- Strategic Intent: An Overview of the Enterprise Application Security Landscape
- Key Components of Enterprise Application Security
- Why Enterprise Application Security is Mission-Critical in Today’s Threat Landscape
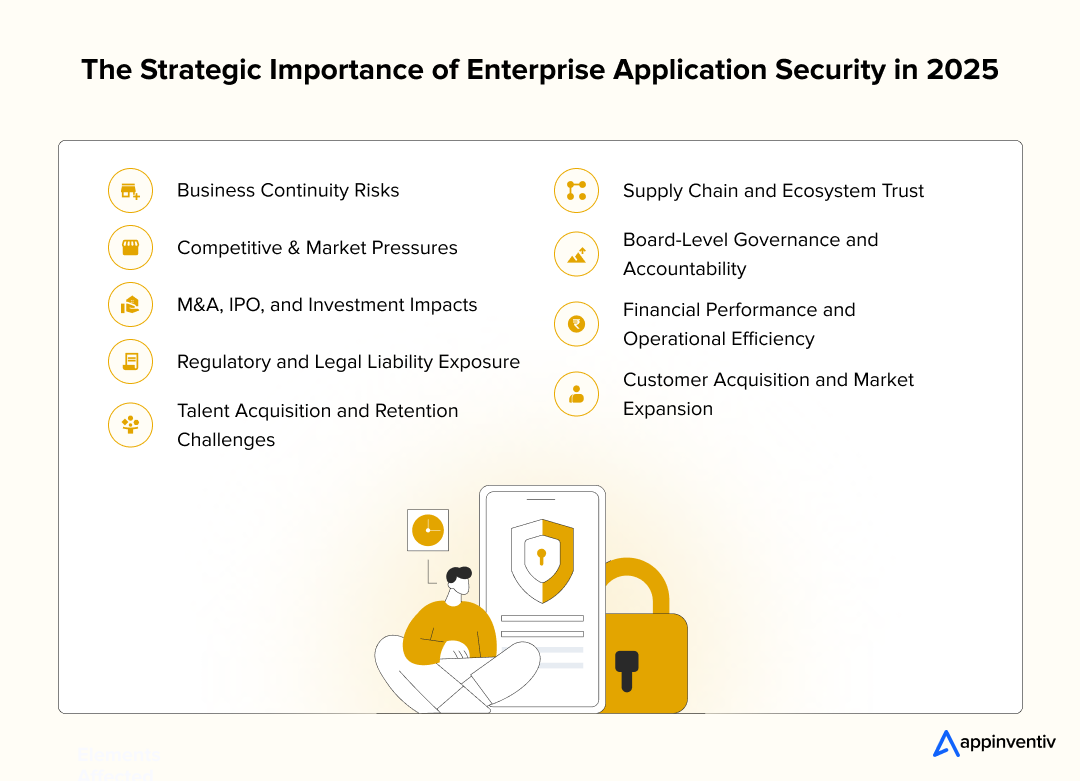
- Business Continuity Risks
- Competitive & Market Pressures
- M&A, IPO, and Investment Impacts
- Regulatory and Legal Liability Exposure
- Talent Acquisition and Retention Challenges
- Supply Chain and Ecosystem Trust
- Board-Level Governance and Accountability
- Financial Performance and Operational Efficiency
- Customer Acquisition and Market Expansion
- What is the Step-By-Step Process of Securing Enterprise Apps?
- Strategic Foundations or Best Practices for Strong Enterprise App Security
- Conduct Regular Security Training and Awareness Programs
- Implement Continuous Monitoring and Real-Time Threat Detection
- Establish Clear Security Policies Aligned With Business Objectives
- Ensure Secure Enterprise Application Integration
- Perform Regular Vulnerability Assessments and Penetration Testing
- Enterprise Application Security: Overcoming Critical Challenges in Modern Development Environments
- Scaling Security Across Distributed Development Teams
- Managing Security in Cloud-Native and Microservices Architectures
- Third-Party and Supply Chain Security Management
- Integrating Security into DevOps Without Slowing Development
- Future-Proof Your Enterprise Security with Appinventiv’s Expertise
- FAQs
Key takeaways:
- Enterprise applications are increasingly complex, spanning cloud-native architectures, APIs, and third-party integrations, which broadens the attack surface.
- Adopting DevSecOps and embedding security early in the development lifecycle reduces breach impacts by up to 30%, proving proactive security integration is vital.
- Regulatory compliance, business continuity, and customer trust hinge on effective application security strategies that include continuous monitoring and regular vulnerability assessments.
- Partnering with experienced providers like Appinventiv can help enterprises implement scalable, secure software development practices that protect data and accelerate growth.
The MOVEit breach of 2023 exposed the sensitive data of over 2,000 organizations, including major enterprises such as Ernst & Young and PwC, as well as hundreds of government agencies. What started as a vulnerability in a single file transfer application escalated into one of the largest supply chain attacks in history, affecting millions of individuals and costing organizations hundreds of millions of dollars in remediation efforts.
This isn’t an outlier—it’s the new reality. Enterprise applications face an unprecedented threat landscape where a single vulnerability can compromise entire business ecosystems. Your applications aren’t just software; they’re the backbone of your operations, the gateway to your data, and increasingly, the primary target for sophisticated attackers.
For CTOs, CIOs, CISOs, and other industry leaders, the question isn’t whether your applications will be targeted; it’s whether they’ll withstand the attack. The complexity of modern enterprise architectures, ranging from cloud-native microservices to API-driven integrations, has created an extensive and challenging attack surface to secure comprehensively.
This blog cuts through the noise to deliver actionable insights on building robust application security solutions. We’ll examine the current threat landscape, identify critical security gaps that plague enterprise environments, and provide a practical roadmap for implementing effective security measures.
Whether you’re securing a startup’s first enterprise contracts or hardening applications for a Fortune 500 company, the strategies outlined here will help you build security that enables, rather than hinders, business growth.
Protect your enterprise applications before it’s too late!
Strategic Intent: An Overview of the Enterprise Application Security Landscape
Enterprise applications have evolved into complex ecosystems that span multiple platforms, APIs, third-party integrations, microservices, and cloud-native backends. While these advancements enable greater agility and innovation, they also broaden the attack surface, exposing organizations to various risks.
APIs are commonly targeted for data exfiltration and injection attacks. Mobile apps often suffer from weak transport layer security. Cloud-native environments face misconfigurations and privilege escalations. Third-party libraries can introduce vulnerabilities from open-source components.
The stakes are high. According to Verizon’s 2025 Data Breach Investigations Report, there has been a 34% increase in attackers exploiting vulnerabilities to gain initial access and initiate security breaches compared to the previous year’s findings.
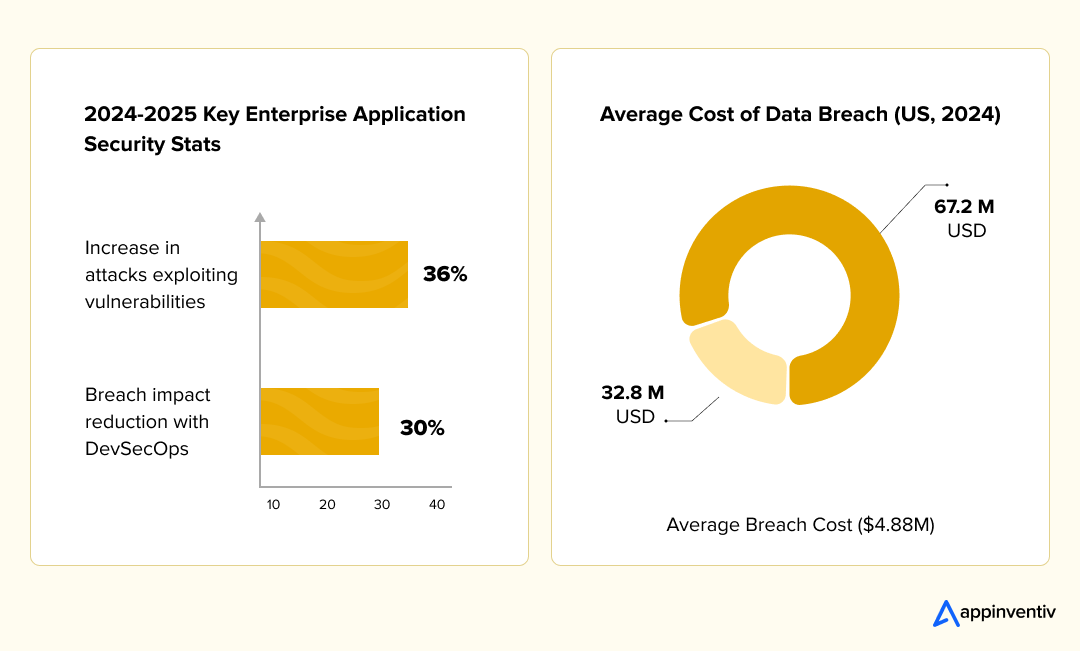
Also, IBM’s Cost of a Data Breach Report 2024 states that in the US alone, the average cost of a data breach reached $4.88 million last year. However, enterprises adopting DevSecOps practices saw a 30% reduction in breach impacts, underscoring the value of integrating security throughout the development lifecycle.
Beyond financial losses and operational disruptions, organizations must also contend with stringent regulatory frameworks, such as GDPR, CCPA, HIPAA, and PCI DSS. Failure to secure applications adequately can result in multi-million-dollar fines and legal challenges, making robust enterprise application security an essential business imperative.
Key Components of Enterprise Application Security
To build a strong defense against evolving cyber threats, enterprise application security must be comprehensive and multi-layered. It involves integrating security at every stage—from design and development to deployment and monitoring. Below are the essential components that form the backbone of an effective application security strategy.
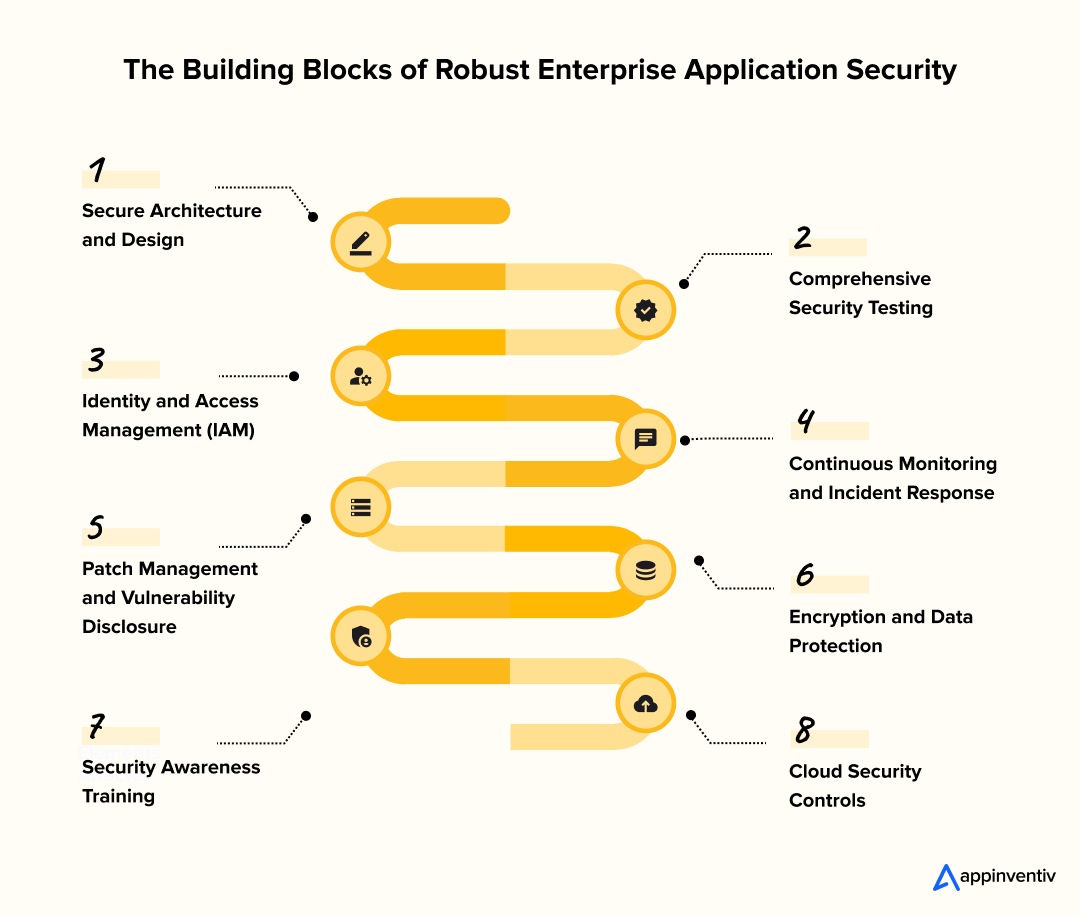
- Secure Architecture and Design: Security starts with a solid foundation. Designing applications with principles such as least privilege and defense in depth reduces the number of attack vectors. Conducting threat modeling and following secure enterprise software development standards early helps prevent vulnerabilities before they enter production.
- Comprehensive Security Testing: Continuous testing throughout the development lifecycle is crucial. Techniques such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST) help identify weaknesses in code, runtime behavior, and user interactions, ensuring issues are caught early.
- Identity and Access Management (IAM): Controlling access is a fundamental aspect of security. IAM enforces who can do what within applications through mechanisms like multi-factor authentication (MFA), single sign-on (SSO), and role-based access control (RBAC), significantly reducing the risk of unauthorized entry and insider threats.
- Continuous Monitoring and Incident Response: Threats can emerge at any time, making real-time monitoring essential. Solutions like Runtime Application Self-Protection (RASP), combined with Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms, enable the rapid detection and containment of security incidents.
- Patch Management and Vulnerability Disclosure: Regularly applying patches and updates addresses known vulnerabilities before they can be exploited. Additionally, maintaining a vulnerability disclosure program encourages ethical reporting, helping organizations stay ahead of emerging threats.
- Encryption and Data Protection: Protecting sensitive data in transit and at rest is a non-negotiable requirement. Using strong encryption protocols such as AES-256 for stored data and TLS 1.3 for network communications ensures data confidentiality and integrity against interception and tampering.
- Security Awareness Training: Human error remains a significant security risk. Providing ongoing education for developers, QA teams, and operations staff on secure coding practices and current threat landscapes empowers teams to write and maintain safer code, especially critical for enterprise web application security.
- Cloud Security Controls: Modern enterprise apps often rely on cloud infrastructure. Ensuring correct cloud configuration, continuous monitoring, and adherence to compliance standards prevents misconfigurations and unauthorized access, securing the backbone that supports your applications, including those accessed via enterprise mobile application security protocols.
Why Enterprise Application Security is Mission-Critical in Today’s Threat Landscape
Enterprise applications power core business operations and are prime targets for cyberattacks. As threats become increasingly sophisticated, robust application security is crucial for protecting data, ensuring continuity, and maintaining trust. Here are the reasons why enterprise application security is mission-critical.
Business Continuity Risks
Application security failures cascade beyond data breaches, costing organizations an average of $9,000 per minute in downtime (Sources: Forbes). When customer applications fail, sales halt, and satisfaction plummets, while internal system breaches disrupt payroll and financial reporting.
The decline of customer trust often inflicts greater long-term damage than the immediate financial losses it causes. For B2B organizations, enterprise application security breaches undermine confidence and expose operational weaknesses, signaling to buyers a lack of maturity and reliability.
As a result, robust security has become a crucial factor in vendor selection and the maintenance of sustained business partnerships.
Competitive & Market Pressures
Security has evolved from a compliance checkbox to a competitive differentiator in vendor selection processes. Enterprise buyers now conduct comprehensive technical evaluations during initial assessments, examining encryption standards and incident response procedures.
Strong enterprise app security postures win deals while weak security eliminates vendors regardless of product superiority. Security certifications like SOC 2 and ISO 27001 have become mandatory prerequisites for enterprise consideration.
M&A, IPO, and Investment Impacts
Security directly impacts business valuations, with poor practices reducing deal values by 10-15% or derailing transactions entirely. Investment firms routinely engage security assessment specialists during due diligence, requiring substantial improvements as closing conditions.
Companies pursuing IPOs face particular scrutiny. Security incidents can force delays and trigger regulatory oversight. Strong programs with a comprehensive application security strategy enhance valuations by demonstrating operational excellence and reducing buyer risk perceptions.
Regulatory and Legal Liability Exposure
Security failures increasingly expose executives to personal liability, with C-suite leaders facing potential criminal charges for negligent practices. GDPR fines have reached millions of dollars currently, while class-action lawsuits routinely seek hundreds of millions in damages.
Industry-specific penalties, such as those for failing to implement HIPAA compliance in healthcare and OCC enforcement in financial services, are becoming increasingly severe. Directors and officers insurance premiums have skyrocketed for companies with poor records of enterprise web application security, with some insurers refusing coverage entirely.
Talent Acquisition and Retention Challenges
Security maturity has become a key factor in attracting top engineering talent who view security practices as indicators of technical excellence. Companies with weak programs struggle to hire senior developers who are concerned about their professional reputation and career prospects.
Data security breaches create toxic environments, leading to increased turnover and hiring difficulties. Organizations that implement robust enterprise mobile application security attract premium talent, as employers who invest in proper tooling and professional development are sought after. This helps build a resilient workforce, enhance employee satisfaction, and prevent data breaches.
Supply Chain and Ecosystem Trust
Security practices are essential for maintaining partner relationships and ecosystem trust in interconnected business environments. Third-party vendors increasingly audit client security postures before integration, while customers demand security attestations for all connected systems.
Poor security practices can trigger contract terminations and partnership dissolutions, isolating organizations from valuable business networks. Organizations following enterprise application security best practices enable deeper integrations and expanded partnership opportunities, creating competitive advantages through enhanced ecosystem participation.
Board-Level Governance and Accountability
Security oversight has become a critical board responsibility, with directors facing increasing scrutiny over cybersecurity governance and risk management decisions. Boards now require regular security briefings, incident response simulations, and comprehensive risk assessments to fulfill their fiduciary duties.
Organizations without proper documentation and systematic approaches struggle to demonstrate due diligence during post-incident investigations. Implementing a comprehensive enterprise application security checklist enables boards to track security posture systematically and establish proper governance for stakeholders and regulators.
Financial Performance and Operational Efficiency
Security investments directly correlate with operational efficiency, as robust security frameworks reduce incident response costs and minimize business disruption. Organizations with mature security programs experience fewer security incidents and recover 3x faster when breaches occur.
Poor security practices result in hidden operational costs through constant firefighting, emergency patches, and compliance remediation efforts. Effective enterprise risk management for applications transforms security from a cost center into a business enabler that supports growth and operational excellence.
Customer Acquisition and Market Expansion
Enterprise customers are increasingly demanding transparency in security and proof of security maturity before signing contracts or expanding their relationships. RFP processes now include detailed security assessments, penetration testing results, and ongoing monitoring requirements as standard evaluation criteria.
Organizations with weak security postures find themselves locked out of high-value customer segments and growth markets. Understanding the importance of app security for enterprises enables organizations to position security as a competitive advantage, opening doors to premium customers and market opportunities previously inaccessible due to security concerns.
What is the Step-By-Step Process of Securing Enterprise Apps?
A structured and proactive approach ensures vulnerabilities are addressed before they can be exploited. Understanding the step-by-step process is essential for building a resilient security posture that supports organizational goals:
- Conduct Comprehensive Risk Assessment: Begin with a thorough evaluation of potential threats, regulatory requirements, and data sensitivity to shape your enterprise application security process. Understanding your specific risk landscape sets a strong foundation for security measures tailored to your environment.
- Adopt a Security-by-Design Approach: Incorporate security from the outset by leveraging threat modeling and defining clear security requirements. This forms a critical part of your overall application security strategy, ensuring vulnerabilities are minimized during design and development.
- Implement Robust Identity and Access Management (IAM): Control access rigorously with multi-factor authentication, single sign-on, and role-based permissions to protect sensitive enterprise assets. These controls are essential for maintaining strong enterprise web application security.
- Integrate Security Testing in CI/CD Pipelines: Embed static, dynamic, and interactive application security testing tools within your continuous integration and deployment workflows. This approach follows best practices outlined in an application security guide, enabling early and frequent detection of vulnerabilities.
- Ensure Secure Configuration and Secrets Management: Build robust cloud and infrastructure settings and safeguard credentials using vault solutions. These steps support secure enterprise software development by reducing risks related to misconfiguration and secret leakage.
- Deploy Runtime Protection and Continuous Monitoring: Utilize Runtime Application Self-Protection in conjunction with SIEM and SOAR platforms for real-time threat detection and response, thereby closing the gaps between development and operational security.
- Maintain Patch Management and Vulnerability Disclosure Programs: Establish disciplined patching cycles and encourage responsible vulnerability reporting to keep your applications resilient against emerging threats.
- Provide Ongoing Security Training and Awareness: Keep development and operations teams informed with regular training focused on secure coding and current threat trends, reinforcing a security-first culture.
- Regularly Review and Update Security Policies: Continuously adapt policies and controls to evolving technology and regulatory demands, ensuring sustained and effective protection.
Also Read: How Can Enterprises Protect Their Data in Cloud Environments?
Strategic Foundations or Best Practices for Strong Enterprise App Security
Building strong enterprise application security starts with a solid strategic foundation grounded in best practices. By prioritizing these fundamentals, businesses can effectively mitigate threats and safeguard critical assets. Let’s have a quick look at those.
Conduct Regular Security Training and Awareness Programs
To build a security-first culture, it is essential to provide ongoing security training to both development and security teams. This fosters a deep understanding of enterprise app security challenges and encourages proactive risk identification and mitigation. A well-informed team strengthens the overall application security strategy by aligning people with security goals and best practices.
Implement Continuous Monitoring and Real-Time Threat Detection
Effective enterprise web application security requires continuous systems monitoring to detect threats as they arise. Real-time detection tools help identify vulnerabilities and suspicious activities early, reducing the exposure window. Integrating these capabilities into your enterprise application integration security ensures rapid response and remediation of potential breaches.
Establish Clear Security Policies Aligned With Business Objectives
Developing and enforcing clear security policies is fundamental to a successful application security strategy. Policies should reflect both regulatory requirements and organizational goals, guiding teams on compliance and risk management. Well-defined policies enable consistent enterprise app security practices across all development and operational environments.
Ensure Secure Enterprise Application Integration
With the increasing reliance on third-party components and APIs, the security of enterprise application integration is critical. This involves validating and controlling interactions between integrated applications to prevent vulnerabilities from spreading. Proper integration security strengthens the overall enterprise application security posture by reducing attack surfaces.
Perform Regular Vulnerability Assessments and Penetration Testing
Proactive identification of security gaps through vulnerability scans and penetration testing is key to robust enterprise app security. These assessments simulate real-world attacks to uncover weaknesses before attackers do. Regular testing informs an adaptive application security strategy, enabling timely remediation and strengthening enterprise web application security defenses.
If you are looking to extend these principles beyond applications and into your overall security posture, our Top 10 Cybersecurity Measures for Businesses guide walks through the core controls every organization should have in place.
Future-proof your enterprise applications by leveraging Appinventiv’s proven security services.
Enterprise Application Security: Overcoming Critical Challenges in Modern Development Environments
Enterprise application security faces growing complexity due to cloud-native architectures, distributed teams, and fast-paced development cycles. Traditional security methods struggle to keep pace with these changes, requiring new approaches to protect dynamic environments without slowing innovation. Here are some of the key challenges of managing security gaps in enterprise applications and solutions, along with strategies to overcome them.
Scaling Security Across Distributed Development Teams
Distributed teams often lack consistent security practices, resulting in gaps and delayed responses. Without centralized oversight and real-time guidance, teams working across time zones and tech stacks accumulate security debt as they prioritize speed over compliance. These are common enterprise AppSec challenges that raise organizational risk.
Solution: Implement Security Champions embedded within each team to provide localized security expertise and guidance. Automate security gates within CI/CD pipelines to enforce consistent policies regardless of team location. Use a standardized application security guide with role-based training to keep all developers aligned with best practices.
Managing Security in Cloud-Native and Microservices Architectures
The proliferation of microservices vastly expands the attack surface, while dynamic, containerized environments outpace traditional security controls. Complex service-to-service communications and rapid scaling create blind spots, making perimeter defenses ineffective. Addressing these is a crucial part of the enterprise application security process.
Solution: Adopt service mesh architectures like Istio to enforce centralized security policies and encrypt inter-service traffic. Use runtime monitoring tools to detect anomalies in real time. Implement policy-as-code and Zero Trust networking to ensure consistent, identity-based access control across services.
Third-Party and Supply Chain Security Management
A heavy reliance on third-party components increases exposure to supply chain attacks, which is worsened by poor visibility and difficulty in tracking dependencies. Rapidly changing dependencies make timely vulnerability remediation challenging, exposing serious gaps in enterprise application security.
Solution: Generate Software Bill of Materials (SBOMs) to maintain detailed inventories of all components. Use automated dependency scanning tools for continuous vulnerability monitoring. Enforce vendor security assessments and rapid response protocols to reduce supply chain risks.
Also Read: Securing the Agent: How to Protect Your Business from AI-Powered Threats
Integrating Security into DevOps Without Slowing Development
Traditional security processes create friction in fast-paced DevOps environments, with slow tools and false positives leading to developer resistance and delayed releases. Security often becomes a bottleneck or an afterthought, a common hurdle in many application security guides.
Solution: Implement shift-left security by integrating fast, accurate SAST and DAST tools directly into development workflows. Use security-as-code frameworks to embed security controls into infrastructure and application code. Prioritize risk-based remediation to focus on high-impact issues while maintaining development velocity.
Future-Proof Your Enterprise Security with Appinventiv’s Expertise
Organizations that master application security don’t just protect themselves from threats—they unlock new markets, accelerate innovation cycles, and build unshakeable customer trust that translates directly into revenue growth and market leadership.
The future of enterprise application security demands a fundamental shift from reactive protection to proactive enablement. Tomorrow’s security leaders will leverage AI-driven threat intelligence to predict and prevent attacks before they materialize, deploy autonomous security systems that adapt more quickly than human-driven processes, and create security architectures that seamlessly scale across hybrid and multi-cloud environments.
At the forefront of this transformation stands Appinventiv, a pioneering enterprise software development services company that sets new industry standards for security excellence. Our track record with global enterprises, including IKEA, Adidas, Y.K. Almoayyed & Sons, and KFC, demonstrates our unique ability to deliver security solutions that not only meet compliance requirements but also accelerate business objectives.
By architecting security into the DNA of every application from conception to deployment, we eliminate the traditional trade-offs between security and agility, enabling our clients to move faster while reducing risk exposure.
Connect with our experts to start building a future-ready, resilient application security framework that protects your enterprise today and empowers your business growth tomorrow.
FAQs
Q. What is enterprise application security, and why is it critical for businesses?
A. Enterprise application security involves protecting software applications used by businesses from threats like data breaches, unauthorized access, and vulnerabilities. It is critical because these applications handle sensitive data and core operations, making them prime targets for cyberattacks. Effective security ensures business continuity, safeguards customer trust, and helps comply with regulations, ultimately minimizing financial loss and reputational damage.
Q. What are the common challenges in enterprise application security implementation?
A. Enterprise application security faces numerous challenges due to evolving tech and complex environments. Organizations must navigate these to protect their applications effectively. Common challenges include:
- Consistently scaling security across distributed teams
- Securing cloud-native and microservices architectures
- Managing third-party and supply chain risks
- Integrating security into fast DevOps workflows
- Handling legacy systems with weak controls
- Maintaining visibility across hybrid environments
- Ensuring adequate security training for staff
- Balancing compliance with development speed
Q. How to measure the ROI of enterprise application security?
A. Measuring the return on investment (ROI) for enterprise application security can be challenging, but it is essential to justify security budgets and demonstrate value. Here are the key ways to measure ROI:
- Tracking reduction in security incidents and breach-related expenses
- Assessing faster threat detection and response times
- Evaluating compliance with regulations to avoid penalties
- Calculating cost savings from automation and reduced manual effort
- Measuring impact on system uptime and business continuity
- Monitoring enhanced customer trust and brand reputation.
Q. How much does enterprise app security cost?
A. Enterprise application security costs vary significantly depending on company size, application complexity, and security needs. According to industry reports:
- Small to medium enterprises (SMEs) charge around $50,000 to $250,000 annually on security tools, personnel, and training.
- Larger enterprises often allocate between $1 million and $10 million+ per year, covering advanced security platforms, dedicated teams, continuous monitoring, and compliance efforts.
Additional factors such as cloud adoption, regulatory compliance (e.g., HIPAA, PCI DSS), and the use of third-party services can further influence costs. Ultimately, organizations should align security investments with their risk profile and business objectives for optimal ROI.
Q. What are the benefits of enterprise application security?
A. Enterprise application security comes with a series of benefits. These include:
- Protects sensitive business data and critical systems from cyber threats
- Reduces risk of costly data breaches and financial losses
- Ensures compliance with industry regulations and standards
- Safeguards customer trust and brand reputation
- Maintains business continuity by preventing downtime and service disruptions
- Enables early detection and remediation of vulnerabilities


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

Enterprise Risk Management Strategies for Complex Business Environments
Key Takeaways Enterprise risk management is shifting from periodic reporting toward continuous operational risk visibility. Integrated risk data improves decision speed, readiness for compliance, and overall business resilience. Governance alignment and data integration strengthen the effectiveness of enterprise risk management in complex environments. Industry-specific ERM approaches help address regulatory, operational, and technology-driven risk exposure. Structured…

Turning Legacy Data into Business Intelligence: A Food Chain’s Success Story
When you walk into a food outlet and place an order, it looks simple: swipe your card, grab your meal, and go. But behind every order lies a stream of valuable data. Now, imagine this happening across hundreds of stores spread across multiple countries, with each outlet running several POS (Point of Sale) systems. That’s…

Building a Robust Enterprise Data Strategy - Benefits, Use Cases, Process, Costs & Best Practices
Key takeaways: A solid enterprise data strategy removes silos, reduces costs, and restores confidence in decisions. AI initiatives only succeed when built on reliable, well-governed enterprise data foundations. Executives, employees, and customers gain through faster insights and personalized experiences. The roadmap starts with goal alignment, audits, future vision, and phased execution. Industries see measurable ROI:…