- The Reality of Cyber Threats Facing Australian Businesses Today
- What the 2023–2030 Australian Cyber Security Strategy Means for Businesses?
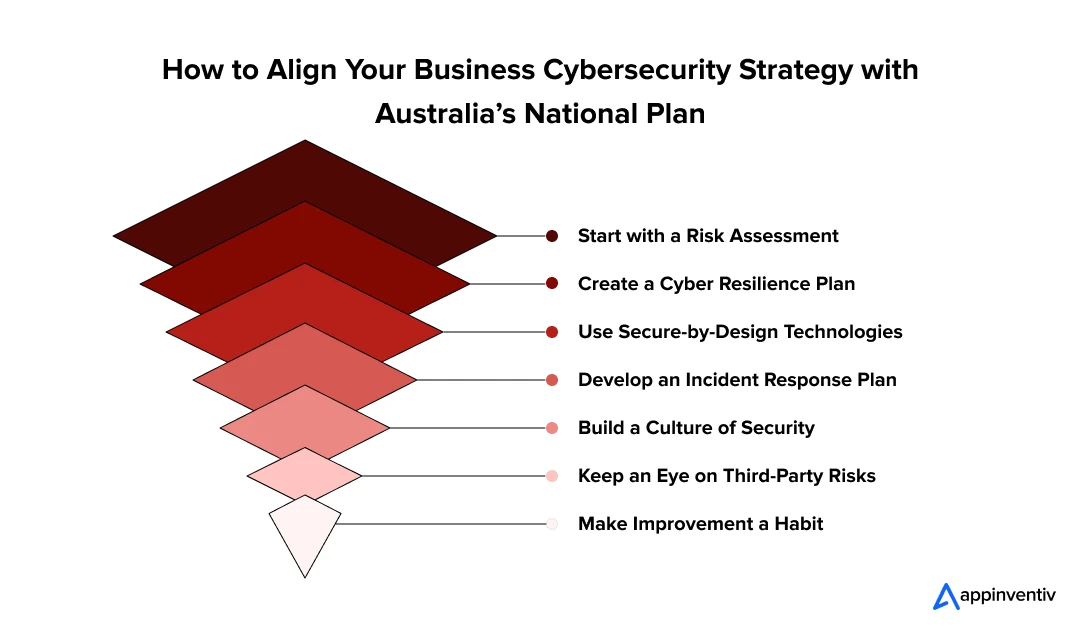
- What are the Key Steps to Build a Cybersecurity Strategy in Australia That Aligns with National Direction
- 1. Start with a Risk Assessment
- 2. Create a Cyber Resilience Plan
- 3. Use Secure-by-Design Technologies
- 4. Develop an Incident Response Plan
- 5. Build a Culture of Security
- 6. Keep an Eye on Third-Party Risks
- 7. Make Improvement a Habit
- Must-Have Cybersecurity Capabilities for Modern Australian Enterprises
- Advanced Threat Detection & Response
- Identity and Access Management (IAM)
- Data Protection & Encryption
- Ransomware Protection and Recovery
- Cloud and IoT Security
- Zero Trust Architecture
- Compliance Automation (Australian Privacy Act, SOCI Act)
- Vendor and Supply Chain Risk Management
- Don’t Leave Your Critical Infrastructure Vulnerable
- Why Work With Appinventiv for Building a Reliable Cybersecurity Strategy in Australia?
- Conclusion
- FAQs
- Q. How to develop a full-proof cybersecurity strategy for your Australian business?
- Q. What’s the importance of a cybersecurity strategy for Aussie businesses?
- Q. How much does cybersecurity implementation cost in Australia in 2025?
- Q. How to develop a cybersecurity plan for a business in Australia?
- Q. What are the top cybersecurity frameworks used in Australian enterprises?
- Q. Which cybersecurity certifications are preferred for Australian enterprises?
Key takeaways:
- For most Australian businesses today, cybersecurity has become as crucial as finance or operations; there is no separating it from the bigger picture.
- The national 2023–2030 strategy is a great backdrop, but real protection depends on how each company applies it to their own systems.
- Proactive businesses are focusing on fundamentals – risk reviews, real-world response plans, and tech that is secure from the ground up.
- Getting support from the right tech partner can take the stress out of compliance, make systems more secure, and keep your team completely focused on growth.
Cyber security for businesses in Australia is no longer just about ticking the compliance box. Today, it’s front and centre in boardrooms – and rightly so. Ransomware is getting nastier, phishing scams are more believable than ever, and insider threats? Let’s just say they’re no longer rare exceptions.
We’ve hit a turning point. Digital operations now run the show – handling customer data, powering supply chains, supporting remote teams. That also means one well-placed attack can lead to frozen systems, damaged reputations, that put you on the radar of Australian Privacy Act cybersecurity requirements.
To tackle this head-on, the government has rolled out its 2023–2030 Australian Cyber Security Strategy – an ambitious plan to make the country a pioneer in cyber resilience. It’s forward-looking, wide in scope, and pushes for stronger public-private collaboration. But let’s be clear: national direction can only go so far. It’s not a shortcut, and it certainly won’t secure your network for you.
That responsibility? It sits with CTOs, founders, and technology leaders like you.
This article is intended to look into the key aspects of the strategy for Australian businesses, the threats we’re all facing, and outlining practical ways to build a tailored cybersecurity strategy in Australia. Whether you’re setting the foundation or fine-tuning what’s already in place, now is the time to act.
Amidst it all, a strong cyber resilience strategy in Australia will not just come useful for protecting – it will give your business room to grow, adapt, and lead confidently in an increasingly volatile digital world.
Let’s talk about a roadmap tailored to your business.
The Reality of Cyber Threats Facing Australian Businesses Today
Let’s not sugar-coat it – Australia’s digital economy might be booming, but the cyber threat landscape is keeping pace. Fast.
In fact, it’s becoming clearer by the day that the cybersecurity challenges in Australia are more than just background noise. We’re seeing a wave of increasingly sophisticated attacks, often backed by organised crime groups or foreign entities. And no, they’re not just going after the big guys.
Here are some of the most common cyber threats businesses face today:
- Ransomware: Attacks have gone beyond simple encryption. Now, attackers are stealing your data, threatening to publish it, and charging you for both silence and access. In Australia alone, ransomware cases have surged – some estimates place the year-on-year rise at over 20%.
- Phishing scams: Still wildly effective. Whether it’s a fake invoice or a spoofed supplier email, employees are being manipulated into opening the wrong file or entering credentials where they shouldn’t.
- Malware and viruses: These aren’t your old-school viruses. Many are built to stay hidden, monitor activity, or quietly extract information for weeks before anyone notices.
- Insider threats: Sometimes it’s malicious. Other times it’s just a rushed employee clicking the wrong link. Either way, it’s a risk that’s real – and growing.
- Denial-of-Service (DoS) attacks: These aren’t just website take-downs anymore. They’re increasingly used to overwhelm internal systems and interrupt operations when you least expect it.
And this isn’t a theory. Think of the Optus, Medibank, and Latitude breaches – not just as headlines but as wake-up calls. These incidents exposed just how vulnerable organisations can be, especially those tied to critical infrastructure.
The government’s 2023–2030 Australian Cyber Security Strategy does respond to this, focusing on resilience at scale. But let’s be honest – legislation and frameworks take time. Businesses need to move now.
The real issue? Many organizations are stuck juggling too much: legacy systems that weren’t built with security in mind, rapid cloud adoption without proper risk assessment, and limited internal expertise to pull it all together.
Which is why simply “having cyber security” no longer cuts it. Not in 2025. Not with the stakes this high. What’s needed is an approach that’s part proactive, part adaptive, and fully embedded into your business. That means treating cyber security for business not as an IT function, but as a strategic layer that influences every process, every vendor decision, and every training session.
Because becoming cyber resilient isn’t about luck. It’s about preparation.
What the 2023–2030 Australian Cyber Security Strategy Means for Businesses?
If you’re running a business in Australia today, you’ve likely heard about the 2023–2030 Australian Cyber Security Strategy. What you may not know is just how much of it applies directly to your day-to-day operations.
At its core, the government’s plan is built around six interconnected “cyber shields”. Think of them as national defence layers designed to make Australia a tougher target for attackers – while encouraging businesses to lift their own guard.
Here’s a quick look at the ones most relevant to you:
- Strong businesses and citizens: This shield puts the spotlight on everyday business operations, digital hygiene, and making sure small and mid-sized enterprises aren’t left behind. It’s about building muscle where it counts – inside companies.
- Safe technology: Whether it’s IoT devices, software stack, or cloud infrastructure, the pillar concentrates on secure-by-design systems. In other words – bake in security from day one, not integrate it later.
- World-class threat sharing and blocking: Expect more real-time alerts and frameworks to report incidents without blame. The goal here is collective resilience – if one business is hit, the next one doesn’t have to be caught off guard.
Together, these three shields directly support the cyber resilience plan benefits that businesses are being urged to pursue. But the Strategy also sets a pace: not everything will roll out at once. Implementation is happening in three horizons, and Horizon 1 (2023–25) makes things real for business owners and CTOs. This phase focuses on strengthening foundational defences, plugging urgent security gaps, and protecting the most vulnerable – especially small businesses and critical infrastructure providers.
Here’s where it gets interesting. The government isn’t doing this in isolation. Instead, it’s actively inviting companies to co-design elements of cyber security Australia regulation. That means businesses may soon have a say in shaping rules around things like ransomware reporting or risk management frameworks – areas that have traditionally been top-down.
From a compliance perspective, expect updates to existing legislation. A few proposals of the Australia cyber security strategy on the table include:
- Setting mandatory secure-by-default standards for IoT devices
- Introducing no-fault ransomware reporting rules to improve visibility across the ecosystem
- Establishing a national Cyber Incident Review Board to gather insights and share learnings
- Updating the SOCI Act to clarify obligations for businesses handling critical infrastructure, especially around data storage and operational continuity
All of this forms part of what the government is calling a “new era of public-private co-leadership.” It sounds ambitious – and it is – but it also recognises a basic truth: the government can set the tone, but it’s the business sector that executes most of the cyber security strategy Australia needs.

So, what should businesses take away from this?
While the national strategy may seem like a policy roadmap, it actually contains key aspects of the strategy for Australian businesses – tools, obligations, and opportunities that can help shape your own path to cyber resilience.
It’s not about following along. It’s about using the momentum to build something that protects your organisation, supports compliance, and lets you focus on growth with confidence.
Because in today’s threat landscape, being prepared isn’t a competitive advantage anymore – it’s survival.
What are the Key Steps to Build a Cybersecurity Strategy in Australia That Aligns with National Direction
The government’s long-range plan gives a clear sense of where we’re headed as a country. But for business owners, CTOs, and tech leads, the real question is – what should we actually be doing right now?
Here’s a down-to-earth guide to help you build a cyber security strategy Australia can be proud of – one that works for your business, not just the headlines.
1. Start with a Risk Assessment
First things first: understand what’s at risk.
Creating cybersecurity measures for businesses does not just mean ticking off a compliance box. It’s about looking at your operations – your systems, your vendors, your data – and figuring out what you stand to lose if something goes wrong. Is your payroll system sitting on outdated infrastructure? Do vendors have access to sensitive client info?
If your business touches areas like healthcare, energy, or logistics, you may also fall under the critical infrastructure bucket – and that comes with responsibilities under the SOCI Act.
A good risk assessment in cybersecurity strategy Australia gives you a clearer view of weak spots, and helps you make smarter, faster decisions when it comes to budget, tools, and people. It’s also a crucial part of building a strong cyber security framework.
2. Create a Cyber Resilience Plan
Cybersecurity isn’t just about defence. It’s about bounce-back.
A solid cyber resilience strategy in Australia means knowing exactly what you’ll do when – not if – something goes sideways. That includes how you’ll keep the business running, how you’ll talk to clients or customers, and how fast you can recover your systems.
The real cyber resilience plan benefits show up in moments of chaos. Instead of scrambling, your team already knows what steps to take. You’ve already rehearsed it. You’re not figuring it out mid-crisis.
If you’re looking for practical steps to create a cybersecurity plan in Australia, this is where things start to take real shape.
3. Use Secure-by-Design Technologies
It’s tempting to take the “add-on” approach – build something fast, and worry about security later. But that mindset is how vulnerabilities pile up.
Secure-by-design means your apps, tools, and systems are built with protection in mind from day one. Not every platform you use will make this easy – but it should be a question you’re asking every time.
As the national plan puts more focus on “safe technology,” this is an area that will likely become non-negotiable down the line.
Following this approach helps shape a cybersecurity implementation roadmap, and it also gives you a strong cyber security strategy example you can use internally or with clients.
4. Develop an Incident Response Plan
This is your game plan for the worst-case scenario.
If you get hit with ransomware tomorrow, who do you call? What systems need to be shut down? Do your employees know who’s in charge during a breach?
A proper incident response plan Australia doesn’t need to be 100 pages long. It just needs to be clear, realistic, and something your team actually understands. Rehearse it. Update it. Make sure it reflects your current tech environment.
This step is central to cybersecurity best practices for businesses, no matter your size or industry.
5. Build a Culture of Security
Even the best firewall can’t stop someone from clicking a bad link in an email.
That’s where culture comes in. Cybersecurity awareness campaigns can go a long way – especially if they’re ongoing and tailored to your team. Phishing simulations, quick training sessions, internal reminders… these don’t just help reduce risk, they make security part of everyday thinking.
Board members and senior leadership should be part of this, too. Cybersecurity isn’t just an IT concern anymore. It’s now a boardroom issue – one that directly affects reputation and continuity.
If you’re thinking long term about the cybersecurity strategy for your Australian business, the cultural side is where you build staying power.
6. Keep an Eye on Third-Party Risks
Most businesses rely on vendors, SaaS platforms, and supply chain partners. But how many of those partners meet your own security standards?
If one of them gets breached, your data could be exposed too. That’s why third-party risk reviews aren’t optional anymore.
Build this into your onboarding process. Make sure contracts cover breach notification and basic security expectations. It’s a simple way to reinforce your overall cyber security strategy Australia.
7. Make Improvement a Habit
Cybersecurity is never “done.” The tech evolves. Threats evolve. So should your plan.
Regular audits keep things sharp – a process that entails reviewing access logs, testing backups, or having a third party run a penetration test.
Additionally, compare what you’re doing with the latest Australian cybersecurity frameworks and then use those benchmarks to modify your plans and see where you stand. What all of this filters down to is, staying up to date, which is critical for keeping up with cybersecurity compliances in Australia – and proving that your business takes security seriously.
We’ll help you go from audit to action with tools and frameworks that actually fit your business
Must-Have Cybersecurity Capabilities for Modern Australian Enterprises
It is a great first step to get the cybersecurity strategy for your Australian business sorted. But it’s the everyday capabilities, one that runs behind-the-scenes that actually keeps a business secure.
The challenge? Knowing what really matters. Let’s break down the practical stuff that modern businesses in Australia are investing in – not to tick boxes, but to stay ahead of threats and keep regulators off their backs.
Advanced Threat Detection & Response
It’s not enough to know something went wrong – you’ve got to catch it fast, and know exactly what went wrong.
Good detection tools do more than just raise red flags. They learn, adapt, and respond. It would be beneficial to plan for the integration of behavioural analytics, automated threat containment, and real-time visibility across your network. A setup of this sort will sit right at the base of cybersecurity best practices for businesses, especially if you’re running hybrid cloud or remote ops.
Identity and Access Management (IAM)
You wouldn’t give your front door key to every employee – your systems shouldn’t be any different.
With IAM, you can control who accesses what, reduce over-permissioning, and stop internal slip-ups from becoming full-blown breaches. You’ll also want to layer on MFA, role-based access, and regular reviews.
It’s a big part of strong compliance and risk management, and increasingly required for certifications and audits.
Data Protection & Encryption
Data is the lifeblood of most businesses, whether it’s customer info, pricing sheets, or IP – if that gets exposed, the fallout’s nasty.
Encryption protects both – data at rest and in motion and when you merge this with secure key management and backup policies, you tick off some core boxes under the Australian Privacy Act.
More importantly, you’re aligning with cybersecurity compliances in Australia before you get caught out.
Ransomware Protection and Recovery
It’s not a matter of if ransomware hits – just when.
Good protection is built on real-time monitoring, but the recovery piece cannot be ignored as well. Practices like offline backups, clear playbooks, and role-based response drills make the difference between a bad day and a full-blown disaster.
Having this in place will make compliance and risk management a smoother ride – especially during audits or breach disclosures.
Cloud and IoT Security
Cloud apps and smart devices keep business moving – but they can also widen your attack surface.
You’ll need policies and tools that monitor configuration changes, limit risky behaviours, and segment devices wherever possible. And IoT? Many devices are built for convenience, not security, so isolation matters.
These areas are now essential for cybersecurity best practices for businesses across industries – not just tech-heavy ones.
Also Read: Top 10 Cloud Security Risks and Ways to Tackle Them
Zero Trust Architecture
There is a new IT rule – trust nothing, verify everything.
Zero Trust means devices, users, and systems all have to prove themselves – every time. It’s not just for large enterprises anymore. Even lean startups are rolling this out to reduce internal spread in case of a breach.
That shift is now shaping the next-gen cyber security strategy Australia businesses are expected to follow.
Compliance Automation (Australian Privacy Act, SOCI Act)
Nobody enjoys paperwork, especially one that keeps piling up with every new policy regulation.
Automation of this means faster reporting, fewer mistakes, and a lighter load on your internal team. We suggest looking for tools that map your controls to frameworks like the SOCI Act or the Australian Privacy Act, and flag issues before regulators do.
This keeps you on track with cybersecurity compliances in Australia, without needing a full legal team on speed dial.
Also Read: The Role of DevOps in Compliance
Vendor and Supply Chain Risk Management
Your biggest risk might not come from inside your business. Third-party software, vendors, or service providers can create a scope for vulnerabilities to enter; making it critical to build a process for onboarding checks, regular reviews, and making sure your partners are meeting your standards.
In today’s threat-heavy landscape, this is a core pillar of compliance and risk management, especially for companies operating across finance, health, logistics, or government supply chains and manufacturing units.
Don’t Leave Your Critical Infrastructure Vulnerable
If you’re running a business in energy, telecom, healthcare, transport, or data hosting – you’re not just a service provider anymore. You’re part of Australia’s frontline defence.
With the government’s increased focus on protecting critical infrastructure, your cyber responsibilities have expanded too. The updated SOCI Act has been outlined with tougher expectations, including stricter protection of data storage systems, faster response to incidents, and even greater direct powers for federal authorities to intervene when needed.
This is not the compliance type which you can afford to treat as a one-off checklist. A single failure whether it’s because of outdated tech or an overlooked vendor can lead to a domino effect far beyond your own operations.
For businesses which fall under this umbrella of cybersecurity strategy in Australia, now is the time to reassess your security posture. That includes checking if your current controls meet all the modern standards, reviewing your incident response readiness, and making sure your team actually understands what to do during a breach incident.
And if you’re unsure about your legal exposure? Get advice. Whether it’s legal counsel or a cybersecurity advisory, it pays to be clear on where you stand.
Meeting the expectations set by the cybersecurity strategy in Australia isn’t just about reducing risk – it’s about earning trust and staying operational when it matters most. Because as digital regulation continues to evolve, keeping up with Australian Privacy Act cybersecurity requirements will only get more demanding.
Why Work With Appinventiv for Building a Reliable Cybersecurity Strategy in Australia?
Many businesses already know the risks, what they don’t always have is the right team to help turn their cybersecurity plans into something that actually works.
At Appinventiv, we focus on one primary element: building software that is secure from the inside out. Whether you are scaling cloud infrastructure, deploying customer-facing platforms, or modernizing your legacy systems, we help build safer digital products from day one.
Here’s how we support growing Australian businesses with our cybersecurity services:
Custom Security Strategies, Not Templates
Every business has its own mix of tools, platforms, and risks. That’s why we don’t push standard playbooks. Instead, we help you create a security approach that fits the way you work – no bloated systems or add-ons you’ll never use.
From Design to Deployment, We Build Security In
Cyber security for business is not only a feature, it should be made the hero element of the way your software is designed, written, and deployed.
From securing APIs and managing access layers to encrypting sensitive workflows, our team at Appinventiv Australia builds the controls your teams need – without slowing development velocity.
Compliance That Lives in Your Code
Meeting the demands of cybersecurity compliances in Australia – especially under the Australian Privacy Act cybersecurity requirements – can’t be an afterthought. We help you embed compliance into your architecture through features like audit trails, consent capture, secure logins, and proper data handling.
No manual checklists. Just smarter builds.
Staying Protected with Managed Security Services
Security doesn’t stop once a product goes live. Through our managed security services, we help businesses stay protected with monitoring setups, patching support, and real-time alerts that surface issues before they snowball.
Independent Security Architecture Review
Got systems already running? We’ll audit your current environment, find weak points, and suggest practical fixes – no long reports, just clear steps. This is especially useful when you’re preparing for scale or going after new certifications. A solid security architecture review can prevent costly redesigns later.
Building secure systems isn’t just about protection but also enabling growth without fear. That is exactly what we aim to deliver – clarity, speed, and a code you can trust.
If your team’s building something that needs to last, we are here to make sure it’s secure from the ground up.
Conclusion
Australia’s national cyber strategy is bold – and rightly so. But the truth is, no federal policy or six-point shield can protect your business unless you act on it from within.
The real work happens inside organizations: in the way systems are built, in how data is handled, and in whether risks are taken seriously before they become problems. Whether you’re running a fintech platform, managing health records, or overseeing logistics infrastructure, cybersecurity is now part of your core business model – not a side concern. And while the cybersecurity strategy in Australia sets an important direction, it’s up to individual businesses to close the gap between intention and action.
Start small if you need to. Prioritise risk assessments. Make compliance part of your software development lifecycle. And lean on partners who know how to turn frameworks into real, working systems.
Want help creating your cybersecurity roadmap? Let’s talk.
FAQs
Q. How to develop a full-proof cybersecurity strategy for your Australian business?
A. Start with a risk assessment, map your weak points, and then layer in defences based on what you actually use – cloud, mobile, APIs, etc. A strong cybersecurity strategy in Australia aligns with your systems, not just regulations. Work with partners who understand how to turn plans into software that defends your business in real time.
Q. What’s the importance of a cybersecurity strategy for Aussie businesses?
A. Cyber risks aren’t slowing down, and a weak link – anywhere – can stall operations or damage trust. A solid cybersecurity strategy for Australian businesses protects more than just data. It shows regulators, partners, and customers that your systems are built to handle the pressure, no matter how sudden.
Q. How much does cybersecurity implementation cost in Australia in 2025?
A. It varies. A basic cybersecurity plan for small businesses might cost a few thousand dollars. Larger companies managing sensitive data or subject to cybersecurity compliances in Australia – like the Australian Privacy Act – could be looking at much more. Cost depends on how complex your systems are and whether you build internally or use managed security services.
Q. How to develop a cybersecurity plan for a business in Australia?
A. Start with your critical data by identifying the weak points, and deciding your response plan for when things go wrong. Having a good cyber resilience strategy in Australia can include prevention, detection, and recovery. Lastly, use known Australian cybersecurity frameworks to stay aligned with industry expectations.
Q. What are the top cybersecurity frameworks used in Australian enterprises?
A. Many local businesses follow the Essential Eight, created by the ACSC. Others use ISO 27001 or NIST if they operate globally. For infrastructure-heavy sectors, aligning with the SOCI Act is becoming essential. The best approach for a cybersecurity strategy for Australian businesses? Blend what fits your size, risk, and budget.
Q. Which cybersecurity certifications are preferred for Australian enterprises?
A. ISO/IEC 27001 is generally the go-to for information security, also certificates like CISSP or CompTIA Security+ are also highly regarded in the industry. Businesses handling sensitive data or infrastructure should also track Australian Privacy Act cybersecurity requirements and ensure internal practices match evolving standards.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

Cybersecurity Risk Management - Strategy, Framework, Implementation Plan
Key takeaways: Digital transformation is rapidly increasing attack surfaces, rendering annual risk assessments obsolete in as little as 90 days. Effective cybersecurity risk management has to be treated just as any other business risk: with executive-level accountability and ongoing monitoring. Breaches involving third-party vendors exceed 60%, underscoring the need for end-to-end supply chain risk management.…

Healthcare Cybersecurity - Key Strategies and Best Practices to Protect Patient Data
Isn't it incredible how technology is revolutionizing patient care? It’s exciting and a bit daunting! The connection between healthcare and cybersecurity cannot be ignored in this digital age. As hospitals connect their systems, the risks amplify. Cyber threats in healthcare can put patient data at risk and disrupt life-saving treatments. We must tackle these challenges…

Cybersecurity in Manufacturing - Building Cyber Resilience for Smart Factories
It’s 2025. A glucometer manufacturing company is running through its hub of 15 smart manufacturing units across the globe. The brand is also connected digitally with a range of vendors and suppliers. One fine day, however, the test strip supplier gets hit by a cyberattack. The harmful code then enters the supplier’s system of record,…