- What is Cloud Migration Security & Why Data Integrity Matters?
- Top Risks & Challenges to Data Quality During Cloud Migration
- Why You Must Integrate Security into Your Cloud Adoption Strategy
- What are the Key Security Considerations for Different Types of Cloud Migration?
- On-Prem → Cloud
- Cloud → Cloud
- Hybrid & Multi-Cloud
- What are the Different Cloud Migration Data Security Considerations for Pre-, During, and Post-Migration Stages?
- Pre-Migration - Establishing Control Before the First Byte Moves
- During Migration - Governing Execution in Real Time
- Post-Migration - Proving Integrity and Sustained Security
- Tools and Best Practices for Implementing Cloud Migration Security
- Core Practices for Integrity and Security
- Tools & Governance Mapping
- What Executives Should See: Model Integrity Dashboard
- Evaluating Cost–Risk Trade-Offs and ROI of Cloud Migration Security
- The Economics of Security Investment
- Must-Invest vs. Defer Decisions
- Executive Checklist & Migration Security Assessment (Ready-to-Use)
- How to Use the Assessment
- What the Checklist Covers.
- Interpreting Results
- What You Get
- How Appinventiv Helps Enterprises Execute Secure, Integrity-First Cloud Migrations
- Cloud Migration Services
- Cloud Security Services
- Cloud Consulting Services
- Recommended Immediate Actions
- FAQs
- Learn how to assess risks during migration, ensuring data integrity and compliance with global standards like GDPR and HIPAA.
- Secure your cloud transition by implementing encryption, checksum verification, and real-time validation to maintain data accuracy.
- Address issues like legacy data models, schema mismatches, downtime, and third-party toolchain risks that could threaten data integrity.
- Define roles clearly within your migration strategy, ensuring accountability for security at every stage, from pre-migration to post-cutover.
- Post-migration, establish continuous monitoring, ensuring logs are immutable and data residency rules are enforced for compliance and risk reduction.
A cloud data migration is never just an IT initiative. It is a moment that tests the organization’s ability to protect what matters most – its data, its reputation, and its regulatory standing. Every record that is transferred carries weight. If even a fraction is lost, corrupted, or exposed, the consequences cascade well beyond technology. Regulators investigate, customers lose confidence, and the board is forced to answer hard questions.
That is why data integrity during cloud migrations have to be treated as absolutes, not nice-to-haves. In practice, executives who weigh cloud migration best practices are doing far more than approving a technology roadmap – they are deciding how much trust the organization can place in its own systems. That trust spans across financial reporting, patient health records, customer identities, and even trade secrets that define competitiveness.
The choices made here – whether around cloud infrastructure security, encryption standards, or lines of accountability – carry consequences. Get them right and the move builds resilience; get them wrong and the migration can quietly create long-term, systemic risk.
This guide sets out the full picture: cloud migration governance models, and risk frameworks that align with global standards. It outlines how to run a thorough cloud migration data security assessment, where to apply data integrity checks, and what executives should expect from their teams and vendors. The goal is simple: to give leadership the insight and actions required to achieve a secure cloud transition strategy that preserves integrity, ensures compliance, and strengthens enterprise value.
What is Cloud Migration Security & Why Data Integrity Matters?
For executives, a cloud migration is less about “moving workloads” and more about redrawing the boundaries of trust. When infrastructure leaves the data center and enters the cloud, control shifts: contracts replace internal policies, shared-responsibility models replace clear ownership, and new risks appear in every gap.
The type of migration defines how wide those trust boundaries must extend. An on-prem to cloud migration places mission-critical records in an environment governed by a third party. A cloud-to-cloud data migration often ends up doubling the exposure, since now two providers have to keep their security controls aligned, and every hand-off needs to be checked rather than assumed.
With hybrid and multi-cloud models, the challenge shifts again – integrity isn’t only at risk while data is moving, it’s also stressed by the fact that information is scattered across platforms that rarely share the same standards for security or compliance.
What executives must recognize is that cloud migration data integrity and security is the single factor that keeps these shifting trust boundaries intact. Integrity is not simply “data accuracy”; it is the guarantee that information remains consistent and authoritative as it crosses domains. When integrity is weakened, reporting becomes unreliable, compliance certifications fail, and decisions lose their foundation.
A global insurer illustrates the point. During a database migration to cloud, encryption was handled flawlessly, but reconciliation was partial. Less than 2% of claims data failed to transfer, yet regulators classified it as a breach of fiduciary duty. The financial penalty was absorbed; the reputational hit led to loss of market confidence.
This is why data quality during cloud migration belongs on the board agenda. It is not about technology – it is about whether leadership can prove, to regulators and shareholders alike, that the enterprise still controls its most valuable asset: its data.
Top Risks & Challenges to Data Quality During Cloud Migration
Every cloud migration strategy carries technical uncertainty, but for executives, the real exposure lies in how that uncertainty translates into operational, regulatory, and reputational risk. The following risks should be treated as part of the board’s oversight, not left buried in technical reports.
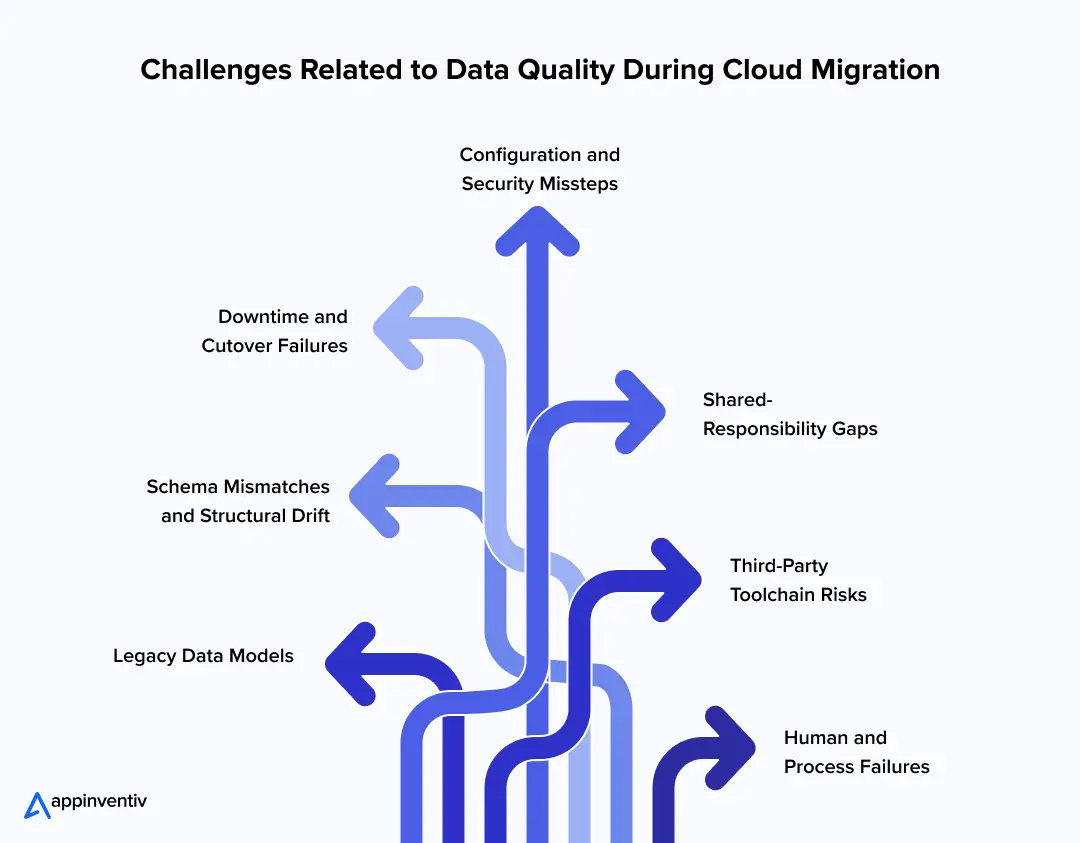
- Legacy data models
Outdated schemas often do not align with modern cloud platforms. Poor mapping leads to dropped fields, truncated records, or misinterpreted values. Impact: silent corruption that surfaces only in audits or financial close.
[Also Read: Transforming Legacy Systems with Cloud Migration: The Whys and Hows] - Schema mismatches and structural drift
When database objects evolve differently in source and target, reconciliation becomes unreliable. A minor naming conflict can cascade into systemic reporting errors. - Downtime and cutover failures
Even a well-planned cutover may overrun. For financial services, every hour of downtime risks missed trades or regulatory breaches. The ideal KPI for boards should be – Maximum acceptable downtime = 60 minutes per core system; anything longer triggers rollback. - Configuration and security missteps
Something as small as a misconfigured VPC, a wrongly scoped IAM role, or even an open storage bucket can open the door to unauthorized access – or in some cases break encryption while the data is moving. Issues like these show up again and again as the root cause behind cloud migration data security failures. - Shared-responsibility gaps
Providers secure the cloud; enterprises secure what is in it. During migration, blurred boundaries lead to unpatched gaps in encryption, logging, or monitoring. - Third-party toolchain risks
Many rely on external cloud data migration tools or integration platforms. If these lack robust validation or logging, undetected errors slip into production. - Human and process failures
Inadequate handoffs, unclear ownership, or fatigue during overnight cutovers are frequent causes of error. Governance lapses amplify technical risks.
For executives, the guiding principle is simple: assume risk materializes unless proven otherwise by integrity checks. A reasonable, tolerable data loss rate is 0.001% of records, but only if reconciliation can prove that the limit was never breached. Anything higher exposes the enterprise to reputational and compliance fallout.
Why You Must Integrate Security into Your Cloud Adoption Strategy
Every one of the cloud migration best practices comes with trade-offs, and the path you choose will shape the way security and governance have to be approached. Take rehost, replatform, refactor, or even replace – each carries a different profile. A lift-and-shift might feel quicker on the timeline, but it usually drags old vulnerabilities into the new environment.
A full refactor, on the other hand, is stronger for the long term, yet it can also create risks around schema drift or extended downtime. In reality, none of these options stands apart from governance: the strategy chosen is tightly bound to how the enterprise manages data integrity and regulatory compliance.
This is why governance cannot be treated as a parallel track. The migration path dictates the cloud security measures required, and those measures only succeed if roles and accountability are explicit. A clear model assigns ownership at multiple levels:
- The Data Owner defines what “integrity” means in measurable terms – such as reconciliation thresholds or acceptable error rates.
- The CISO ensures cloud infrastructure security, enforcing encryption, monitoring, and incident readiness.
- The CTO or CIO validates architecture and oversees toolchains for cloud data migration.
- The Compliance Lead ensures alignment with regulatory mandates, from GDPR to industry-specific standards.
Accountability on its own rarely gets the job done, meaning governance has to tie back to frameworks that boards, auditors, and regulators understand. In practice, mapping progress against the NIST Cybersecurity Framework, ISO/IEC 27001, or the Cloud Security Alliance (CSA) STAR program gives leadership a shared language for measuring risk maturity and before go-live, executives should insist on a cloud migration security assessment – scored across encryption, reconciliation, and access controls – so the organization’s risk posture is visible and defensible at the highest level.
The flow is deliberate: the migration strategy chosen shapes the risks faced; those risks demand a governance model with named accountability; and governance becomes credible only when tested against established frameworks. For executives, this connectivity is what ensures that a secure cloud transition strategy is not a slogan but a verifiable, board-monitored discipline.
What are the Key Security Considerations for Different Types of Cloud Migration?
Executives sometimes see cloud migration as a single, uniform problem, but in practice, the risks to security and integrity shift a lot depending on the route chosen. An on-prem to cloud migration means the enterprise is pushing data beyond its own perimeter for the first time, extending the circle of trust.
A cloud to cloud migration is different again: it forces two providers to synchronize controls, and even a tiny mismatch can snowball into systemic failure. And then in hybrid or multi-cloud models, the overlapping policies, data locations, and logging gaps pile complexity on top of complexity, making the exposure higher.
For boards, the real responsibility when answering, “What are the security considerations when migrating to the cloud?” is not to approve a generic plan but to insist on safeguards that reflect the migration type.
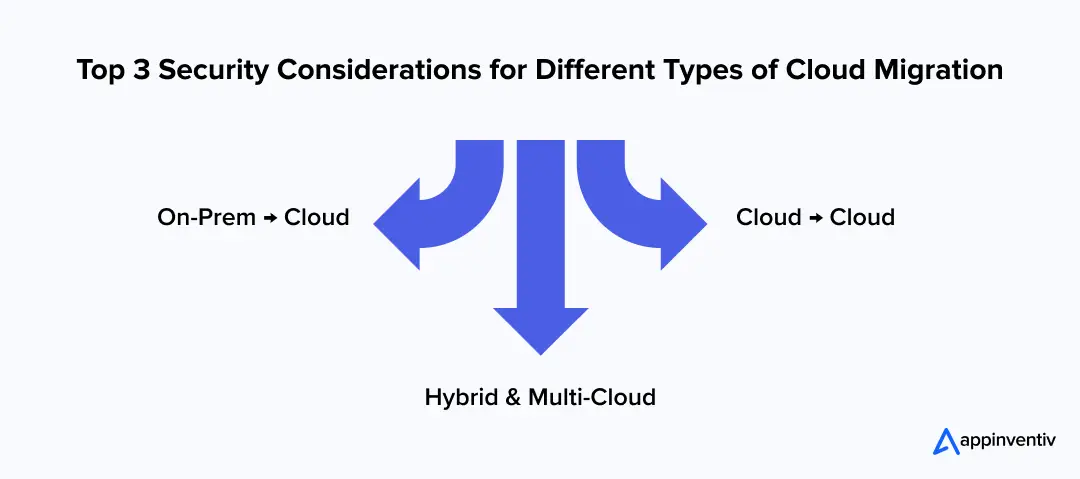
On-Prem → Cloud
Once data leaves private infrastructure, the enterprise gives up direct control and depends heavily on the provider’s assurances. That shift is not just technical – it changes the definition of responsibility. Encryption that isn’t applied consistently, sovereignty rules that get overlooked, or rollback plans that remain vague all create risks that don’t just vanish after cutover. In fact, they can resurface months later as regulatory penalties or reputational damage that the board will be forced to explain.
- Transfers must be encrypted end-to-end and validated with checksums.
- Large-scale syncs must account for bandwidth limits and “data gravity,” which can corrupt datasets if not managed carefully.
- Key management policies – who controls encryption keys, how rotations are handled – should be documented and contractually binding.
- The board should approve only when rollback criteria and sovereignty protections are written into provider contracts.
Cloud → Cloud
Switching between providers (AWS, Azure, GCP) is often motivated by cost, agility, or performance, but the risks multiply because two vendors share responsibility during the transfer. The technical challenge lies not only in moving data but in preserving its meaning – APIs may interpret metadata differently, IAM roles may not map one-to-one, and encryption policies can diverge without notice. For executives, the real danger is silent corruption: data appears intact until reconciliation fails weeks later, often under the scrutiny of auditors or regulators.
- Validate that APIs and metadata (tags, encryption scopes, compliance attributes) are preserved without alteration.
- Ensure least-privilege IAM is enforced across both providers; temporary access expansions must be revoked immediately after cutover.
- Require independent cloud migration data integrity and security checks during cloud migration, with documented evidence before sign-off.
- In one audit of a multinational bank’s database migration to cloud, checksum validation detected a 2.4% data loss that would otherwise have gone unnoticed, preventing regulatory fallout and reputational harm.
Hybrid & Multi-Cloud
Adopting more than one cloud can look like the safer choice because it spreads workloads and avoids over-dependence on a single provider. The promise is resilience and flexibility. The problem is, without strong governance, it quickly becomes the hardest model to secure. Each provider brings its own defaults, its own way of enforcing controls, and that fragments oversight. Accountability gets blurred. Logs may be missing in one environment, data can quietly drift into non-compliant regions, and network segmentation that looked solid in design becomes tangled once you stitch platforms together.
Boards often underestimate this complexity. A hybrid or multi-cloud setup may look like diversification on paper, but unless the enterprise pulls security posture and incident response together, it usually introduces more weak points than it closes. Every platform adds its own quirks – its own standards and blind spots – and unless executives demand consistency, the gaps multiply.
- Logging, monitoring, and observability need to be leveled across all providers. If one cloud lags, it creates a blind spot where breaches can hide.
- Data residency can’t be a one-off compliance tick box. It needs constant oversight, or sensitive records end up in the wrong geography, breaking sovereignty rules.
- Network segmentation has to be designed as one fabric. Piecemeal approaches, stitched cloud by cloud, create holes that attackers can exploit.
- Governance choices fall squarely on leadership: centralize posture management, or live with provider-specific controls. Either way, there must be a single, unified incident response protocol.
And across all migration models, single, multi, or hybrid – the same principle holds: cloud infrastructure security and data integrity during migration are not IT checklists. They are assurances at the board level. They must be demanded, independently verified, and documented as proof of due diligence for regulators, customers, and shareholders.
Also Read: Which Is the Best Cloud Solution for Your Business – Public, Private, Hybrid, or Multi-Cloud?
What are the Different Cloud Migration Data Security Considerations for Pre-, During, and Post-Migration Stages?
A cloud migration strategy is not simply a matter of moving workloads; it is an exercise in governance where leadership must control risk at three distinct stages. Treating these stages as “investment gates” ensures that decisions are made based on evidence rather than assumptions, and that accountability for integrity and security rests with the board as much as with the technology team.
Pre-Migration – Establishing Control Before the First Byte Moves
The preparation phase determines whether the migration begins from a position of strength or exposes the organization to unnecessary liabilities. Once systems are in motion, it becomes significantly harder to renegotiate SLAs, redefine tolerances, or enforce encryption policies. For this reason, executives should insist on evidence that the fundamentals of cloud infrastructure security and data integrity are in place before approving the first transfer.
- Data classification and risk assessment should not be generic. Leadership should expect a heat map that categorizes datasets by business criticality, regulatory exposure, and recovery time objectives. The critical question is: if the top three datasets were to fail mid-migration, what impact would it have on customers, regulators, and the balance sheet?
- Encryption ownership must be unambiguous. It is not enough to state that data will be “encrypted.” Boards should require documented key management policies that define escrow arrangements, key rotation frequency, and continuity of access in the event of provider failure. If the enterprise does not retain ultimate control of keys, it does not retain control of its data.
- Contracts and liability cannot remain buried in procurement appendices. SLAs should include measurable penalties for data loss, sovereignty breaches, or downtime that exceeds the organization’s defined thresholds. Without such terms, liability will inevitably revert to the enterprise.
- Rollback and continuity planning must be based on quantifiable triggers – such as more than 0.1% data integrity loss or 60 minutes of unplanned downtime. A continuity plan that merely promises “service resumption” is inadequate; leadership must see how mission-critical functions will continue during fallback.
Executive Output: A Migration Security Assessment, rated red/amber/green, where red signifies unacceptable risk and halts the migration until mitigated.
During Migration – Governing Execution in Real Time
The execution stage is where theoretical risks become operational realities. For executives, the role is not to monitor every command line but to demand transparency through real-time reporting. In a recent healthcare migration, for example, executives received live dashboards showing reconciliation error rates; a variance of 0.3% triggered rollback before corrupted patient records reached production. That single decision avoided not only operational chaos but also regulatory censure.
- Integrity checks must operate continuously. Every dataset should be validated through checksums or hash functions, with results logged in tamper-proof systems and escalated immediately if variance appears. Executives should demand daily reconciliation reports during the cutover.
- Large datasets require staged validation. Transferring terabytes without interim checks risks cascading corruption that may only be detected days later. By validating in blocks, the enterprise reduces the detection window from days to hours – or ideally, minutes. Boards should ask directly: What is our error detection window, and is it short enough to prevent material damage?
- Access privileges must remain temporary. Migration often necessitates elevated IAM roles, but these should expire automatically once the window closes. Standing privileges that persist post-migration are a long-term security liability.
- Operational KPIs must be reported with discipline. At a minimum, leadership should see metrics on transfer success rates (target >99.99%), reconciliation variance (target <0.1%), and downtime against agreed tolerances (target <60 minutes). These numbers should not be buried in technical logs but summarized in executive dashboards to help businesses make informed decisions.
Executive Output: Hourly or daily integrity dashboards shared with the CISO and CIO, with escalation protocols to bring the board into the decision loop in situations where the defined thresholds are breached.
Post-Migration – Proving Integrity and Sustained Security
Declaring success at the point of cutover is one of the most common mistakes in cloud adoption. For regulators, customers, and shareholders, what matters is not whether data “moved” but whether it remained intact, auditable, and compliant. This phase is where leadership must insist on proof, not promises.
- Reconciliation must be exhaustive. Record counts, checksums, and targeted audits should demonstrate at least 99.999% accuracy across migrated datasets. Anything lower is not a “minor issue” – it is a material event that may require disclosure.
- Audit trails must be immutable. Executives should require evidence that logs are tamper-proof, retained offsite, and stored for the full regulatory period – often seven years in financial services. A mutable log is no log at all.
- Compliance certifications must be renewed. Post-migration, regulators expect fresh evidence of compliance with ISO 27001, HIPAA, PCI DSS, or other relevant standards. The board should request the certificates themselves, not rely on verbal assurances.
- Drift monitoring must be established. Integrity and residency checks cannot end once migration concludes. Baseline metrics should be captured within 30 days of cutover, against which all future anomalies can be measured. Without this baseline, drift will remain invisible until regulators or customers detect it.
- SLAs must extend to data quality. Contracts should go further than uptime guarantees. They need to spell out remediation timelines and financial penalties when integrity checks fail, not just when systems go down. That way, both vendors and internal teams stay accountable long after the migration itself is declared “done.”
What executives should expect in return is a post-migration validation pack – signed off by the Data Owner, the CISO, and the Compliance Lead – that contains proof of reconciliation, evidence that encryption was consistently enforced, and documentation that regulatory obligations were met.
Tools and Best Practices for Implementing Cloud Migration Security
The technology stack chosen will determine whether a cloud data migration strengthens control or quietly erodes it. For leadership, the point isn’t to master every technical detail. It’s to understand which practices actually safeguard integrity, which tools make those practices reliable, and how governance needs to frame their use so that results can be verified at the board level.
The following principles represent cloud migration best practices proven to reduce risk, backed by tools that make them operational.
Core Practices for Integrity and Security
- Data validation before and after transfer
Establish baselines for record counts, referential integrity, and business rules before migration, then validate again after cutover. This ensures executives can sign off on accuracy with evidence, not assumptions. - ETL/ELT process discipline
Use standardized workflows to prevent silent errors when transforming or loading data. Poorly governed ETL pipelines often introduce more corruption than the migration itself. Boards should insist on versioned scripts and audit logs for every transformation. - Checksum and hash verification
Employ algorithms such as MD5 or SHA-256 to confirm that every record has arrived unchanged. These proofs should be independently verifiable, logged, and reported to leadership as part of integrity dashboards. - Schema version management
Incompatibility between source and target structures is a leading cause of integrity drift. Enforce schema versioning so that changes are controlled and traceable. Executives should request evidence that schema reconciliations have been reviewed by both data owners and compliance leads. - Orchestration and workflow governance
Anyone who’s been through a complex migration knows it’s not one clean transfer – it’s dozens of moving parts that have to line up. Tools like Apache Airflow or Control-M can help by automating those steps so people aren’t stuck running manual jobs at 2 a.m. But the real issue isn’t just automation; it’s whether the data migration process leaves behind a usable trail.That means workflows should be logged in one place, not scattered across teams, and access to change them has to be limited to the right roles. Otherwise, when something breaks later, no one can prove who touched what, and that’s where accountability falls apart. - Secure transfer channels
Whether data moves via SFTP, TLS-encrypted streams, or direct-connect links, the board must demand evidence that transport is both encrypted and monitored. For massive datasets, offline transfer appliances (e.g., Snowball) should be subject to chain-of-custody controls. - Key management and hardware security
Data encryption during migration sounds like an easy fix, but it fails the moment the keys aren’t managed properly. Keys that sit only with the provider, or rotations that happen without notice, basically strip the enterprise of control.Executives need to ask very direct questions here: Who actually holds the keys? How are they rotated? When was the last audit? Whether the answer is through hardware security modules (HSMs) or a cloud-native key management service, the important part is that ownership is spelled out and tested regularly. Otherwise, the encryption in place is more of a comfort blanket than a real safeguard.
Tools & Governance Mapping
| Tool Category | Purpose | Executive Risk Mitigation |
|---|---|---|
| Data validation tools (e.g., Talend, Informatica Data Quality) | Validate record counts, rules, and reconciliation pre-/post-migration | Proves to the board that integrity checks are evidence-based, not assumptions |
| ETL/ELT platforms (e.g., Fivetran, dbt, Informatica) | Standardize data transformations with logging | Prevents silent corruption; ensures auditability |
| Hash/checksum utilities (e.g., built-in md5, SHA-256, AWS S3 ETag) | Verify file and record-level consistency | Detects corruption immediately; provides cryptographic proof |
| Schema/version control (e.g., Liquibase, Flyway) | Manage schema changes across environments | Prevents mismatched structures that distort reports |
| Workflow orchestrators (e.g., Apache Airflow, Control-M) | Automate and log complex migration pipelines | Reduces human error; creates an auditable execution trail |
| Native cloud data migration tools (e.g., AWS DMS, Azure Database Migration Service, GCP Data Transfer) | Simplify database migration to cloud workloads | Accelerates migration while enforcing data encryption during migration and monitoring |
| Secure transfer options (e.g., TLS, VPN, Direct Connect, AWS Snowball) | Encrypt and monitor data-in-transit | Prevents exposure during movement; enforces sovereignty |
| Key management (HSM/KMS, e.g., AWS KMS, Azure Key Vault, Thales HSM) | Control encryption lifecycle | Ensures enterprise, not vendor, holds ultimate authority over access |
Best practices and tools should be seen not as “engineering preferences” but as controls with board-level implications. When leaders demand reconciliation evidence, cryptographic proofs, and auditable workflows, they transform migration from a technical project into a governance-driven assurance exercise.
What Executives Should See: Model Integrity Dashboard
Executives should not be buried in technical logs. What they need is a concise dashboard that tracks the integrity of the migration in real time and highlights whether thresholds are being met. The following model illustrates the minimum view a C-suite should expect:
| KPI | Target Threshold | Why It Matters for Executives |
|---|---|---|
| Transfer success rate | ≥ 99.99% | Ensures almost all data is moved without error; anything lower signals systemic risk. |
| Reconciliation variance | ≤ 0.1% | Quantifies the gap between source and target; beyond tolerance, rollback must be triggered. |
| Downtime vs SLA tolerance | ≤ 60 minutes for core systems | Defines business continuity expectations; executives see immediately if tolerances are breached. |
| Encryption verification | 100% of transfers logged as encrypted | Guarantees compliance and security considerations for a database migration are met; prevents regulator fines. |
| Schema drift events detected | 0 during cutover | Confirms structure consistency; prevents reporting failures post-migration. |
| Anomaly alerts resolved | All within 24 hours | Shows whether operational issues are managed proactively or allowed to linger. |
This executive-level view strips away technical noise and surfaces only the metrics tied to governance, risk, and compliance. Each KPI should be presented with red/amber/green status indicators, allowing the board to make rapid, informed decisions on whether to proceed, pause, or rollback.
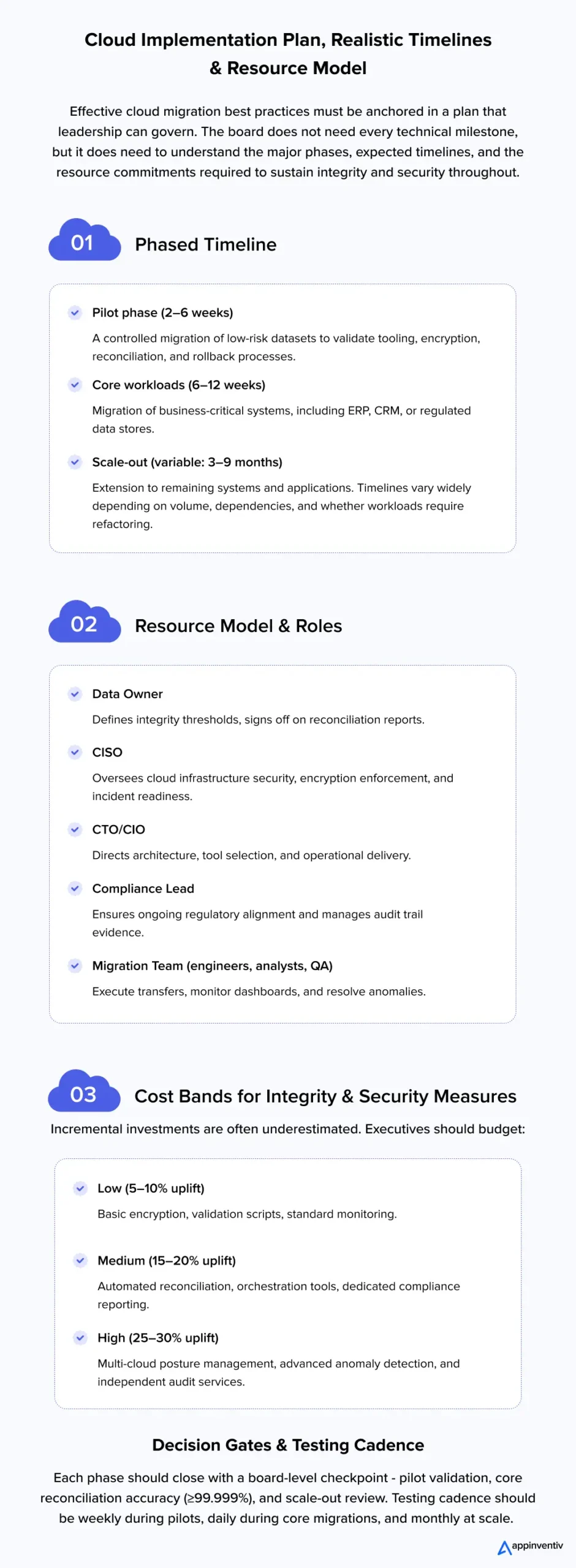
Evaluating Cost–Risk Trade-Offs and ROI of Cloud Migration Security
When boards review a cloud migration strategy, the discussion inevitably turns to cost. The issue is not whether to invest in safeguards, but how to weigh the additional spend on cloud security measures against the risk of operational, regulatory, or reputational losses.
The Economics of Security Investment
Incremental spend of 15–20% on integrity and security controls – automated reconciliation, real-time anomaly detection, and independent audit tooling – can avert incidents that routinely cost multiples of that amount.
- Downtime: In financial services, one hour of outage can cost $6–10 million in missed trades.
- Regulatory fines: GDPR and HIPAA violations for data integrity during cloud migrations often exceed $5 million, excluding remediation.
- Reputation loss: A single public failure may reduce market capitalization by 5–10%, dwarfing any upfront investment.
Must-Invest vs. Defer Decisions
- Must Invest: Controls tied directly to compliance (encryption, reconciliation, immutable audit trails) are non-negotiable. They protect the organization’s license to operate.
- Defer if Needed: Advanced enhancements – such as multi-cloud posture management or external continuous audits – can be staged if budgets are tight, but only with explicit board sign-off on the residual risk.
ROI on security is not speculative. Every additional dollar invested in proven integrity controls reduces exposure to losses that can be 10 to 20 times greater. The real governance failure is not overspending, but underestimating the cost of a breach or outage.
Also Read: How to evaluate the ROI and cost-benefit of cloud migration
Executive Checklist & Migration Security Assessment (Ready-to-Use)
Oversight of a cloud migration strategy cannot rely on informal updates or vague assurances. Executives need a structured way to measure readiness, identify red flags, and decide whether to proceed, pause, or remediate. The Migration Security Assessment is designed for exactly this purpose.
How to Use the Assessment
- Assign responsibility: The CISO, CIO, Data Owner, and Compliance Lead should complete the checklist together.
- Score each question 0–5:
- 0 = no evidence or action taken
- 3 = partial implementation, incomplete evidence
- 5 = fully implemented and verified with documentation
- Review with the board: Present results as averages and identify any “red flag” scores (0–2).
- Decide next steps: Use the scoring ranges below to determine whether to approve, pause, or remediate.
What the Checklist Covers.
Fifteen core governance questions span classification, encryption, reconciliation, downtime tolerance, compliance certification, and drift monitoring. Together, they test whether data integrity during cloud migrations and cloud security measures are fully in place.
Interpreting Results
- Score 4.5–5.0 (Green): Migration is ready to proceed. Evidence shows controls are mature and risks are managed.
- Score 3.5–4.4 (Amber): Migration may proceed for non-critical systems, but remediation is required before core workloads are moved. The board should demand timelines for closure.
- Score 0–3.4 (Red): Migration must not proceed. Critical gaps exist (e.g., encryption ownership unclear, reconciliation unproven). The board should halt until controls are verified.
What You Get
A one-page governance report that:
- Demonstrates to regulators that the board exercised active oversight.
- Provides executives with a clear yes/no decision gate.
- Ensures that security and integrity are evidenced, not assumed.
Download the Migration Security Assessment Template – a ready-to-use scorecard with built-in maturity ratings, red/amber/green indicators, and board decision guidance. It turns these questions into a practical tool for your leadership team.
How Appinventiv Helps Enterprises Execute Secure, Integrity-First Cloud Migrations
Enterprises do not measure success in cloud adoption by how quickly systems move, but by whether integrity, compliance, and resilience are preserved. Appinventiv has delivered cloud migration services and cloud security services for organizations operating under some of the strictest regulatory regimes worldwide – including finance, healthcare, and manufacturing – where a single integrity failure could trigger millions in fines and lasting reputational damage.
Cloud Migration Services
Our migration programs are built around audit-ready integrity controls. In a recent engagement with a global financial institution, our reconciliation framework achieved >99.999% data accuracy during the transition of critical transaction systems. We implement staged pilots, reconciliation dashboards, and rollback triggers so that boards receive evidence, not assumptions, at every phase.
Cloud Security Services
We design cloud migration data integrity and security into the migration lifecycle in alignment with NIST Cybersecurity Framework, ISO 27001, and CSA STAR standards. Our teams have reduced downtime windows by up to 40% for healthcare providers by enforcing IAM hardening, real-time anomaly detection, and automated compliance monitoring. Every engagement concludes with a cloud migration security assessment, producing red/amber/green scoring that auditors and regulators can validate.
Cloud Consulting Services
Appinventiv’s advisory practice guides leadership through the strategic choices – rehost, replatform, refactor, or replace – by mapping them to risk, cost, and compliance exposure. For a multinational manufacturer, our governance model aligned board oversight to GDPR and HIPAA obligations while reducing migration costs by 18% through phased workload prioritization.
Our approach towards cloud consulting services is not theoretical. It is evidenced by cross-sector results, anchored in global security frameworks, and validated through independent compliance certifications. By working with us, your board can gain the ability to demonstrate, with documentation and metrics, that their cloud adoption strategy was secure, compliant, and integrity-first.
Recommended Immediate Actions
Cloud migration decisions carry consequences that extend far beyond IT. They touch compliance obligations, customer trust, and enterprise resilience. Executives cannot afford to treat cloud migration data integrity and security as technical details – they are board-level responsibilities that must be evidenced and enforced.
Three actions to take this week:
- Appoint an executive migration sponsor with clear authority to oversee governance and report directly to the board.
- Commission a Security & Integrity Readiness Report that covers data classification, encryption ownership, rollback criteria, and continuity planning.
- Review vendor SLAs and liability clauses to confirm penalties, residency guarantees, and audit requirements are enforceable.
Next Step: Initiate a tailored Security & Integrity Audit with us. It provides a board-ready scorecard, identifies governance gaps, and delivers a roadmap for executing compliant and integrity-first secure cloud transition strategies.
FAQs
Q. How to ensure data integrity during cloud migration?
A. It’s more like layers. First, you clean the data before moving, then you run checksums or hash verifications while it’s moving, and after the cutover, you reconcile record counts. Think of it as pre, during, and post. If you skip any of those steps, you’ll never really know if something got lost in transit.
Q. What are the best practices for cloud migration data security?
A. A couple of things stand out. Encrypt everything (in-flight and at-rest), limit access with strict IAM, run pilots before you go big, and make sure there’s a rollback plan in case something breaks. Oh, and don’t forget to log everything – immutable logs save you later when auditors come knocking.
Q. What are the risks to data integrity in cloud migration?
A. Biggest one? Silent corruption. Like schema mismatches, where numbers look fine but are actually wrong. Downtime, failed cutovers, misconfigured buckets, third-party tools that don’t log properly – all classic traps. If you don’t define accountability (who signs off on what), stuff slips through the cracks.
Q. How to secure data during cloud migration?
A. Encrypt transfers, yeah, but also check that encryption actually worked. Split big datasets into smaller chunks so you can validate mid-way, not just at the end. Use direct connect or TLS tunnels, and avoid the open internet where possible. And keep elevated privileges temporary… migrations are famous for leaving behind orphaned admin rights.
Q. What is the cloud migration data security checklist?
A. It’s a long one, important ones being: classify data, define rollback triggers, enforce end-to-end encryption, validate with checksums, monitor replication in real time, lock down IAM roles, and then reconcile post-cutover. If any one of those is missing, you’re taking chances.
Q. How to validate data integrity after cloud migration?
A. Run record counts, checksums, and then… don’t just stop there. Do business-level validation. Can finance still close the books properly? Can CRM still pull the right customer history? Numbers matching doesn’t always mean the data still works.
Q. How to comply with regulations during cloud migration?
A. Start early. Map which data is regulated (GDPR, HIPAA, PCI, whatever) before you even move it. Make sure residency is honored – where data sits matters. And keep all audit logs immutable. Regulators care less about “we tried” and more about “show me the evidence.”
Q. What are the benefits of securing cloud migration?
A. Peace of mind, really. You avoid downtime fines, regulator penalties, and angry customers. Plus, once you bake security in, the board and auditors stop breathing down your neck because you can actually prove control. And it just makes the cloud move smoother… less firefighting later.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

How Cloud Services Accelerate Product Development for Businesses
Key takeaways: Cloud product development changes the speed, cost, and risk profile of modern software delivery. The cost of cloud product development ranges between $40,000 and $400,000 or more. Cloud platforms give you instant access to AI/ML, edge computing, and advanced analytics without dropping tons of money upfront. Appinventiv supports enterprise cloud product development through…
Green Cloud - How Cloud Adoption Helps Improve Sustainability/ESG Goals of Enterprises
Key takeaways: Adopting green cloud solutions lowers energy consumption, cuts emissions, and reduces operational costs. Companies like UEM Edgenta and Bharti Airtel have seen measurable improvements in sustainability and efficiency. AI Enhances Green Cloud Efficiency. AI optimizes energy use, predicts demand, and minimizes waste in cloud infrastructure. Your Green Cloud Roadmap. Start with an infrastructure…

Cloud Migration Strategy for Enterprises in Australia: Benefits, Implementation Process and Tools
Key takeaways: Cloud migration in Australia is accelerating as enterprises modernize aging systems and prepare for AI-driven workloads. Local cloud regions in Sydney, Melbourne and Brisbane make compliance and performance far easier for large-scale migrations. A strong cloud migration strategy for enterprises in Australia depends on clear assessment, the right tools and ongoing optimization. Industry…