri Fraud
- SIM Box Fraud
- CLI Spoofing
- Subscription Resale Fraud
- International Revenue Share Fraud (IRSF)
- PBX Hacking (Private Branch Exchange Hacking)
- SIM Swap Fraud
- Fake Toll-Free Numbers
- 10 Effective Strategies to Prevent Telecom Fraud and Secure Your Business
- 1. Implement Multi-Factor Authentication (MFA)
- 2. Regularly Monitor Telecom Traffic
- 3. Conduct Regular Audits and Risk Assessments
- 4. Educate Employees and Users About Telecom Fraud
- 5. Utilize Advanced Fraud Detection Software
- 6. Secure Your PBX Systems
- 7. Regularly Update Your Network Security
- 8. Implement Call Blocking and Filtering Technologies
- 9. Collaborate with Third-Party Fraud Prevention Providers
- 10. Ensure Compliance with Telecom Regulations
- Smart Technologies That Help Detect and Prevent Telecom Fraud
- Artificial Intelligence (AI) and Machine Learning (ML)
- Blockchain Technology
- Voice Biometrics
- Geolocation Technology
- Data Analytics and Big Data Solutions
- Cloud Computing
- Overcoming the Challenges of Implementing Fraud Detection in the Telecom Industry
- Evolving Fraud Techniques
- High Volume of Data
- Global Nature of Fraud
- Integration with Legacy Systems
- Resource Constraints
- Prevent Fraud With Appinventiv’s Secure Telecom App Development Services
- FAQs
Key takeaways:
- Telecom fraud continues to surge, with global losses now exceeding $1.03 trillion.
- Scams such as SIM swapping, subscription fraud, and call termination fraud are becoming increasingly sophisticated by the day.
- Getting ahead of fraud with solid detection and prevention systems isn’t optional anymore—it’s absolutely critical.
- Companies need to invest in AI-powered fraud detection and real-time monitoring if they want any chance of staying ahead of the criminals and keeping their customers safe.
Telecom fraud is escalating at an alarming rate, posing serious threats to businesses, service providers, and consumers across the globe. Fueled by advancing technologies and an increasingly digital landscape, these scams are becoming more sophisticated, frequent, and costly.
The crooks behind these schemes have become increasingly sophisticated, utilizing cutting-edge tools to identify vulnerabilities in telecom networks. The money lost and the damaged reputations resulting from these attacks are staggering, and the problem continues to spread worldwide.
Here’s a concerning example that illustrates the severity of the issue: someone in Southern California recently lost $21,000 due to SIM swapping fraud (Source: NBC Los Angeles). The criminals essentially hijacked their phone number, which allowed them to bypass security and drain the person’s bank account. This type of incident is becoming increasingly common, posing a serious risk to both businesses and individuals. As these fraudsters continue to find new ways to exploit telecom weaknesses, companies must wake up to the threat they face and implement effective protection strategies.
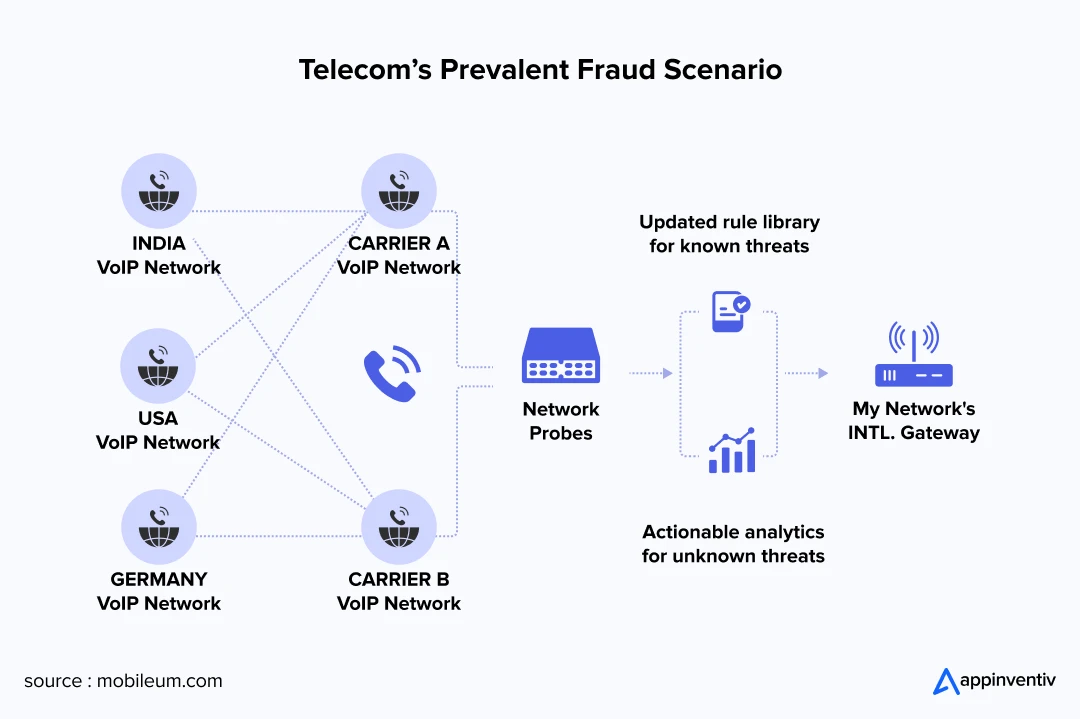
We’re going to break down the different flavors of telecom fraud, why it’s exploding right now, and what businesses can do to shield themselves from these attacks. Getting a handle on these challenges and implementing robust telecom fraud prevention measures helps companies mitigate their risk and maintain their customers’ trust.
Whether you run a telecom company, use telecom systems in your business, or you’re just trying to protect yourself, this growing threat demands action right now. Investing in proven enterprise telecom fraud solutions for businesses is no longer optional.
Let’s delve into this issue and determine how to safeguard your organization against these relentless threats.
Let our experts help you build fraud-proof telecom systems.
Types of Telecom Fraud You Need to be Aware Of
Understanding telecom security threats has become crucial as deceptive practices targeting telecom networks continue to evolve. These schemes are specifically designed to exploit system vulnerabilities for financial gain. Here are the most common and increasingly troublesome types of telecom fraud that businesses and consumers should understand:
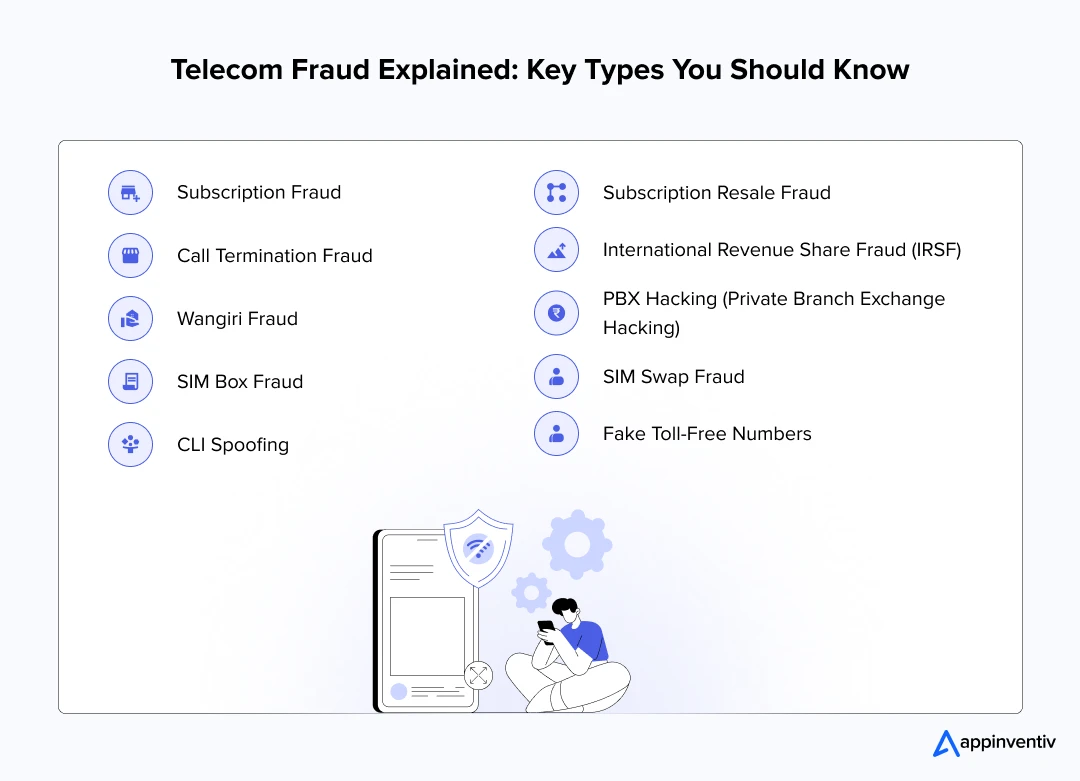
Subscription Fraud
This happens when criminals sign up for telecom services using fake or stolen identities. They provide false information to access services they never plan to pay for. The impact hits telecom companies hard since they often extend credit or provide services upfront, only to discover the customer has vanished before payment is due. Online services with weaker verification processes have made this problem worse over the years. Effective telecom fraud prevention starts with recognizing these subscription-based schemes.
Impact: Telecom companies absorb significant financial losses from unpaid bills, particularly with long-term contracts or premium service plans.
Call Termination Fraud
Criminals redirect calls through unauthorized international gateways to dodge legitimate toll charges. They exploit cheap or illegal routes for international calls, completely bypassing the network fees that should apply. This practice directly cuts into telecom provider revenues since these unauthorized channels either cost nothing or charge substantially less than standard rates. Modern telecom fraud solutions for businesses must account for these routing manipulations.
Impact: Revenue losses for telecom providers, plus increased operational expenses from monitoring and fighting fraudulent routing systems.
Wangiri Fraud
This scam involves criminals making brief calls to victims’ phones from premium-rate numbers, then hanging up immediately. When victims see the missed call and call back, they connect to expensive premium numbers that rack up hefty charges. Automated systems can generate hundreds or thousands of these missed calls quickly, catching unsuspecting victims off guard. Understanding telecom security threats like Wangiri helps consumers avoid these traps.
Impact: Consumers face unexpected charges from calling premium-rate numbers, while telecom providers may suffer reputational damage for hosting these numbers.
SIM Box Fraud
Criminals use devices called “SIM boxes” loaded with multiple SIM cards to route international calls through cheap connections, avoiding standard toll charges. These devices exploit low-cost or free international gateways, causing substantial revenue losses for legitimate telecom providers. The practice often involves complex international networks. Robust enterprise telecom fraud detection solutions are essential for identifying these unauthorized routing patterns.
Impact: Major revenue losses for telecom providers, especially from international call termination fees, plus the illegal bypass of legitimate telecom infrastructure.
CLI Spoofing
CLI Spoofing (a form of IP spoofing) involves manipulating caller-ID or originating IP/endpoint information to make calls appear to come from trusted sources like businesses or government agencies.
By disguising their real identity, criminals increase the likelihood that recipients will answer calls and potentially share sensitive information or make payments. The false sense of legitimacy makes these scams particularly effective. Advanced telecommunication fraud detection systems can help identify spoofed caller identification patterns.
Impact: Identity theft, unauthorized access to personal information, and financial losses for consumers. Telecom providers may face reputation damage if perceived as enabling these activities.
Subscription Resale Fraud
Criminals resell telecom services or data packages without proper authorization, often using stolen payment methods or bypassing authentication systems. They present themselves as legitimate dealers offering discounted services while actually profiting from services paid for by others through fraudulent means. The facade of legitimacy makes these schemes particularly difficult to detect. Monitoring telecom fraud trends helps identify emerging resale fraud patterns.
Impact: Revenue losses for telecom companies who can’t track unauthorized resales, potential breakdown of customer trust, and complications in service management.
International Revenue Share Fraud (IRSF)
Criminals manipulate telecom systems to generate international calls to premium-rate numbers or expensive destinations, then pocket a percentage of the revenue from those calls. They create fake or inflated traffic to these numbers, often exploiting international routes on a massive scale. This fraud can remain hidden for extended periods, causing substantial financial damage to telecom providers. Strengthening telecom network security helps prevent unauthorized access to international routing systems.
Impact: Revenue losses for telecom providers from fraudulent traffic, plus potential damage to international business relationships due to compromised routing systems.
PBX Hacking (Private Branch Exchange Hacking)
Business PBX systems used for internal communication become targets when security measures fall short. Hackers break into company PBX systems to make unauthorized international or toll-free calls that the business ultimately pays for. These attacks often happen during weekends or holidays when monitoring is reduced, giving criminals more time to exploit telecom infrastructure.
Impact: Companies face steep financial losses from unauthorized calls, plus potential reputational damage and trust issues if business communications are compromised.
SIM Swap Fraud
Fraudsters convince telecom providers to transfer victims’ phone numbers to new SIM cards they control, typically through social engineering or exploiting weak verification processes. Once they control the phone number, they access all calls, messages, and two-factor authentication codes. This gives them entry to banking apps, email accounts, and other sensitive information tied to that number.
Impact: Identity theft, unauthorized account access, and major financial losses for individuals and businesses, especially in banking and e-commerce sectors.
Fake Toll-Free Numbers
Criminals establish fake toll-free numbers that mimic legitimate companies or services. When consumers call these numbers, they’re secretly connected to expensive premium-rate lines. This scheme particularly damages businesses by eroding consumer trust and creating financial losses for both consumers and the companies being impersonated.
Impact: Higher billing charges for consumers, reputational harm to businesses, and potential regulatory penalties if fraudsters use toll-free numbers for illegal activities.
10 Effective Strategies to Prevent Telecom Fraud and Secure Your Business
Telecom fraud continues to grow, so businesses must take proactive measures to protect their operations and customers. When companies implement robust fraud prevention measures, telecom service providers and businesses that utilize telecom systems can significantly reduce their risk of being targeted by fraud. Here are some of the top 10 best practices to prevent telecom fraud:
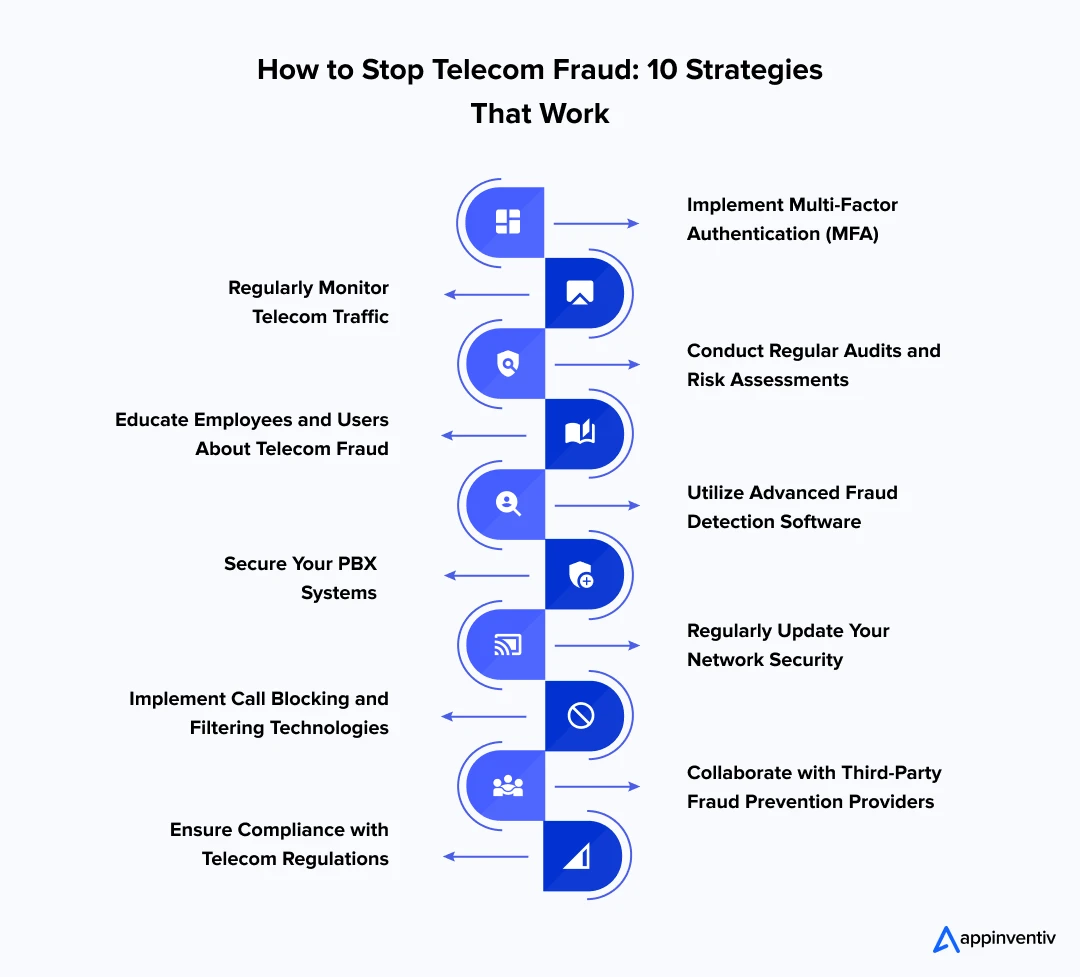
1. Implement Multi-Factor Authentication (MFA)
Multi-factor authentication stands out as one of the strongest ways to lock down accounts and stop unauthorized access. When you require multiple verification steps—like a password, security questions, and a one-time code—you create serious barriers for criminals.
This becomes critical for systems that allow remote access, like PBX systems or telecom apps, where criminals often try to break in and steal sensitive business information. Effective telecom fraud prevention starts with these fundamental security layers. Consider implementing biometric authentication, like fingerprint or facial recognition, for even stronger protection. Regularly review and update MFA settings, especially after employee departures or security incidents.
2. Regularly Monitor Telecom Traffic
Watching your telecom traffic in real-time helps you catch unusual patterns or usage spikes that scream fraud. Set up automated systems that ping you immediately when something looks off, whether it’s unauthorized international calls, sudden call volume jumps, or spikes in premium-rate calls. Staying alert to telecom fraud trends helps you spot emerging attack patterns before they cause serious damage.
Establish baseline usage patterns for your organization so you can quickly identify deviations from normal behavior. Create detailed logs that track call destinations, duration, and timing to help investigators trace fraudulent activity.
3. Conduct Regular Audits and Risk Assessments
Regular audits of your telecom services and risk assessments reveal weak spots in your system before criminals find them. This means checking your billing processes, network security, and access controls for vulnerabilities. A solid audit shows you exactly where fraudsters might slip through the cracks. Smart telecom fraud solutions for businesses always include comprehensive auditing protocols.
Schedule these assessments quarterly at a minimum, or immediately after any significant system changes or security incidents. Bring in external auditors periodically to get fresh eyes on your security posture and identify blind spots your internal team might miss. Document all findings and create action plans with clear timelines for addressing identified vulnerabilities.
4. Educate Employees and Users About Telecom Fraud
Knowledge remains your strongest weapon against telecom fraud. Train your team to recognize fraud attempts, such as phishing calls, SIM swapping, or suspicious login attempts. At the same time, teach your customers about telecom fraud risks, including scams like Wangiri fraud or fake subscriptions. Understanding common telecom security threats helps everyone stay one step ahead of criminals.
Create regular training sessions that cover the latest fraud tactics and update materials as new threats emerge. Develop clear protocols for reporting suspicious activity and ensure that everyone knows who to contact when something appears to be amiss. Consider sending periodic security awareness newsletters or tips to keep fraud prevention at the forefront of both staff and customers’ minds.
5. Utilize Advanced Fraud Detection Software
Investing in advanced AI-based telecom fraud detection systems can help identify fraudulent behavior before it occurs. These systems analyze telecom traffic, customer behavior, and network activity to identify anomalies and prevent fraud before it causes harm. Modern telecom fraud detection solutions use sophisticated algorithms to identify threats faster than traditional methods.
Look for solutions that can adapt and learn from new fraud patterns, becoming more effective over time. Integration with your existing telecom infrastructure should be seamless to avoid disrupting normal operations. Ensure the system provides detailed reporting and analytics, allowing you to understand attack patterns and continuously improve your defenses.
Also Read: How Much Does It Cost to Build a Fraud Detection Software?
6. Secure Your PBX Systems
Private Branch Exchange systems attract fraudsters like magnets because they offer easy access to make unauthorized calls. Make sure your PBX system has rock-solid configuration with strong password policies, firewall protection, and encryption protocols to block unauthorized access and toll fraud. Comprehensive telecom fraud prevention requires special attention to PBX vulnerabilities.
Disable unnecessary features and ports that could serve as entry points for attackers, and regularly update firmware to patch known security vulnerabilities. Set up call restrictions that prevent international or premium-rate calls unless specifically authorized by management. Monitor PBX logs regularly for signs of unauthorized access attempts or unusual calling patterns that might indicate a breach.
7. Regularly Update Your Network Security
Keeping your network security current is absolutely essential for fighting telecom fraud. Install firewalls, intrusion detection systems, and regular security patches to fix vulnerabilities in your network infrastructure. Ensure all endpoints, including employee devices and telecom equipment, remain protected from external threats. Advanced telecommunication fraud detection depends on maintaining updated security protocols.
Create a patch management schedule that prioritizes critical security updates and test patches in a controlled environment before deploying them across your network. Implement network segmentation to limit the damage if one part of your system gets compromised. Regular penetration testing can help identify weaknesses before criminals discover them.
8. Implement Call Blocking and Filtering Technologies
Call blocking and filtering technologies work wonders for reducing fraud by stopping incoming calls from suspicious or high-risk numbers. These systems automatically filter out calls from known fraudsters, preventing them from reaching your network in the first place. Following best practices to prevent telecom fraud means leveraging these protective technologies.
Configure your systems to block calls from countries or regions where you don’t conduct business, and maintain updated blacklists of known fraudulent numbers. Set up whitelists for trusted contacts and business partners to ensure legitimate calls always get through. Review and update your filtering rules regularly as new fraud patterns emerge and attack methods evolve.
9. Collaborate with Third-Party Fraud Prevention Providers
Partnering with specialized third-party fraud prevention providers can seriously strengthen your defenses. These providers offer advanced fraud detection tools, monitoring services, and real-time alerts to help protect your business from new fraud schemes. Working with experts ensures your telecom fraud prevention strategy stays current with evolving threats.
Choose providers that offer 24/7 monitoring since fraud attacks often happen outside normal business hours when your internal team isn’t watching. Look for partners who share threat intelligence and collaborate with other organizations to spot emerging fraud patterns across the industry. Ensure that any third-party solution integrates seamlessly with your existing systems and provides clear escalation procedures for handling detected threats.
10. Ensure Compliance with Telecom Regulations
Staying compliant with local and international telecom regulations protects your business from fraud while reducing legal risks. Ensure your business adheres to telecom industry standards and regulatory requirements, such as those established by the Federal Communications Commission (FCC) or the European Telecommunications Standards Institute (ETSI). Regulatory compliance forms a crucial part of any comprehensive telecom fraud prevention framework.
Keep detailed records of your compliance efforts and regularly review regulatory changes that might affect your operations. Consider appointing a compliance officer who stays current with evolving regulations and ensures your fraud prevention measures meet all legal requirements. Non-compliance can result in hefty fines and legal troubles that compound the damage from any fraud attacks you might experience.
Implement secure app development practices to safeguard your telecom operations.
Smart Technologies That Help Detect and Prevent Telecom Fraud
As telecom fraud becomes increasingly sophisticated and complex, telecom providers and businesses are combating it with cutting-edge technologies to detect, prevent, and mitigate fraudulent activities. These tools provide companies with the necessary tools to protect their telecom networks and services from increasingly sophisticated fraudsters.
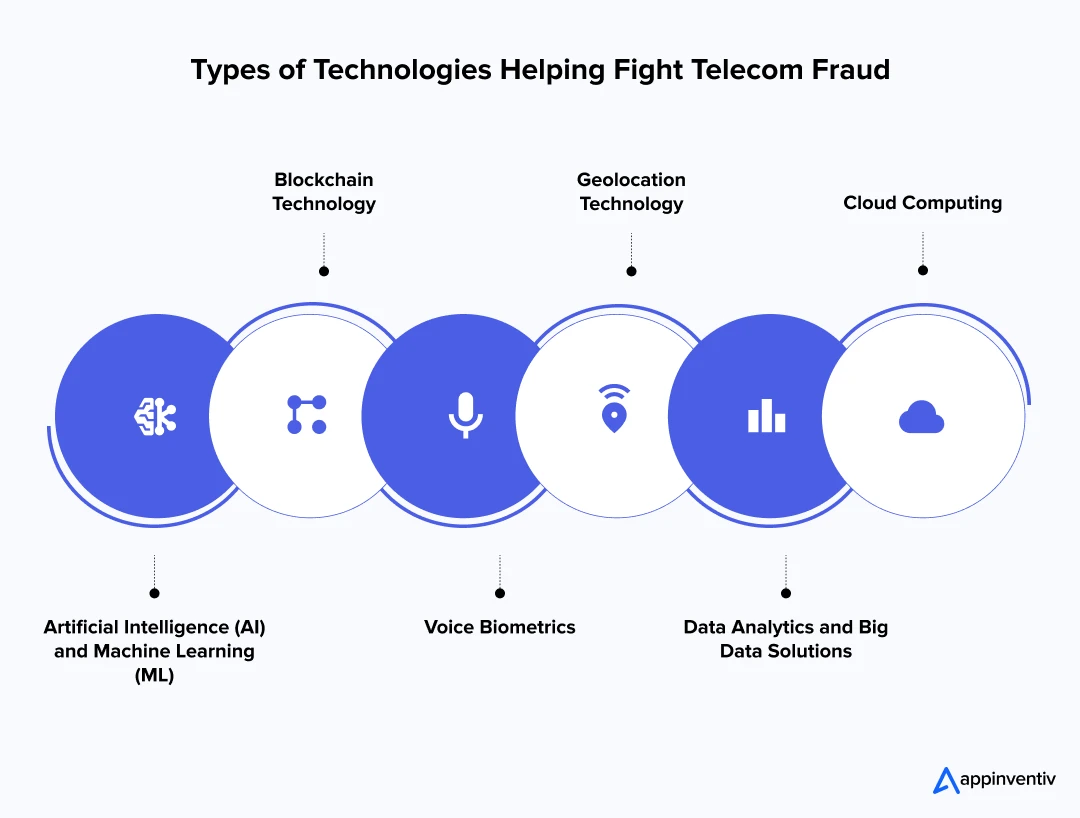
Artificial Intelligence (AI) and Machine Learning (ML)
Artificial Intelligence and Machine Learning are leading the charge in modern fraud detection and prevention. These technologies sift through massive amounts of data using sophisticated algorithms to identify patterns and unusual behaviors that may signal fraud. The use of AI in the telecom industry helps in detecting fraud, as its systems are trained on past fraud cases, allowing them to continually improve at recognizing new scam tactics as criminals evolve their methods.
When telecom companies deploy AI-powered systems, they can detect and prevent suspicious activities as they occur, shutting down fraud before it causes real damage. Again, telecom fraud detection using machine learning enables real-time identification of anomalies, helping stop fraud before it escalates.
Blockchain Technology
Blockchain brings something entirely different to the fraud-fighting game due to its decentralized, secure, and immutable structure. Every transaction recorded on a blockchain remains transparent and can’t be altered, creating a bulletproof system for telecom transactions.
Telecom providers can utilize blockchain to maintain secure records of all service transactions, ensuring that fraudsters cannot manipulate the data. Additionally, blockchain’s smart contracts automatically enforce rules and conditions, ensuring that only authorized users receive services and blocking fraudulent activities.
Voice Biometrics
Voice biometrics represents cutting-edge technology that utilizes each person’s unique voice characteristics to verify their identity. This technology works particularly well for preventing fraud during telecom customer service calls.
Voiceprints get created by analyzing vocal features like pitch, tone, and rhythm—elements that make each person’s voice unique. Modern telecom fraud detection software often includes voice biometrics to prevent fraudsters from pretending to be real customers over the phone, adding serious security when people access sensitive accounts.
Geolocation Technology
Geolocation technology helps telecom providers spot and prevent fraud by tracking where users actually are. By monitoring device locations and network activity, businesses can catch discrepancies that might indicate fraudulent behavior, like SIM swaps or unauthorized international roaming.
Effective telecom fraud prevention relies heavily on these location-based detection methods. When user activity suddenly jumps to a new or unexpected location, geolocation tools trigger alerts and prompt investigation, helping stop fraud before it spreads.
Data Analytics and Big Data Solutions
The use of data analytics in telecom and big data technologies allows companies to detect fraud by processing large volume of information from various sources. By analyzing data on customer behavior, billing activities, and network usage, telecom providers can spot unusual patterns that may signal potential fraud.
Advanced fraud analytics in the telecom sector help businesses manage this complex data, uncover emerging threats, and identify fraud patterns. These solutions also offer predictive analytics, enabling companies to anticipate future risks and proactively prevent fraudulent activity before it happens.
Cloud Computing
Cloud computing in telecom has fundamentally transformed how the industry approaches fraud prevention. When telecom providers migrate their infrastructure, data storage, and fraud detection tools to the cloud, they gain exceptional flexibility, processing speed, and scalability. Cloud-based systems enable real-time access to vast data volumes, allowing for rapid threat identification and immediate response to suspicious activities across any location.
What makes cloud computing particularly effective is its seamless integration with AI, machine learning, and real-time monitoring technologies. This powerful combination allows telecom companies to automate fraud detection processes, deploy security updates instantly, and scale their defensive capabilities as networks expand. Cloud platforms also provide centralized security management and continuous updates, ensuring telecom systems remain protected against emerging threats.
Overcoming the Challenges of Implementing Fraud Detection in the Telecom Industry
The telecom industry encounters numerous roadblocks when attempting to establish effective fraud detection strategies. As criminals become more sophisticated and telecom operations expand globally, providers face significant challenges in protecting their networks and customers. Here are five major hurdles, plus practical solutions to strengthen telecom fraud prevention efforts.
Evolving Fraud Techniques
Challenge: Fraudsters continually adapt to new technologies, necessitating that detection systems receive constant updates to remain relevant.
Solution: Invest in AI-powered systems that grow and change alongside emerging fraud patterns. Utilize machine learning for predictive analytics that can identify threats before they fully emerge.
High Volume of Data
Challenge: The massive amount of data generated by telecom networks can overwhelm fraud detection systems, rendering them slow and ineffective.
Solution: Roll out real-time analytics platforms designed to handle huge datasets efficiently. This ensures fast detection without messing up service quality for legitimate customers.
Global Nature of Fraud
Challenge: Criminals frequently operate across international borders, exploiting varying regulations and legal gaps between countries.
Solution: Work closely with international telecom organizations and deploy cross-border fraud detection tools that follow local laws. Understanding global telecom security threats helps create more comprehensive protection strategies.
Integration with Legacy Systems
Challenge: Many telecom companies still rely on outdated systems that are incompatible with modern fraud detection technologies.
Solution: Gradually update or integrate these older systems with advanced fraud detection tools. Plan the transition carefully to ensure smooth adaptation without causing major service disruptions.
Resource Constraints
Challenge: Smaller telecom providers often lack the budget or staff to implement comprehensive fraud detection solutions independently.
Solution: Partner with third-party fraud management services that provide scalable, cost-effective telecom fraud solutions for businesses. These services are specifically designed for smaller companies that need protection but can’t afford massive internal security teams.
Prevent Fraud With Appinventiv’s Secure Telecom App Development Services
Telecom fraud isn’t slowing down—it’s getting smarter every day. That’s why building secure, intelligent applications isn’t just a good idea anymore; it’s absolutely essential for survival. At Appinventiv, we craft telecom solutions that come loaded with fraud prevention built right in, rock-solid data protection, and continuous threat monitoring to keep you one step ahead of every attack.
The numbers tell our story. We helped a major US telecom company by building a data analytics platform that completely transformed its operations. The results were incredible: 85% better data quality and 26% lower operational costs. But here’s the real win—these improvements didn’t just boost performance. They also strengthened their fraud defenses by eliminating data blind spots and making decision-making lightning fast.
Maybe you want to build stronger customer trust, stay compliant with regulations, or cut down fraud risks. Whatever your goal, Appinventiv has the tools and expertise to help you achieve it. As a telecom software development company, we build everything from secure authentication systems to AI-powered threat detection, making sure security isn’t an afterthought—it’s the foundation.
Team up with us and watch your telecom application become an unbreakable fortress of trust, performance, and resilience. When you work with Appinventiv, you are securing your telecom app from the prying eyes of hackers and fraudsters.
FAQs
Q. How to prevent telecom fraud?
A. Stopping telecom fraud takes a mix of smart technology, constant monitoring, and educating your team and customers. Effective telecom fraud prevention means taking these key steps:
Set up strong authentication: Use multi-factor authentication and tough password rules to keep unauthorized users out of accounts.
Watch network traffic constantly: Use real-time detection systems to catch weird patterns and block suspicious activity immediately.
Do regular security checkups: Audit your telecom services and infrastructure regularly to find weak spots that criminals might exploit.
Get advanced detection software: Invest in AI-powered systems that use machine learning to spot and stop fraud automatically.
Educate everyone about fraud: Ensure that customers and employees are aware of common scams, including phishing, SIM swapping, and fake subscription services.
Follow the rules: Stay current with telecom regulations and make sure your business meets anti-fraud requirements.
Q. What is the most common detection method for fraud?
A. Real-time traffic monitoring takes the lead as the most common fraud detection method. This involves continuously monitoring network activity, call data, and account behavior to identify unusual patterns or spikes that may indicate fraud.
Modern telecom fraud detection solutions are increasingly utilizing machine learning to identify new fraud tactics by analyzing past data and predicting potential fraud scenarios.
Q. What are the rules in fraud detection?
Fraud detection rules are preset conditions that trigger alerts when something suspicious happens. These rules provide automated responses to suspicious activities, helping protect telecom services from telecom security threats.
- Weird traffic patterns
- Excessive usage
- Multiple account sign-ups
- Strange locations
- Failed login attempts
Q. What technologies are used for real-time telecom fraud detection?
A. Several cutting-edge technologies power real-time fraud detection:
- AI and Machine Learning
- Big Data Analytics
- Cloud Computing
- Geolocation Tracking
- Voice Biometrics
- Blockchain Technology
Q. How much does it cost to build a telecom software?
A. Building telecom software can cost anywhere between $40,000 and $300,000+, depending on what you need. Simple apps tend to be less expensive, while feature-rich platforms with analytics and security tools often come at a higher cost. It comes down to complexity and integrations. For a clear estimate, it’s best to talk to a telecom software expert.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

Why OSS Architecture is the Innovation Engine Behind Next-Gen Telecom?
In an era where 5G rollouts, network slicing, and edge computing are redefining connectivity, telecom operators are under increasing pressure to innovate fast and operate smarter. Behind the scenes of these headline-grabbing advancements lies a less glamorous, but critical, component of the telecom engine: Operational Support Systems (OSS). OSS architecture in telecom may not be…

Telecom Billing Software Development - Benefits, Features, Process, Costs
The world runs on connectivity. Whenever someone taps their phone to stream, pay, or simply scroll, they trigger a chain reaction across a highly complex telecom infrastructure that processes, tracks, and bills their usage in real time. Behind these seemingly instant transactions lies a sophisticated ecosystem of telecom billing software. The Telecom Billing and Revenue…

How Much Does It Cost to Develop a Telecom App Like My WE?
When it comes to the Egyptian markets, My WE is the undisputed titan, ruling the telecom sector with its unparalleled features and widespread user adoption. With its growing popularity, the app has become a benchmark for telecom applications, captivating users with its intuitive design and robust capabilities. As businesses and entrepreneurs set out to create…