- Understanding Cloud Security in 2026?
- The Shared Responsibility Model: Who Does What?
- The Unique Challenges of Securing Cloud Environments
- The New Shape of Cloud Threats
- Comprehensive List of Cloud Security Risks, and How to Mitigate Them?
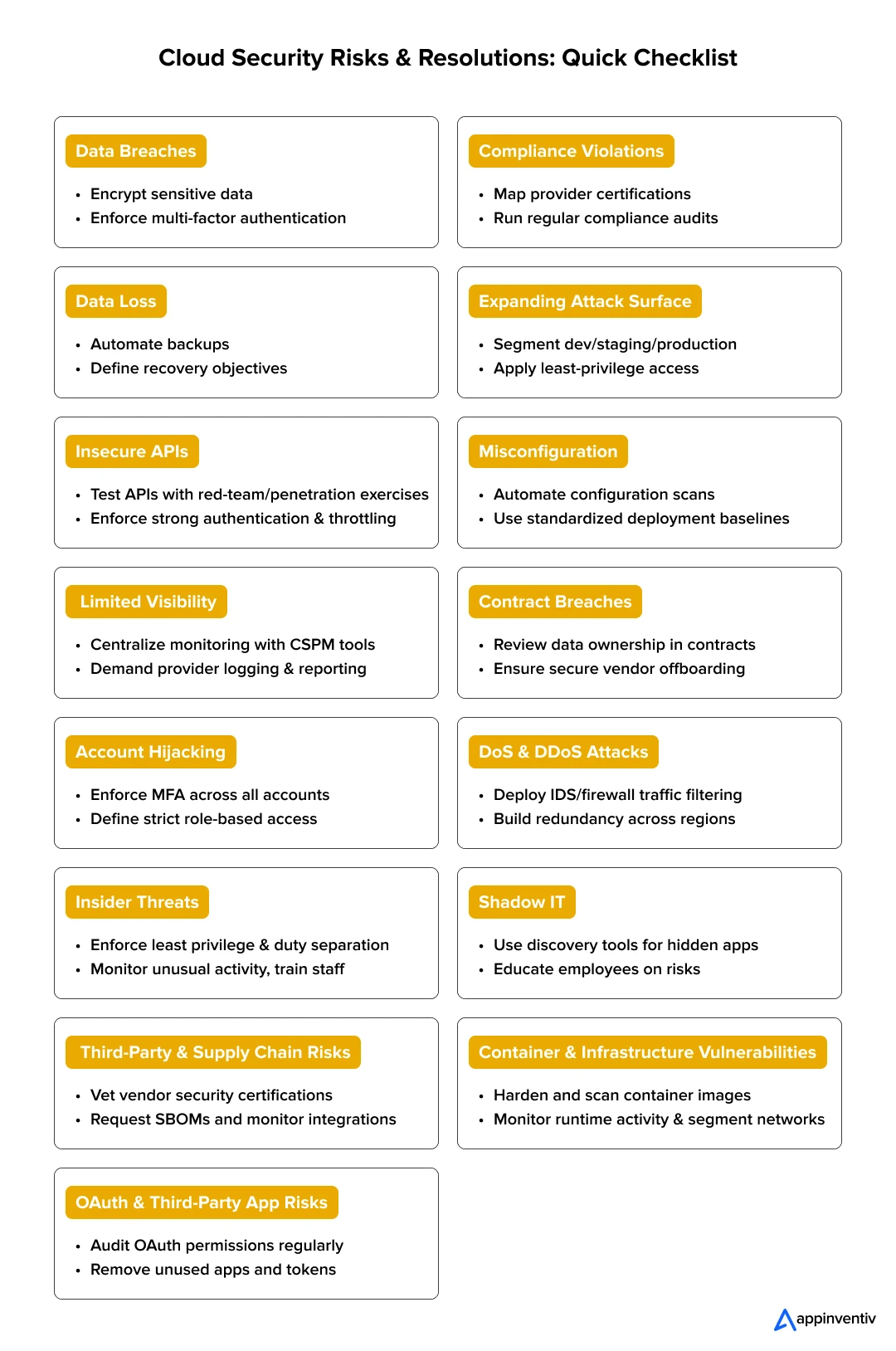
- 1. Data Breach
- 2. Compliance Violations
- 3. Data Loss
- 4. Expanding Attack Surface
- 5. Insecure APIs
- 6. Misconfiguration
- 7. Limited Visibility of Cloud Usage
- 8. Contract Breaches with Business Partners
- 9. Account Hijacking
- 10. DoS and DDoS Attacks
- 11. Insider Threats
- 12. Shadow IT (Unmanaged Cloud Usage)
- 13. Third-Party & Supply Chain Risks
- 14. Container & Infrastructure Vulnerabilities
- 15. OAuth & Third-Party App Risks
- Best Practices for Cloud Security and Beyond
- Adopting a Zero Trust Security Model
- Continuous Monitoring and Incident Response
- Regular Employee Training and Awareness Programs
- Automated Security Assessments and Audits
- Strong Vendor Management and Supply Chain Security
- Encryption and Key Management
- How to Choose the Right Cloud Security Partner
- Partner with Appinventiv to Overcome Cloud Security Risks
- Case Studies That Prove Our Cloud-Driven Expertise
- FAQs
Key takeaways:
- Cloud security risks in 2026 go beyond data breaches as insider threats, shadow IT, third-party vulnerabilities, and container misconfigurations are now front and center.
- A solid defense means combining cloud security solutions like Zero Trust, continuous monitoring, encryption, and automated audits.
- Cloud risk management should be proactive: run regular cloud security risk assessments and enforce least privilege access to minimize human error.
- Choosing the right cloud security solutions provider is critical. Certifications, compliance readiness, and future-proof planning for next-gen threats must be on your checklist.
- Appinventiv’s proven track record with clients like IKEA, YKA, and others shows how secure cloud solutions can reduce costs, improve efficiency, and eliminate critical vulnerabilities.
It’s October 2025. Headlines across the globe reports that over 17.3 million records have been exposed in a wave of data breaches affecting the finance, healthcare, retail, and government sectors alike.
For any company, a data breach is the ultimate nightmare. In just the second quarter of 2025, almost 94 million records were exposed, affecting millions of individuals across the globe. Once stolen, this information rarely disappears; it often resurfaces on the dark web, traded like currency (Source: Statista).
To safeguard against such incidents, organizations must prioritize strong cybersecurity measures for businesses that go beyond reactive defenses.
Silicon Valley Bank was closed down by the California Department of Financial Protection and Innovation following a bank run that was sparked by possible insolvency and a stock market decline. The major reason behind the SVB shutdown is cyber fraud potential.
These incidents are reminders that cloud dependence, while powerful, brings its own set of vulnerabilities. Businesses that assume cloud equals safety are dangerously mistaken. Because the accessibility, size, and interconnectedness of data have now become incredibly susceptible to numerous cloud security risks that attackers are eager to exploit.
Therefore, it can be rightly said that data safety is crucial in terms of cloud computing security risks. This urgency is reflected in market growth too. As reported by Statista, the global cloud security software market is expected to reach $37 billion by 2026. (Statista)

So, your organization must have a strong strategy to protect itself against cloud security threats and ensure business continuity. But to have a strong cloud security strategy, you must first be aware of the top cloud security issues and their possible solutions.
That’s why this blog takes a closer look at the real cloud security risks in 2026. In this blog, we will explore the cloud security challenges and solutions, and guide you in selecting the right technology partner for cloud computing services to enhance its capabilities.
Let’s dive in!
Don’t wait to become part of that statistic. Build a secure cloud solution with Appinventiv today.
Understanding Cloud Security in 2026?
Let’s get one thing straight: the cloud isn’t inherently unsafe, but it’s also not automatically secure. The magic and the danger lie in how you configure and manage it. Let’s know in detail:
The truth is, the cloud itself isn’t inherently secure or insecure but it isn’t automatically secure either. Its strength and vulnerability both depend on how it’s configured, managed, and monitored. Let’s explore this in detail:
The Shared Responsibility Model: Who Does What?
If there’s one thing that companies still struggle with, it’s the shared responsibility model. Cloud providers cover the basics: data center security, physical infrastructure, and the backbone of the service. But what they don’t handle are the things inside your environment: your applications, your data, and your access policies.
With multicloud setups, serverless apps, and containers in the mix, security obligations are scattered across more layers. Missing even one layer, such as forgetting to secure a container registry, creates one of the most common cloud security risks and challenges businesses face today.
Here is how responsibilities shift between the provider and the customer across SaaS, PaaS, IaaS, and on-prem setups:
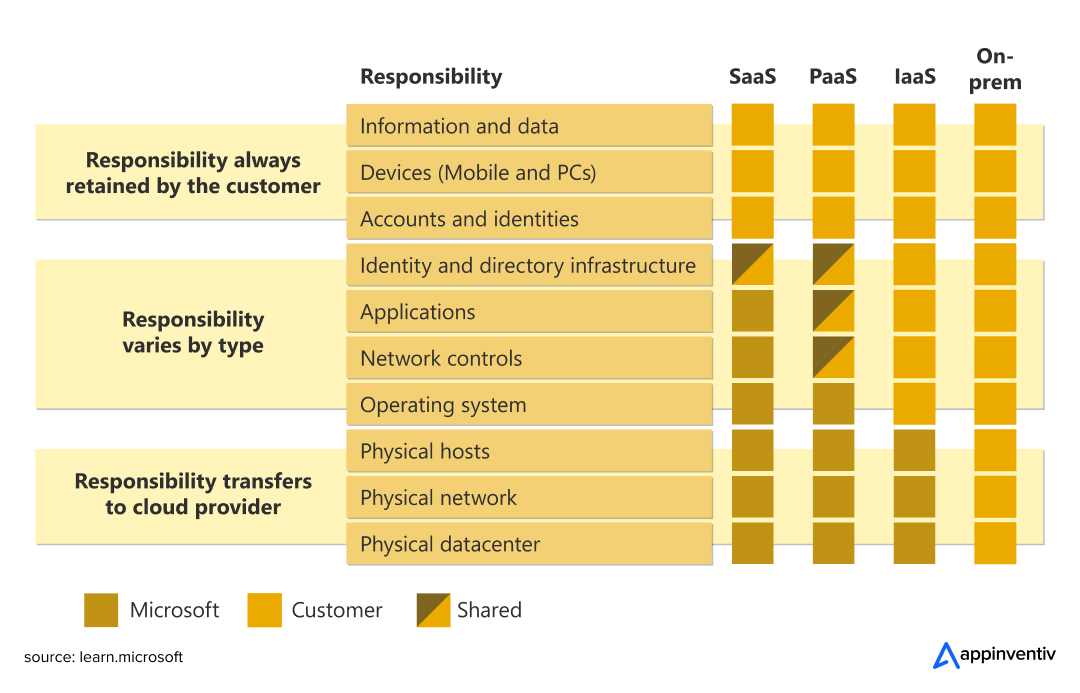
Here’s the breakdown of the cloud security responsibility model:
| Cloud Provider Responsibilities | Your Responsibilities |
|---|---|
| Physical infrastructure security | Data encryption and key management |
| Host operating system patching | Identity and access management (IAM) |
| Network controls | Application-level controls |
| Virtualization layer security | Operating system updates (for IaaS) |
The problem? Gartner projected that by 2025, 99% of cloud security failures would be the customer’s fault, not the provider’s, and this proved to be true, seeing the increasing number of data breaches worldwide. Most breaches happen because organizations mess up their side of the equation.
The Unique Challenges of Securing Cloud Environments
Cloud environments present security challenges that traditional on-premises setups never faced. Cloud systems aren’t like old-school IT, where you had a handful of servers running quietly in a rack.
- Workloads come and go in seconds. Think Kubernetes pods spinning up, disappearing, and leaving barely a trace.
- Shadow IT has become a real headache. Teams sign up for SaaS tools without approvals, and sensitive data slips outside official monitoring.
- Insider threats are still here. Sometimes malicious, but often just an employee making a small mistake that snowballs.
- Vendors and partners also play a part. Third-party vulnerabilities in APIs or libraries can open the door to attackers.
This is why cloud risk management isn’t just about firewalls or passwords. It’s about visibility, control, and having the right checks in place before something goes wrong.
The New Shape of Cloud Threats
Threat actors are increasingly targeting cloud environments due to the significant financial incentives they present.
- AI-driven tools are making attacks faster and more precise, from phishing to automated credential stuffing.
- Supply chain incidents are growing. If one vendor or library gets compromised, it can spread across dozens of companies.
- Ransomware is no longer only on local machines. Cloud computing services themselves are being abused to deliver ransomware-as-a-service.
- Advanced persistent threats (APTs) now quietly move through cloud identity systems, staying undetected for months.
That’s why doing a proper cloud computing security risk assessment isn’t a one-off task. It’s ongoing. Zero Trust security, continuous monitoring, and strong identity controls are the only way to stay ahead.
Also Read: AI in Cybersecurity: Automating Enterprise Security
Comprehensive List of Cloud Security Risks, and How to Mitigate Them?
The way businesses store, utilize, and exchange data is constantly changing, thanks to cloud computing and security. The amount of sensitive data that is possibly at risk is growing as a result of increased cloud usage globally. Let’s check out the potential top cloud security threats in 2025 and ways to mitigate them:
1. Data Breach
Few words strike more fear in board-level discussions than “breach.” The danger isn’t just that criminals steal information; it’s that they weaponize it. A leaked customer database can spark lawsuits, while exposed trade secrets can erode competitive advantage overnight.
The cloud adds complexity here: misconfigured storage, weak access policies, and shared environments give attackers more cracks to slip through. And once data is out, it rarely stays hidden. Identity records, health data, and even internal emails often reappear on underground forums, sold in bulk.
How to fix it?
- Encrypt everything: Treat data encryption not as an option but a baseline. Keep keys separate, and rotate them regularly.
- Layer authentication: Multi-factor authentication shuts the door on most credential theft attacks. Combine it with role-based access to shrink the blast radius.
- Monitor aggressively: Breaches rarely happen in silence. Continuous monitoring tools can flag unusual access patterns before the damage spreads.
2. Compliance Violations
Compliance isn’t just paperwork; it’s the difference between doing business and paying crippling fines. Regulations like GDPR in Europe, HIPAA in the U.S., and PCI-DSS for payments demand strict handling of sensitive information. The challenge is that cloud systems spread data across regions and services, sometimes without clear visibility.
A marketing team might spin up a new SaaS tool that stores customer data in the wrong jurisdiction, and suddenly, you’re non-compliant and facing penalties. Beyond the legal impact, public violations erode trust, and winning back customers can take years.
How to fix it?
- Bake compliance into workflows: Don’t bolt it on after launch. Define governance frameworks and assign accountability early.
- Segment sensitive workloads: Keep regulated data in controlled zones, with access tightly limited.
- Audit continuously: Annual reviews are no longer enough. Automated compliance checks reduce human oversight gaps.
3. Data Loss
A breach steals your data. A loss erases it. Both are painful, but loss can be permanent, and businesses often underestimate how fragile their data really is. Causes range from accidental deletions to expired cloud subscriptions, or even attackers wiping everything during a ransomware attack.
In industries like healthcare or finance, even brief outages can have cascading effects: delayed treatments, missed transactions, and broken customer trust. While the cloud is built for redundancy, poor planning can still leave critical files unrecoverable.
How to fix it?
- Don’t skip backups: Manual backups fail because humans forget. Automate the process, and store copies across regions or providers.
- Define recovery objectives: Know how quickly data must be restored (RTO) and how much loss you can tolerate (RPO).
- Harden access to backups: Attackers target backups, too. Keep them encrypted and separate from the main environment.
Also Read: How to Approach Data Loss Prevention (DLP)? Identifying the Best Practices
4. Expanding Attack Surface
What we call an environment’s overall vulnerability is called its attack surface. Every new workload, container, or API you add to the cloud broadens the attack surface. What looks like progress in development can quietly create dozens of new entry points for attackers. Businesses that adopt microservices or multi-cloud setups often discover their exposure only after an incident.
The danger isn’t just the number of endpoints; it’s that many remain invisible until exploited. A forgotten test environment left online, or an unused admin portal with default credentials, can be all an attacker needs to move inside.
How to fix it?
- Segment everything: Treat development, staging, and production as separate universes, each with its own policies.
- Apply least privilege consistently: Over-privileged accounts are the fastest way to expand risk. Only grant access for what’s needed and only for as long as it’s needed.
- Map the surface: Use attack surface management tools to continuously identify and monitor exposed assets.
5. Insecure APIs
APIs make cloud platforms flexible, but that openness also makes them tempting targets. Attackers don’t have to break into your network if they can exploit an API that’s poorly authenticated or overexposed. In fact, APIs have become the most common attack vector for enterprise web applications.
Hackers often target APIs using brute-force attacks, man-in-the-middle exploits, or denial-of-service attempts to gain unauthorized access or disrupt service. Your cloud security solutions must be able to tackle these three methods. Usually, the risk grows because APIs are often well-documented for developer ease, which also makes them easy for attackers to study.
How to fix it?
- Run red-team tests: To mitigate API security risks, you should simulate real attacks against your APIs to uncover blind spots.
- Secure by design: Require strong authentication, input validation, and throttling to block brute-force attempts.
- Monitor behavior: Logging and anomaly detection can reveal abuse patterns before they escalate into breaches.

6. Misconfiguration
Misconfiguration remains one of the most widespread cloud computing security risks. It’s rarely malicious; more often it’s a rushed setup, a missed default setting, or a permissions error. But the consequences are massive: open storage buckets, unsecured ports, or “allow all” firewall rules have exposed millions of records in recent years.
The complexity of multi-cloud environments makes human oversight even harder, increasing the odds of small but costly mistakes.
How to fix it?
- Automate compliance checks: Use tools that scan for misconfigured assets in real time.
- Adopt configuration baselines: Standardize how environments are set up to reduce inconsistency.
- Review regularly: Don’t wait for annual audits; schedule frequent reviews to catch mistakes early.
7. Limited Visibility of Cloud Usage
Moving to the cloud often means losing visibility into your own systems. Unlike on-premises environments, where logs and controls are centralized, cloud platforms scatter activity across services and regions. This lack of visibility creates blind spots.
You may not know who accessed sensitive data last week, or whether unusual activity is a misconfiguration or a breach. What is worse? Limited oversight slows down incident response. By the time anomalies are detected, damage may already be done.
How to fix it?
- Demand transparency: Choose a cloud computing security solutions provider who offers clear logging and reporting.
- Centralize monitoring: Use cloud security posture management (CSPM) to unify visibility across multiple platforms.
- Perform regular risk assessments: Build cloud risk management routines that identify gaps before attackers do.
8. Contract Breaches with Business Partners
Cloud security isn’t only about firewalls and passwords; contracts matter too. When employees store business files in personal cloud accounts, or when vendors hold more rights over data than you realized, confidentiality clauses can break down fast.
There are many cases where companies faced lawsuits simply because a third-party provider disclosed information under its own terms of service. In high-stakes industries like finance or healthcare, even a minor contractual gap can snowball into reputational damage and legal action.
How to fix it?
- Negotiate clarity up front: Spell out who owns the data, how it will be handled, and what happens at contract termination.
- Cover all scenarios: Include protections for insider misuse as well as external threats.
- Push for interoperability: If you switch vendors, your data should move securely and without disruption.
9. Account Hijacking
Hijacked accounts are one of the oldest tricks in the book and they still work. A single stolen credential can open the door to sensitive systems. The real danger is that, unlike malware, account takeovers can look like legitimate activity.
Attackers may spend weeks moving laterally, quietly escalating privileges, and harvesting information before anyone notices. In the cloud, where one login can unlock vast resources, the fallout is magnified. Also, unlike on-premises infrastructure, cloud environments sometimes provide different visibility into and control over security concerns.
How to fix it?
- Don’t rely on passwords alone: Layer MFA across all accounts, especially admin roles.
- Set strict role boundaries: Marketing doesn’t need access to finance, and finance doesn’t need engineering privileges. Be clear about it and restrict the boundaries.
- Plan for the worst: Ensure your provider has a continuity plan if major accounts are compromised.

10. DoS and DDoS Attacks
Not every cyberattack is about stealing data. Sometimes the goal is simply to knock you offline. A distributed denial-of-service (DDoS) flood can overwhelm cloud servers with junk traffic, leaving real users locked out.
For eCommerce sites or streaming platforms, minutes of downtime can mean millions lost. What makes DDoS especially nasty is attribution; sorting legitimate requests from malicious ones is complex, and attackers often use botnets spread across the globe.
How to fix it?
- Deploy intrusion detection systems (IDS): These tools flag unusual traffic spikes early.
- Use layered defenses: Firewalls that inspect traffic and block suspicious IPs help filter the noise.
- Build redundancy: Distributing workloads across regions reduces the impact of localized floods.
11. Insider Threats
Not every danger comes from anonymous hackers. Sometimes the problem is much closer, inside your own team. An insider threat could be a frustrated employee copying sensitive files before leaving, or just someone accidentally exposing a storage bucket.
Because insiders already have some level of access, their actions are harder to spot. The cost of insider mistakes is high: in one recent case, a single misstep exposed hundreds of millions of customer records because a storage bucket was left public.
How to fix it?
- Limit privileges: Nobody should have blanket access to everything. Split responsibilities so no one person can cause major damage.
- Keep training continuous: Remind staff that careless clicks or shortcuts can have big consequences.
- Monitor behavior: Unusual access patterns should raise alerts, even if they come from a trusted employee.
12. Shadow IT (Unmanaged Cloud Usage)
Shadow IT creeps in quietly. A marketing team signs up for a free SaaS tool, or an engineer spins up a test environment on their personal account. Nobody means harm, but suddenly sensitive data is flowing through systems the IT team doesn’t even know exist.
These hidden tools create blind spots, making compliance nearly impossible and giving attackers more doors to try. The bigger the company, the harder it becomes to spot, and by the time a breach is noticed, the trail can be messy.
How to fix it?
- Make the rules visible: Employees often bypass IT out of convenience, not malice. Clear guidelines help them know what’s acceptable.
- Use discovery tools: Track unsanctioned apps and bring them under management before they turn into risks.
- Educate staff: Show teams what happens when data leaves secure channels. Awareness cuts down accidental exposure.
13. Third-Party & Supply Chain Risks
Your cloud environment is only as strong as the weakest link in your supply chain. That link might be a vendor with outdated security, a SaaS app that over-collects data, or open-source code hiding vulnerabilities.
Attackers know this, which is why supply chain breaches have become headline events in recent years. The danger is amplified because when a trusted partner is compromised, the attack reaches you indirectlyoften bypassing your front-line defenses.
The Oracle Cloud breach is the biggest supply chain hack of 2025, which compromised 6 million records from over 140,000 tenants.
How to fix it?
- Vet vendors carefully: Certifications like ISO 27001 or SOC 2 aren’t just badges; they’re baselines. Partner with a cloud security solutions provider who owns these certifications.
- Demand transparency: Ask for a Software Bill of Materials (SBOM) so you know what’s inside third-party software.
- Monitor continuously: Vendor checks shouldn’t end at onboarding. Risks evolve, and your oversight should too.
14. Container & Infrastructure Vulnerabilities
Containers and Kubernetes have revolutionized how businesses deploy apps. They’re fast, scalable, and cost-effective, but they aren’t invincible. Insecure container images, unpatched Kubernetes dashboards, or attacks like Server-Side Request Forgery (SSRF) can give intruders a foothold.
Once inside, attackers often move laterally across workloads, quietly probing for more weaknesses. The pace of DevOps can make it tempting to skip checks, but in cloud environments, even one unscanned image can become a doorway.
How to fix it?
- Harden containers from the start: Stick to minimal base images, scan them before use, and patch them often.
- Monitor runtime behavior: Don’t just check code before deployment. Watch how containers behave once live.
- Segment workloads: If one container falls, isolation keeps attackers from spreading further.
15. OAuth & Third-Party App Risks
OAuth was designed to make logins easy. And it does. But convenience comes with hidden risks. Companies often grant third-party apps far more permissions than they truly need, or they forget to revoke tokens once apps are retired.
Those forgotten connections can become silent backdoors. Attackers don’t need to break into your systems if an abandoned app already has the keys.
How to fix it?
- Review permissions regularly: Audit OAuth scopes and strip back unnecessary access.
- Retire unused apps: Tokens that linger are time bombs. Remove them as soon as apps fall out of use.
- Vet before connecting: Don’t let every tool slip into your environment. Review third-party apps as carefully as you would a new hire.
Best Practices for Cloud Security and Beyond
Cloud adoption continues its steady expansion, and so as the associated security. The reality is that security has to be woven into daily operations; it can’t sit in a separate box. Below are practices companies should lean on in 2025 and beyond.
Adopting a Zero Trust Security Model
Zero Trust isn’t just a buzzword anymore. It basically means “don’t trust anything by default.” Even if a request comes from someone inside your company, it should still be checked.
- Every request is verified before access is given.
- Separate networks and workloads so one breach doesn’t spread everywhere.
- Keep access temporary; give it only when it’s needed and pull it back after.
Continuous Monitoring and Incident Response
In cloud systems, things happen fast. If you only check logs once in a while, you’ll miss the signs.
- Use tools that watch workloads, APIs, and containers in real time.
- Centralize your logs and feed them into monitoring systems like SIEM or CSPM.
- Have an incident plan ready, and practice it. Dry runs are awkward, but they save time in a real attack.
Regular Employee Training and Awareness Programs
Most of the time, breaches aren’t because of some genius hacker—they’re because of small mistakes. A wrong click, a weak password, an upload to the wrong bucket.
- Run short training sessions instead of long, boring ones.
- Test people with phishing simulations now and then.
- Keep it ongoing. Security awareness fades if it’s only once a year.
Automated Security Assessments and Audits
The cloud moves too quickly for manual reviews. If you rely only on humans, you’ll fall behind.
- Scan infrastructure-as-code before you deploy it.
- Automate compliance checks so GDPR or HIPAA reviews aren’t a last-minute scramble.
- Don’t skip penetration tests. Outside testers see what you can’t.
Strong Vendor Management and Supply Chain Security
Your security doesn’t just depend on you. It depends on every vendor and every bit of third-party software you bring in.
- Ask for certifications and proof of compliance before working with vendors.
- Monitor integrations closely instead of assuming they’re safe.
- Get a Software Bill of Materials (SBOM) so you know exactly what open-source code is in your stack.
Encryption and Key Management
Encryption is one of those things that sounds simple, but in practice, it’s easy to get wrong.
- Encrypt both data at rest and in transit. It should never sit unprotected.
- Rotate keys often and don’t leave them lying around in code or config files.
- Use secure vaults or HSMs for key storage, and when possible, manage your own keys instead of leaving them entirely to the provider.
Also Read: Cloud Application Security: Protecting Your Data in the Cloud
Let Appinventiv help you eliminate cloud security risks and challenges with solutions tailored to your business.
How to Choose the Right Cloud Security Partner
Selecting a cloud provider or security vendor has evolved far beyond routine procurement. With the stakes higher than ever, the wrong choice can introduce risks that no subsequent patch can resolve. The right cloud security partner should not only safeguard your infrastructure today but also ensure long-term resilience against emerging threats.
To build a truly secure cloud environment, you need a partner who understands both technology and accountability. Consider these key factors before making your choice:
Do they explain the shared responsibility model clearly?
Cloud security failures often begin with confusion. Who secures the physical servers? Who manages data encryption? If a provider can’t explain where their job ends and yours begins, you’ll likely discover the gap during a breach.
What certifications and compliance do they have?
Don’t just take their word for it. Look for proof: ISO 27001, SOC 2, PCI-DSS, or GDPR. These aren’t just logos on a website; they’re validation that the provider meets standards your industry regulators expect.
What tools do they offer for visibility and monitoring?
Security without visibility is like driving blind. Ask about Cloud Security Posture Management (CSPM), centralized logs, and real-time dashboards. Without these, even the most “secure cloud solution” can leave you blind to breaches until it’s too late.
How strong is their approach to identity and access?
Identity is the new firewall. If the vendor doesn’t enforce multi-factor authentication, allow fine-grained IAM, or provide secrets management, you’ll end up carrying the extra risk. Weak IAM is how most account hijacks begin.
What’s their roadmap for emerging threats?
Threats don’t stand still. AI-driven phishing, supply chain compromises, even post-quantum cryptography are evolving rapidly. Ask: What are the next-generation cloud security threats that businesses should prepare for? A serious partner should already be testing defenses against them.
What are their SLAs and breach protocols?
Here’s the question too many companies overlook. If a breach happens and history says it eventually will, how soon will they notify you? What accountability will they take? If their answers are vague, assume that response times will be too.
Partner with Appinventiv to Overcome Cloud Security Risks
For organizations seeking a reliable partner to strengthen their cloud security posture, Appinventiv offers proven expertise. We’ve partnered with global brands to design, implement, and safeguard cloud ecosystems that remain resilient amid today’s complex threat landscape.
Our team of 1600+ tech evangelists, including 50+ cloud experts, has deployed 2000+ secure cloud-based applications and handled 500+ cloud migration projects successfully, each tailored to meet the client’s unique regulatory, scalability, and risk management needs.
Unlike generic providers, we focus on building architectures that are resilient, compliant, and designed to tackle modern cloud security risks and challenges head-on.
Case Studies That Prove Our Cloud-Driven Expertise
- Y.K. Almoayyed & Sons: We helped modernize their retail and distribution platform by implementing scalable cloud solutions. The outcome? Streamlined operations, better data visibility, and a 32% cut in IT costs.
- Avatus: For Avatus, a secure avatar-based social networking platform, we designed a cloud-first architecture that ensured real-time scalability and user data privacy, critical for building trust in a privacy-sensitive market.
- TrackMyShuttle: Our team created a shuttle management app powered by cloud computing services. With real-time tracking and seamless ride coordination, the solution improved reliability for commuters and reduced operational bottlenecks.
- IKEA (Private Cloud ERP): For one of the world’s largest furniture retailers, we delivered a secure cloud-based ERP system. Using private IPs, each store operated independently while still collaborating seamlessly across the global network.
- Ility: We built Ility, a white-label SaaS platform for real estate management. The cloud-powered solution enabled property managers to optimize portfolios, automate processes, and lower costs.
Why Businesses Trust Appinventiv
- Security First: We begin every project with a cloud security risk assessment to identify vulnerabilities before rollout.
- End-to-End Ownership: From migration to monitoring, we provide cloud computing security solutions built for long-term resilience.
- Integration Ready: Our cloud solutions support all major integrations, reducing complexity while minimizing cloud computing security risks.
- Expertise at Scale: We’re official partners with AWS, Azure, Google Cloud, Oracle, and other leading cloud platforms.
- ISO-Certifications: We adhere to global standards such as ISO 27001, proving our commitment to information security management.
- Compliance Adherence: Whether it’s GDPR, HIPAA, or PCI-DSS, we ensure every solution aligns with industry regulations.
With Appinventiv, you don’t just migrate to the cloud; you gain a secure, scalable, and future-ready environment backed by proven case studies and real-world results. Partner with us to build a secure future on the cloud.
FAQs
Q. How can organizations ensure the security of their data when using cloud services?
A. Given its increasing prevalence, understanding the need for greater accountability in cloud usage is crucial. However, before making the switch, companies must think strategically about how they will use this technology and what they hope to accomplish.
By availing the latest cloud managed services, businesses can scale and adapt quickly, drive business agility, accelerate innovation, modernize operations, and cut expenses. This can not only help businesses get through the present crisis, but it can also result in more robust long-term growth.
Q. How to assess cloud security risks?
A. Here are some of the tips to assess cloud computing security risks:
- Identify new risks of cloud computing and perform regular risk assessments.
- Document and reevaluate any risks you decide to accept.
- Prioritize and implement security controls to reduce the risks you’ve found.
Q. What essential questions should I ask my cloud service provider regarding cloud security risks and measures?
A. While the questions can vary as per your requirements, use the following questions as a guide:
- What are specific data transmission encryptions, included in the cloud?
- Where are the servers physically located?
- Who can access the data in the cloud?
- What action will be taken in case of a security violation?
- How are GUIs and APIs protected?
- What level of technical support is available?
- What is my company’s role in data protection?
Q. What workload should I shift to the cloud?
A. You could move any workload to a cloud architecture. To meet all necessary regulatory compliances, you will need to pay particular attention to the implications of cloud migration and ensure that its architecture keeps your data secure. Get in touch with a reputed cyber security consulting firm to know more.
Q. What are the biggest cloud security risks in 2026?
A. The main risks include data breaches, misconfiguration, poor IAM (Identity and Access Management), insider threats, shadow IT, and third-party vulnerabilities. With attackers increasingly targeting APIs and containerized workloads, visibility and proactive monitoring have become critical.
Q. How to prevent data breaches in cloud environments?
A. Here are the most effective ways to prevent data breaches in cloud environments:
- Encrypt sensitive data in transit and at rest.
- Enforce multi-factor authentication (MFA).
- Regularly audit permissions and remove overprivileged accounts.
- Use cloud computing security solutions like Cloud Security Posture Management (CSPM) for real-time monitoring.
Q. What are the compliance risks with cloud data storage?
A. Compliance risks often involve storing data in the wrong region (violating GDPR or HIPAA), inadequate logging, or missing audit trails. Cloud security risk management practices, such as automated compliance checks and regular documentation reviews, can help avoid penalties.
Q. What are common cloud security mistakes?
A. Some of the most common mistakes for cloud computing security risk assessment include:
- Leaving cloud storage buckets public by default.
- Forgetting to revoke unused OAuth app permissions.
- Ignoring updates for container images and APIs.
- Assuming the provider alone is responsible for security, instead of following the shared responsibility model.
Q. How to manage identity and access in cloud systems?
A. Identity is often called the new security perimeter. To manage it effectively:
- Apply role-based access control (RBAC).
- Use MFA everywhere possible.
- Rotate secrets regularly and store them in secure vaults.
- Conduct periodic IAM audits as part of a cloud computing security risk assessment.
Q. What regulations apply to cloud security?
A. The key regulations for secure cloud solutions depend on industry and geography:
- GDPR (Europe) – data privacy and residency.
- HIPAA (US healthcare) – health data security.
- PCI-DSS – payment card security.
- CCPA (California) – consumer privacy.
Many providers also follow global standards such as ISO 27001 and SOC 2, which should be part of your vendor checklist.
Q. What are the next-generation cloud security threats that businesses should prepare for?
A. When building secure cloud solutions for the next generation, businesses should prepare for:
- AI-driven cyberattacks: Attackers use AI to automate phishing and craft malware that adapts faster than traditional defenses.
- Supply chain compromises: A single vendor with weak controls, or a poisoned software update, can spread trouble to every connected customer.
- Container and Kubernetes exploits: Misconfigured clusters or unscanned images give intruders a foothold, letting them move sideways across workloads.
- Post-quantum risks: Quantum computing will break current encryption; businesses must prepare now.
- Ransomware going after backups: Attackers now target backups and cloud storage directly to cripple recovery.
Q. What are the security risks of cloud computing?
A. The main cloud security risks show up in ways that are both common and costly:
- Misconfigured storage: An open bucket can expose millions of records.
- Weak IAM: Poorly managed accounts make hijacking simple.
- Insecure APIs: Endpoints without validation become easy entry doors.
- Shadow IT: Teams often use SaaS tools without approval, bypassing oversight.
- Insider slip-ups: Errors or malicious employees can expose or steal data.
- Vendor compromises: A breach in your supply chain can transfer risk to you.
This is why a cloud security risk assessment matters. It digs into IAM policies, API exposure, misconfigurations, and vendor trust, before those issues turn into public breaches.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

How Cloud Services Accelerate Product Development for Businesses
Key takeaways: Cloud product development changes the speed, cost, and risk profile of modern software delivery. The cost of cloud product development ranges between $40,000 and $400,000 or more. Cloud platforms give you instant access to AI/ML, edge computing, and advanced analytics without dropping tons of money upfront. Appinventiv supports enterprise cloud product development through…
Green Cloud - How Cloud Adoption Helps Improve Sustainability/ESG Goals of Enterprises
Key takeaways: Adopting green cloud solutions lowers energy consumption, cuts emissions, and reduces operational costs. Companies like UEM Edgenta and Bharti Airtel have seen measurable improvements in sustainability and efficiency. AI Enhances Green Cloud Efficiency. AI optimizes energy use, predicts demand, and minimizes waste in cloud infrastructure. Your Green Cloud Roadmap. Start with an infrastructure…

Cloud Migration Strategy for Enterprises in Australia: Benefits, Implementation Process and Tools
Key takeaways: Cloud migration in Australia is accelerating as enterprises modernize aging systems and prepare for AI-driven workloads. Local cloud regions in Sydney, Melbourne and Brisbane make compliance and performance far easier for large-scale migrations. A strong cloud migration strategy for enterprises in Australia depends on clear assessment, the right tools and ongoing optimization. Industry…