- What Is Included in Enterprise AWS Managed Services?
- AWS Shared Responsibility Model in Managed Services
- Key Challenges German Enterprises Face in AWS Managed Services Adoption
- Why German Enterprises Are Re-Evaluating AWS Cloud Operations
- Why This Decision Cannot Be Deferred in Germany
- Compliance Requirements for AWS Managed Services in Germany
- BSI C5: Operationalizing Cloud Security Controls
- GDPR: Data Protection in Daily Cloud Operations
- NIS2 and KRITIS: Continuous Security and Resilience
- AWS Managed Services for Regulated Industries in Germany (BaFin, DORA, KRITIS)
- BaFin: Outsourcing and Audit Accountability
- DORA: Operational Resilience and Third-Party Risk
- KRITIS and Cross-Sector Obligations
- Continuous Audit Evidence
- Cloud-Auslagerung on AWS: Outsourcing Governance in Germany
- AWS Managed Services Models for Enterprises in Germany (AMS vs AWS MSP vs Hybrid)
- Executive Guidance
- Data Residency and Sovereignty for AWS Managed Services in Germany
- AWS Frankfurt Region and Residency Enforcement
- AWS European Sovereign Cloud
- Balancing Sovereignty and Performance
- Enterprise Reference Architecture for Managed AWS Operations in Germany
- Landing Zone and Multi-Account Governance
- Identity and Access Governance
- Continuous Security and Observability
- Resilience and Recovery Engineering
- How AWS Managed Services Operate in Practice (Change, Incidents, Service Control)
- Change Management
- Incident Detection and Response
- Controlled Service Provisioning
- FinOps and Cost Governance in AWS Managed Services for Germany
- Cost Allocation and Accountability
- Continuous Optimization
- Executive Cost Predictability
- AWS Managed Services Cost in Germany: What Enterprises Should Expect
- Key Cost Drivers
- AWS Managed Services vs In-House Cloud Operations for German Enterprises
- AWS Managed Service Providers in Germany – What Enterprises Should Look For
- Migrating to AWS Managed Services Without Disrupting Operations
- AWS Managed Services Adoption Roadmap for German Enterprises
- Phase 1: Readiness and Regulatory Gap Assessment
- Phase 2: Landing Zone and Governance Build
- Phase 3: Phased Workload Onboarding
- Phase 4: Transition to Managed Operations
- Phase 5: Continuous Optimization
- How to Choose an AWS Managed Service Provider in Germany
- Contract Requirements for Regulated Enterprises
- SLA and Governance Expectations
- Future of AWS Managed Services in Germany
- AI-Driven Cloud Operations
- Sovereign Cloud Maturity
- Industry 4.0 and Edge Expansion
- How Appinventiv Delivers AWS Managed Services for Germany-Based Enterprises
- Frequently Asked Questions
Key takeaways:
- German cloud operations have shifted from technology execution to regulatory risk management.
- AWS Managed Services embed continuous compliance, security, and audit evidence into daily operations.
- German regulations demand provable control execution, not just compliant cloud architectures.
- Sovereignty, data residency, and outsourcing governance now drive cloud operating model decisions.
- Managed services reduce audit effort, incident risk, and internal cloud operations strain.
Most executive teams reach a point where the cloud stops being a technology initiative and becomes an operating risk decision. Infrastructure runs. Applications perform. The real question is whether security monitoring, compliance enforcement, incident response, and cost governance can scale under tightening regulation and rising operational complexity.
German enterprises face this pressure early. Compliance obligations expand. Supplier accountability is under closer scrutiny. Skilled cloud operations talent remains scarce, while business units demand faster digital delivery. The constraint is no longer cloud adoption. It is cloud operations maturity.
Industry data supports this reality, with 81% of companies already using AWS cloud services in Germany along with cloud services. Shifting the enterprise challenge decisively toward governance, compliance, and operational scale.
AWS Managed Services address this shift by moving day-to-day cloud operations, security execution, compliance controls, incident handling, and financial governance into a structured, auditable operating model. The outcome is not outsourcing technology. It embeds continuous operational discipline within regulator-aligned control frameworks.
In practical terms, AWS Managed Services in Germany operates AWS environments under continuous monitoring, with security policies, enforced structured change workflows, incident response processes, and automated compliance evidence generation aligned with German regulatory requirements. Internal teams retain strategic ownership. Managed operations deliver continuous execution, reporting, and audit readiness.
AWS’s continued infrastructure investment in Germany accelerates enterprise cloud adoption across key industries. As adoption scales, governance maturity becomes the dividing line between compliant growth and unmanaged risk.
This AWS managed services guide is written for C-suite and senior technology leaders responsible for cloud risk, compliance, and resilience. Its purpose is to enable leadership teams to leverage AWS managed services to move from cloud experimentation to industrialized, audit-ready cloud operations.
AWS plans €8.8B investment, driving enterprise cloud acceleration in Germany
What Is Included in Enterprise AWS Managed Services?
This AWS managed services guide section covers how enterprises cover continuous infrastructure operations, security execution, compliance enforcement, and financial governance across Amazon Web Services environments.
Most executive teams already understand what cloud migration delivers. The question is what happens after migration. Managed services fill the operational layer that keeps enterprise cloud environments secure, compliant, and continuously monitored at scale.
Typical service coverage includes:
- AWS infrastructure management in Germany: Provisioning, patching, configuration enforcement, and health monitoring of AWS environments.
- Security operations: Threat detection, security alert handling, vulnerability management, and incident response workflows.
- Compliance management: Continuous control monitoring, audit evidence generation, and regulatory reporting alignment.
- Backup and disaster recovery: Automated backups, restore testing, and resilience validation against defined RTO and RPO targets.
- Monitoring and observability: Centralized logging, metrics, alerting, and performance tracking across workloads.
- Financial governance (FinOps): Cost allocation, optimization, budget controls, and business unit reporting.
- Change management: Controlled request-for-change pipelines, approvals, and traceable change records.
This structure matters because German enterprises are not outsourcing technology. They are outsourcing the continuous execution of operational discipline.
Also Read: How can enterprises protect their data in cloud environments?
AWS Shared Responsibility Model in Managed Services
In AWS Managed Services, cloud security risk is shared between AWS, the managed service provider, and the enterprise, with each retaining defined accountability.
A common misconception is that managed services transfer full cloud responsibility to the provider. In reality, AWS secures the underlying infrastructure. Managed service providers run daily operations. Enterprises retain governance, data ownership, and risk accountability. Clarity here prevents compliance gaps later.
| Responsibility Area | AWS | Managed Service Provider | Enterprise |
|---|---|---|---|
| Physical data center security | Owns and operates | Not applicable | Not applicable |
| Core cloud infrastructure | Secures compute, storage, and network | Not applicable | Not applicable |
| Operating system and patching | Shared through managed automation | Executes patching workflows | Approves critical change windows |
| Identity and access AWS governance for enterprises | Provides IAM capabilities | Enforces access controls and monitoring | Defines access policies and role models |
| Security monitoring and incident response | Provides detection services | Operates monitoring and response | Owns escalation decisions and regulatory reporting |
| Compliance evidence generation | Provides control tooling | Produces continuous evidence | Owns audit response and accountability |
| Data ownership and classification | Not applicable | Not applicable | Fully owned by the enterprise |
This shared model matters in Germany. Regulators hold the enterprise accountable even when operations are outsourced. Managed services succeed when execution is delegated, but accountability remains clearly owned.
Key Challenges German Enterprises Face in AWS Managed Services Adoption
German enterprises adopting AWS Managed Services face operational, regulatory, and organizational challenges that must be addressed before outsourcing execution.
Moving to managed cloud operations is rarely blocked by technology. TFriction usually arises from governance alignment, regulatory interpretation, and internal operating culture. Recognizing these challenges early prevents costly redesign later.
Unclear Accountability In Outsourced Operations
Many enterprises assume managed services transfer operational risk entirely to the provider. In Germany, cloud risk management on AWS means regulators hold the enterprise accountable, regardless of outsourcing. A shared responsibility framework with documented decision rights, escalation ownership, and audit accountability prevents governance gaps.
Integrating Managed Operations With Existing IT Governance
Large organizations already run ITSM, SOC, and GRC platforms with a hybrid cloud AWS architecture. Managed services that operate outside these systems create parallel processes. Mature providers integrate monitoring, ticketing, compliance evidence, and reporting into existing enterprise governance systems.
Meeting German Outsourcing And Audit Rights Requirements
BaFin, KRITIS, and public sector procurement rules require contractual inspection rights and evidence of ownership. Contracts must define audit access, evidence retention, ownership, and support for regulator inspections before operational handover.
Enforcing Continuous Data Residency
Residency is often configured correctly, but drifts over time due to new workloads, logs, or backups. Service control policies, continuous configuration monitoring, and automated remediation maintain residency enforcement.
Maintaining Evidence Continuity During Transition
Operational handover can disrupt logging pipelines or incident records, creating gaps in audit evidence. Parallel operations and phased onboarding ensure logging, monitoring, and evidence pipelines remain uninterrupted.
Internal Team Resistance To Outsourcing
Platform and security teams may perceive managed services as a loss of control. Co-managed models retain internal governance ownership while externalizing execution capacity.
Scaling 24×7 Operational Coverage
Internal teams struggle to provide sustained round-the-clock monitoring without burnout or hiring pressure. Managed operations embed 24×7 coverage with defined escalation and reporting structures.
A consistent pattern emerges. Enterprises that address these challenges during design move to stable operations faster. Those that ignore them face operational friction after go-live.
Why German Enterprises Are Re-Evaluating AWS Cloud Operations
Most cloud programs deliver quick migration wins, but AWS strategy for large organizations must address risks that surface later. Audits demand access to evidence. Security teams uncover guardrail gaps. Incidents reveal unclear escalation of ownership.
AWS remains stable, but operations do not. German enterprises re-evaluate cloud governance as internal teams struggle with continuous monitoring, compliance enforcement, and 24×7 readiness amid growing findings and talent shortages.
This shift is reinforced by market momentum, with the European AWS Managed Services market projected to reach $653.54 million by 2032, reflecting how operational outsourcing is becoming a structural requirement rather than a tactical choice.
What Raises the Bar in Germany
- Availability assurance: Multi-zone resilience and tested disaster recovery
- Auditability: Centralized logging and immutable evidence retention
- Supplier accountability: Contractual control, inspection, and reporting rights
- Regulatory pressure: NIS2, DORA, GDPR, BSI C5, KRITIS enforcement
- Operational reality: Expanding cloud estates with limited internal capacity
Delaying action increases audit risk, compliance exposure, and operational fragility
Why This Decision Cannot Be Deferred in Germany
AWS managed services and cloud operations in Germany can no longer evolve gradually. Regulatory enforcement, sovereignty initiatives, and cloud skill shortages are moving faster than internal operating models can scale. Delaying action does not reduce risk. It allows compliance and operational gaps to grow inside production environments.
Forces accelerating urgency:
- NIS2 enforcement: Expands continuous security monitoring and incident-reporting obligations across more enterprises.
- DORA regulation: Mandates operational resilience and third-party risk controls for financial institutions.
- AWS European sovereign cloud programs: Influence how sensitive workloads must be architected and operated within EU jurisdiction.
- Talent constraints: Shortage of cloud security and operations specialists limits internal scalability.
- Cloud expansion: New digital, data, and AI workloads increase governance and evidence requirements.
This urgency is reinforced by AWS’s €8.8 billion investment in its Germany region, expected to support 15,200 jobs annually and contribute €15.4 billion to GDP, signaling long-term infrastructure commitment rather than short-term cloud expansion.
Enterprises that act early build controlled, audit-ready foundations. Those who delay often redesign cloud operations under audit or incident pressure, when correction costs are higher.
Compliance Requirements for AWS Managed Services in Germany
AWS security and compliance services in Germany ensure compliance is not assessed by policy existence alone but by continuous control execution. It is evaluated by whether controls run continuously and generate defensible evidence. Most cloud compliance gaps emerge when operational discipline drifts over time. AWS Managed Services embed continuous control execution directly into daily cloud operations.
BSI C5: Operationalizing Cloud Security Controls
BSI C5 is fundamentally an operations framework. It requires continuous enforcement and traceable evidence across identity governance, security logging, encryption, vulnerability management, incident handling, and change control.
In AWS environments, this typically includes:
- AWS Control Tower guardrails for account governance
- AWS Config for continuous configuration monitoring
- AWS Security Hub and GuardDuty for security findings aggregation
- Centralized CloudWatch and immutable S3 log archives
Managed operations ensure these controls remain enforced daily, not only during audit preparation cycles.
GDPR: Data Protection in Daily Cloud Operations
GDPR compliance fails when operational ownership is unclear. Common risks include inconsistent IAM role design, unmanaged encryption keys, or logs containing personal data outside retention rules.
Managed services standardize:
- Federated identity and least-privilege role models
- Enforced encryption using AWS KMS
- Centralized log storage with defined retention
- Predefined incident response workflows aligned to GDPR reporting timelines
This embeds GDPR compliance into default cloud behavior rather than manual enforcement.
Also Read: How to Develop a GDPR-Compliant Software for Your Business?
NIS2 and KRITIS: Continuous Security and Resilience
NIS2 expands cybersecurity and incident reporting obligations across more German enterprises. KRITIS operators must demonstrate tested resilience and recovery readiness.
Managed operations implementation:
- Continuous security monitoring and alert escalation
- Defined incident classification and response timelines
- Multi-AZ resilience design
- Tested backup and disaster recovery workflows
The result is continuous compliance execution with audit-ready evidence.
Also Read: Understanding the Regulatory Compliance Implications for Cloud Businesses
AWS Managed Services for Regulated Industries in Germany (BaFin, DORA, KRITIS)
AWS managed services for regulated industries in Germany recognize that cloud outsourcing is not a technology decision. It is a risk-and-accountability decision. Regulators focus less on which platform is used and more on who controls operations, owns evidence, and can intervene when failures occur. AWS Managed Services must therefore align with strict outsourcing, audit, and resilience obligations.
BaFin: Outsourcing and Audit Accountability
For financial institutions, cloud operations supporting critical functions fall under BaFin outsourcing rules. Institutions must demonstrate:
- Clear definition of outsourced cloud activities
- Retained accountability for operational risk
- Contractual audit and inspection rights
- Continuous monitoring of provider performance
- Exit and transition plans for service disruption
In managed AWS environments, this requires accessible incident records, change logs, access reports, and compliance dashboards. MSP models that operate as black boxes fail BaFin expectations. German financial institutions typically adopt customized MSP or hybrid models to preserve contractual control and audit transparency.
DORA: Operational Resilience and Third-Party Risk
DORA formalizes ICT risk governance for financial entities. Managed cloud operations must provide:
- Defined incident classification and reporting timelines
- Continuous ICT risk monitoring
- Regular backup and recovery testing
- Documented third-party risk assessments
- Enforceable exit strategies
The focus is evidence. Resilience must be tested and recorded, not just architected.
KRITIS and Cross-Sector Obligations
Healthcare, energy, transport, and public-sector operators face similar third-party risk and resilience requirements. Managed services must support regulatory reporting workflows, coordinated incident response, and alignment with business continuity.
Continuous Audit Evidence
Across regulated sectors, auditors ultimately ask one question: Can you prove continuous control execution? Managed operations deliver automated logs, change records, incident trails, and recovery-test evidence daily.
Cloud-Auslagerung on AWS: Outsourcing Governance in Germany
In Germany, cloud adoption is legally treated as Cloud-Auslagerung (IT outsourcing), not simple technology procurement. Under BaFin, KRITIS, and public-sector rules, enterprises must retain audit access, evidence ownership, and operational risk accountability even when cloud operations are managed externally.
AWS’s cloud managed services must therefore include contractual inspection rights, defined evidence retention, incident record accessible to regulators, and exit planning. BaFin explicitly requires that cloud providers not operate as black boxes. Managed operations must deliver transparent reporting and continuous evidence of compliance to meet German outsourcing governance expectations.
AWS Managed Services Models for Enterprises in Germany (AMS vs AWS MSP vs Hybrid)
When evaluating an AWS managed service provider in Germany, enterprises typically adopt one of three operating models. The right choice depends on governance maturity, regulatory outsourcing requirements, and the extent of operational control that must remain internal.
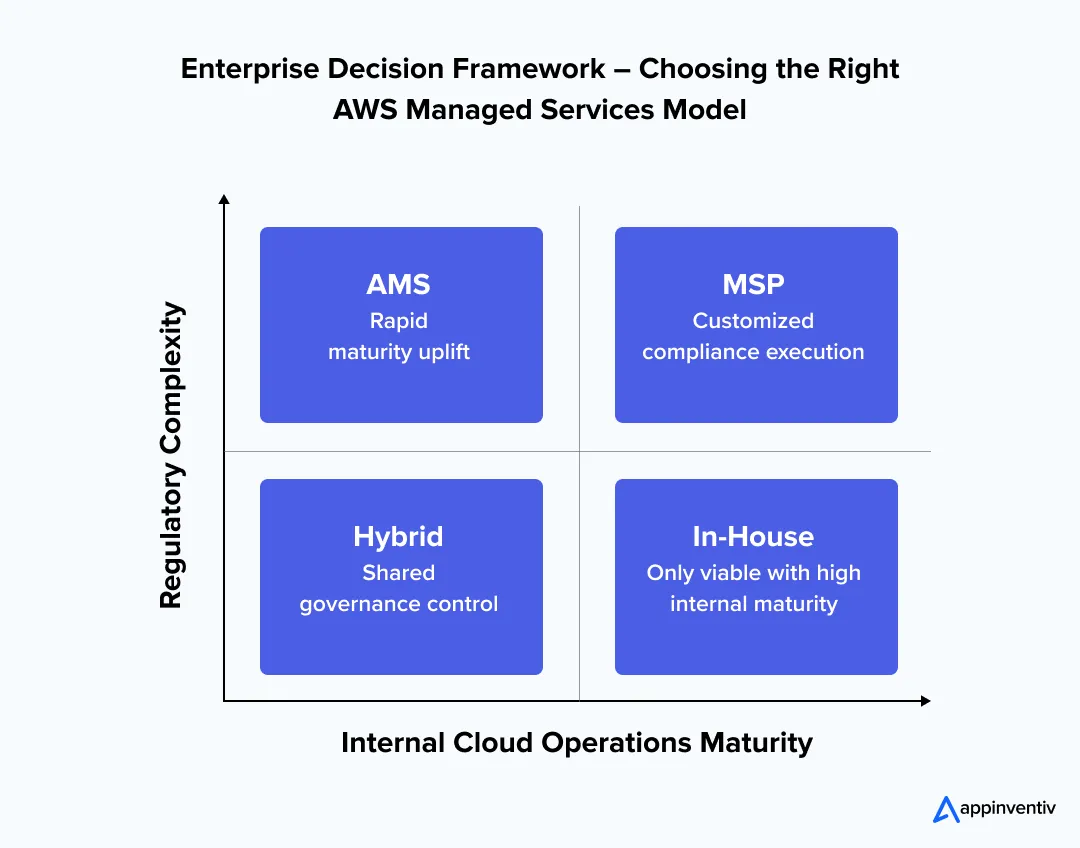
The difference is not in AWS tooling. It is in who executes operations, who owns evidence, and how accountability is structured under German regulatory expectations.
Managed Services Model Comparison
| Decision Area | AWS Managed Services (AMS) | AWS Managed Service Provider (MSP) | Hybrid / Co-Managed Model |
|---|---|---|---|
| Operating model | AWS-operated standardized runbooks and workflows | AWS managed service provider in Germany designed and operated cloud operations | Internal teams own governance, external teams execute operations |
| Governance customization | Limited customization | Fully customized to enterprise governance and GRC systems | Internal governance retained, execution delegated |
| Integration with ITSM / SOC / GRC | Standard AWS tooling | Integrated into enterprise ITSM, SOC, and GRC platforms | Shared integration model |
| Compliance evidence format | Standard AWS evidence outputs | Customized evidence mapped to internal audit templates | Internal review of externally generated evidence |
| BaFin / outsourcing alignment | Moderate | Strong contractual audit and inspection control | Strong enterprise retains direct governance ownership |
| Data residency and sovereignty enforcement | Policy-driven | Policy-driven plus contractual enforcement | Enterprise-defined with external execution |
| Incident and change control | AWS-defined workflows | Customized workflows aligned to enterprise processes | Shared runbooks with defined handoff points |
| Internal staffing requirement | Low | Low to moderate | Moderate |
| Speed of adoption | Fastest | Moderate | Moderate |
| Best fit in Germany | Enterprise AWS managed services for rapid maturity uplift | Regulated enterprises needing customized governance | Enterprises with mature internal cloud governance |
Executive Guidance
- AMS fits organizations needing rapid, standardized operating maturity.
- MSP models fit regulated enterprises that require customized audit, outsourcing, and reporting controls.
- Hybrid models fit enterprises, retaining strategic governance while scaling execution capacity.
In Germany, most large regulated enterprises favor MSP or Hybrid models to meet BaFin, DORA, KRITIS, and internal supplier governance obligations.
Data Residency and Sovereignty for AWS Managed Services in Germany
Data residency and sovereignty are decisive factors in German cloud approvals. Beyond performance and cost, enterprises must address jurisdiction, audit access, legal exposure, and long-term regulatory stability. A technically sound architecture can still fail to gain approval if sovereignty and residency controls are not enforceable in day-to-day operations.
AWS Frankfurt Region and Residency Enforcement
Using the AWS Frankfurt Region (eu-central-1) enables German data residency, but residency must be continuously enforced, not assumed.
A residency-safe AWS setup typically includes:
- Workloads deployed exclusively in eu-central-1
- No cross-region replication for regulated data
- In-region backup vaults and log archives
- Region-locked AWS KMS encryption keys
- Service control policies blocking non-approved regions
- Continuous configuration monitoring and automated remediation
Managed cloud operations convert residency from a design decision into an enforced operating rule with continuous audit evidence.
AWS European Sovereign Cloud
Some enterprises require protection from non-EU legal influence. This applies to public sector systems, defense supply chains, regulated research, and sensitive industrial IP environments.
The AWS European Sovereign Cloud introduces:
- EU-jurisdiction infrastructure
- EU-restricted administrative access
- Separated control planes
- EU-only data handling and support operations
The AWS European sovereign cloud reduces the risk of extraterritorial access and simplifies regulatory approvals. Managed service providers must be able to operate under EU-restricted support and escalation models to align with sovereignty requirements.
Sovereign Cloud Key and Jurisdiction Control
For the German public sector, defense, and regulated research workloads, data residency alone is insufficient. Regulators increasingly require cryptographic sovereignty, meaning encryption keys must remain outside cloud providers’ control.
AWS support services for enterprises include External Key Management (XKS), allowing enterprises to host encryption keys in on-premise or EU-controlled HSMs while still using AWS services.
Sovereignty-aligned control includes:
- AWS KMS with External Key Store (XKS)
- Enterprise or EU-hosted master keys
- No AWS operator access to key material
- Full audit logging of key usage
Sovereign Cloud: Cost vs Risk Lens
| Area | Standard AWS | AWS European Sovereign Cloud |
|---|---|---|
| Admin access | Global support | EU-restricted support |
| Key ownership | AWS-managed | Enterprise-controlled (XKS) |
| Control plane | Global | EU-dedicated |
| Typical cost impact | Baseline | ~10–15% premium |
| Regulatory exposure | Moderate | Minimized |
Sovereign-ready managed operations accelerate regulatory approvals and prevent redesign when EU jurisdiction or key ownership is mandated.
Standard AWS MSP Germany vs Sovereign-Ready MSP
| Capability Area | Standard AWS MSP Germany | Sovereign-Ready AWS MSP |
|---|---|---|
| Data jurisdiction | EU regions selectable | EU-only jurisdiction enforced |
| Administrative access | Global support possible | EU-based personnel only |
| Control plane separation | Shared global control plane | Dedicated sovereign control plane |
| Support and incident handling | Global follow-the-sun | EU-restricted operations |
| Audit access model | Standard audit rights | Expanded regulator audit access |
| Data residency enforcement | Policy-driven controls | Hard residency enforcement |
| Sub-processor usage | Global subcontractors | EU-restricted subcontractors |
| Extraterritorial access risk | Possible | Structurally minimized |
| Typical workload fit | Commercial enterprise | Public sector and sensitive IP |
Balancing Sovereignty and Performance
Cross-region replication improves resilience. Global monitoring enhances visibility. Sovereignty imposes boundaries. Mature managed operations resolve this by classifying workloads, enforcing stricter controls for regulated data, and allowing documented exceptions for non-sensitive systems.
The result is enforceable residency, compliant sovereignty, and sustained operational resilience.
Enterprise Reference Architecture for Managed AWS Operations in Germany
German enterprises leveraging AWS cloud services in Germany require environments that are not only secure and scalable, but also governable, auditable, and operationally predictable. A managed services model succeeds only when the underlying architecture is designed for continuous control execution and evidence generation.
Landing Zone and Multi-Account Governance
German enterprises use a multi-account AWS strategy to isolate workloads and enforce compliance at scale. A managed-ready landing zone standardizes cloud governance on AWS from the start
Core landing zone elements:
- Multi-account AWS strategy using AWS organizations by risk tier
- Service control policies for the region and service enforcement
- Standardized network patterns
- Automated account provisioning with guardrails
In mature environments, the landing zone acts as a control plane.
Governance enforcement layers:
- Control plane: Preventive policy enforcement
- Detection plane: Continuous posture monitoring
- Evidence plane: Immutable audit logs and reports
This loop prevents drift, automates compliance, and keeps cloud operations audit-ready.
Identity and Access Governance
Auditors in regulated German environments prioritize access governance. Managed identity models typically include:
- Federated authentication integrated with corporate directories
- Role-based access enforcing least privilege
- Permission boundaries for workload teams
- Just-in-time privileged access
- Automated access reviews with immutable logs
This ensures consistent access patterns and traceable evidence across teams and environments.
Continuous Security and Observability
AWS security and compliance services in Germany prove that security tooling is only effective when operationalized. Cloud managed application security baselines include:
- AWS GuardDuty for threat detection
- AWS Security Hub for posture aggregation
- AWS Config for continuous compliance monitoring
- Centralized CloudWatch and immutable log archives
Findings flow into monitored queues with defined escalation paths and audit trails.
Resilience and Recovery Engineering
Regulated workloads require proven resilience, not theoretical designs.
Managed operations implementation:
- Automated backups with monitored success reporting
- Regular restore and disaster recovery testing
- Defined RTO and RPO targets
- Multi-Availability Zone architectures
This embeds recovery readiness into daily operations rather than annual testing cycles.
How AWS Managed Services Operate in Practice (Change, Incidents, Service Control)
Cloud operating maturity is tested not in architecture diagrams but in how changes, incidents, and service requests are executed under pressure. In Germany, auditors expect structured change control, regulators expect defined incident reporting, and business units expect speed. Managed operations align all three.
Change Management
In unmanaged environments, change traceability weakens over time. Managed AWS operations introduction:
- Standardized change categories and risk levels
- Automated request-for-change pipelines
- Defined maintenance windows
- Approval workflows for high-risk changes
- Immutable change logs for audit evidence
Routine activities such as scaling, patching, and certificate renewals run through automated workflows. Emergency changes follow defined escalation and post-incident documentation paths.
Incident Detection and Response
Managed operations implementation:
- Continuous monitoring feeding centralized alert queues
- Severity-based incident classification
- Defined response and escalation timelines
- Predefined communication templates
- Recorded remediation actions for audit traceability
Security findings trigger tickets, guided response playbooks, and regulator-aligned reporting when required.
Controlled Service Provisioning
Uncontrolled environment creation is a major compliance risk. Managed services prevent this through service catalogs offering:
- Pre-approved infrastructure templates
- Embedded security baselines
- Automated network and logging configuration
- Enforced cost allocation tags
- Default identity role application
Teams retain self-service speed while governance remains enforced by design.
FinOps and Cost Governance in AWS Managed Services for Germany
For German enterprises, cloud cost management is not just an optimization exercise. It is a governance requirement. Business units must own consumption. Finance teams must forecast spend. Executives must link cloud investment to measurable outcomes. AWS Managed Services embeds the FinOps discipline directly into daily operations.
Cost Allocation and Accountability
Without enforced attribution, cloud spend becomes unmanaged overhead. Managed operations implementation:
- Mandatory cost allocation tags at provisioning
- Automated chargeback or showback reporting
- Budget thresholds with alerting
- Business-unit-level consumption dashboards
Provisioning pipelines block environments that lack cost center tagging. This ensures accountability is enforced at creation, not reconciled later.
Continuous Optimization
AWS cost optimization in Germany requires continuous execution, not quarterly reviews. Managed FinOps practices include:
- AWS workload optimization
- Rightsizing and idle resource detection
- Savings Plan and Reserved Instance coverage management
- Scheduled scaling for non-production workloads
- Anomaly detection for unexpected spend
Optimization findings become tracked operational tasks with defined owners and resolution timelines. Finance teams gain predictable forecasts. Engineering teams receive actionable remediation. Leadership gains transparency into the value of cloud realization.
Executive Cost Predictability
Compared to in-house operations, AWS managed services convert variable staffing, tooling, and incident-response costs into predictable operating expenditure with defined service levels. AWS ROI for enterprises focuses not only on savings but also on controlled cloud economics, reduced risk exposure, and defensible budget planning.
AWS Managed Services Cost in Germany: What Enterprises Should Expect
AWS Managed Services pricing in Germany reflects the scale of cloud environments, regulatory obligations, and required operational coverage. Enterprises are not paying only for monitoring tools. They are investing in continuous compliance execution, security operations, audit readiness, and resilient cloud governance.
Typical enterprise managed services engagements in Germany fall within the following range.
Typical AWS Managed Services Cost Range (Germany)
| Environment Scale | Typical Enterprise Context | Monthly Cost Range (EUR / USD) |
|---|---|---|
| Mid-size AWS estate | 10–30 accounts, moderate compliance requirements | €35,000 – €80,000 ($40,000 – $90,000) |
| Large enterprise environment | 30–100 accounts, multi-business workloads requiring AWS compliance in Germany (GDPR, BSI, ISO 27001) | €80,000 – €180,000 ($90,000 – $200,000) |
| Regulated or critical infrastructure | Financial services, KRITIS, NIS2, BaFin / DORA obligations | €180,000 – €350,000 ($200,000 – $390,000) |
| Sovereign or highly customized operations | EU Sovereign Cloud, restricted access models, custom governance | €350,000 – €380,000+ ($390,000 – $420,000+) |
AWS infrastructure consumption costs are billed separately based on actual service usage.
Key Cost Drivers
Managed services pricing is determined less by technology and more by governance and risk requirements. The primary cost drivers include:
- Number of AWS accounts and workload complexity
- Required compliance frameworks (GDPR, BSI C5, NIS2, KRITIS, BaFin, DORA)
- 24×7 monitoring and incident response coverage
- Degree of customization in governance, reporting, and audit evidence
- Data residency and sovereign cloud operating constraints
- Integration with internal ITSM, SOC, and GRC systems
- Required SLA levels for availability and recovery
- Volume of security and compliance evidence generation
Also Read: How Much Does It Cost to Migrate to the Cloud?
AWS Managed Services vs In-House Cloud Operations for German Enterprises
For German enterprises, AWS strategy for large organizations means choosing between in-house cloud operations and AWS Managed Services to determine audit readiness, risk exposure, and long-term operational stability.
Many organizations evaluating AWS ROI for enterprises begin with internal cloud teams. Over time, regulatory pressure, tooling complexity, and 24×7 coverage needs force a strategic decision. Build a full-scale operations organization internally or adopt a managed execution model.
| Decision Area | In-House Cloud Operations | AWS Managed Services |
|---|---|---|
| Compliance burden | Internal teams design and run controls | Controls embedded into managed operations |
| Audit readiness | Manual evidence collection | Continuous audit-ready evidence pipelines |
| Talent availability | Dependent on scarce cloud operations hiring | Shared access to specialized operations teams |
| 24×7 coverage | Requires shift and on-call rotations | Built-in round-the-clock monitoring |
| Cost predictability | Variable staffing and tooling costs | Defined operating expenditure models |
| Risk exposure | Higher dependency on individual teams | Shared accountability with defined SLAs |
A simple pattern emerges. In-house operations preserve control but increase execution risk. Managed services retain strategic control while externalizing continuous operational discipline.
AWS Managed Service Providers in Germany – What Enterprises Should Look For
Not all AWS managed service provider in Germany options are equipped to meet regulatory, sovereignty, and audit requirements.
Many providers offer strong technical capabilities. Fewer can operate in compliance with Germany’s governance, outsourcing, and data jurisdiction expectations. For enterprise buyers, selection is less about tools and more about operational accountability.
Evaluation criteria for German enterprises
- Regulatory alignment: Proven experience mapping AWS operations to BSI C5, GDPR, NIS2, DORA, and sector-specific requirements.
- Audit and inspection rights: Willingness to contractually support internal audit and regulator access to operational evidence.
- Data residency enforcement: Ability to technically enforce EU and Germany-based workload and log residency.
- Sovereign cloud readiness: Capability to operate under EU-restricted support and jurisdiction models when required.
- Operational maturity: Defined change, incident, and escalation workflows with measurable SLAs.
- Evidence ownership: Clear rules ensuring audit logs, security records, and compliance reports remain accessible to the enterprise.
A practical reality often emerges. Choosing the right AWS managed service provider in Germany matters because providers optimized for generic global delivery models struggle with the country’s governance expectations. Enterprises benefit from partners that treat compliance execution and audit evidence as first-class operational outcomes.
Migrating to AWS Managed Services Without Disrupting Operations
Cloud migration to AWS Germany for enterprises involves a phased operational handover to avoid audit disruptions, service downtime, and compliance regressions.
Most large organizations already run active production workloads in AWS before adopting managed operations. The challenge is not infrastructure migration. It is a migration of responsibility, evidence pipelines, and operational control without interrupting regulated business functions.
Common enterprise transition scenarios
- Brownfield enterprise cloud migration to AWS: Existing AWS accounts and workloads are integrated into managed landing zones without replatforming.
- Parallel operations during transition: Internal teams and managed providers operate jointly while monitoring, incident, and change workflows are validated.
- Regulatory approval alignment: Outsourcing risk assessments, audit rights, and evidence ownership are formalized before operational handover.
- Phased workload onboarding: Non-critical environments move first, followed by regulated and production-critical systems.
- Evidence continuity protection: Logging, monitoring, and compliance reporting pipelines remain uninterrupted throughout the transition.
A practical outcome of phased transition is predictable risk control. Internal teams retain visibility. Regulators see continuous evidence. Business units experience no service disruption.
Ensure operational continuity while modernizing your infrastructure with expert-led governance and scaling.
AWS Managed Services Adoption Roadmap for German Enterprises
This AWS managed services guide roadmap shows why German enterprises rarely fail due to technology choices. They struggle when governance arrives too late, operational ownership is unclear, or compliance is treated as a later-phase activity. In Germany, this risk is amplified by regulatory expectations. Compliance and audit readiness must be built in from the first operational phase.
A managed services adoption roadmap enables a controlled transition to industrialized cloud operations without disrupting production environments or breaking evidence continuity. The objective is steady maturity uplift, not disruptive migration.
Phase 1: Readiness and Regulatory Gap Assessment
Enterprises work with AWS consulting services in Germany partners to assess current AWS environments, security posture, and governance maturity. Controls are mapped against GDPR, BSI C5, NIS2, KRITIS, and sector-specific outsourcing requirements. Workloads requiring strict residency or sovereignty are identified. Audit evidence expectations are defined early to prevent later gaps.
Phase 2: Landing Zone and Governance Build
Standardized multi-account structures, region guardrails, identity governance, logging pipelines, and change workflows are implemented. New environments are provisioned through controlled pipelines with embedded security and compliance baselines.
Phase 3: Phased Workload Onboarding
Lower-risk workloads transition first, followed by regulated and production-critical systems. Monitoring, backup, and recovery patterns are validated during onboarding to ensure uninterrupted compliance evidence.
Phase 4: Transition to Managed Operations
24×7 monitoring, incident response, change control, and compliance checks become fully operational. Internal teams shift to oversight and risk governance while managed teams execute daily operations.
Phase 5: Continuous Optimization
Resilience testing, compliance refinement, AWS workload optimization, FinOps optimization, and supplier performance reviews drive continuous maturity and audit readiness.
How to Choose an AWS Managed Service Provider in Germany
Selecting an AWS managed service provider in Germany partnership is less about comparing tools or headcount and more about ensuring accountability under regulatory scrutiny. In German enterprise environments, the real risk is not technical failure. It is a loss of audit access, unclear evidence ownership, or weak outsourcing governance. The right provider strengthens operational maturity. The wrong one introduces hidden compliance exposure.
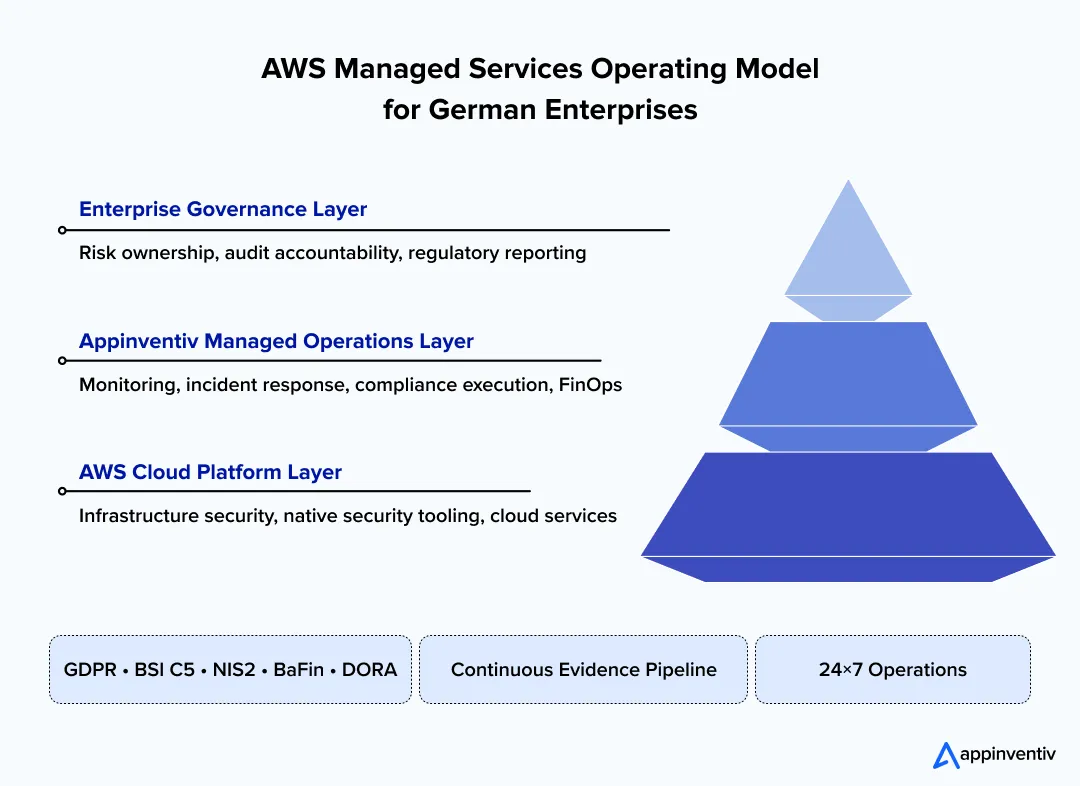
A strong selection process aligns executive sponsors, procurement, risk, and IT leadership around governance expectations before contracts are signed.
Contract Requirements for Regulated Enterprises
German enterprises operating under GDPR, BSI C5, NIS2, KRITIS, or BaFin oversight need contractual safeguards that standard MSP agreements often miss:
- Explicit audit and inspection rights for internal audit teams and external regulators
- Enforced data residency and data handling commitments
- Controlled use and location of subcontractors
- Incident notification timelines aligned with regulatory reporting windows.
- Evidence retention obligations and defined access formats
- Exit and transition support to prevent vendor lock-in
Contracts should also clarify ownership of security logs, incident records, change histories, and compliance reports. Without defined evidence ownership, audit continuity becomes a critical risk.
SLA and Governance Expectations
In regulated environments, service quality is measured by risk control, not uptime alone. Effective agreements include:
- Uptime targets tied to workload criticality
- Severity-based incident response and resolution timelines
- Change success rate thresholds.
- Backup and recovery validation metrics
- Security remediation time commitments
Oversight must be continuous, not ad hoc. Mature governance models include weekly operational reviews, monthly security and compliance reporting, quarterly resilience testing, and annual audit evidence walkthroughs. This cadence keeps providers accountable and ensures cloud operations remain transparent, compliant, and defensible at the board level.
Future of AWS Managed Services in Germany
Cloud strategies are often planned on three-year roadmaps. Operational reality in Germany evolves much faster. Regulations shift. Automation matures. Threat landscapes change.
Germany already dominates the European AWS managed services market, making operational excellence a baseline expectation rather than a competitive differentiator.
Enterprises that treat cloud operations as a one-time transformation frequently rebuild governance foundations sooner than expected. Those designing for continuous evolution stay compliant and competitive.
Intelligent operations, maturity in sovereignty, and industry-specific acceleration will shape the next phase of AWS Managed Services in Germany.
AI-Driven Cloud Operations
Manual alert triage and reactive incident handling do not scale in complex enterprise environments. AI-driven operations are becoming standard practice through:
- Automated correlation of security and performance events
- Predictive detection of configuration drift
- Intelligent prioritization of remediation actions
- Self-healing automation for known failure patterns
For German enterprises, the impact is practical. Faster response without expanding headcount. Stronger compliance evidence through automated decision and remediation logging. Managed service providers investing in AIOps will shift from execution vendors to strategic operations partners.
Also Read: AI in Cloud: Transforming Enterprises with 10 Benefits and Applications
Sovereign Cloud Maturity
European sovereign cloud platforms are expanding in capability and adoption. This will influence public sector programs, regulated research, defense supply chains, and sensitive industrial IP environments. Enterprises adopting sovereignty-ready managed operations today avoid costly redesign later.
Also Read: Why Private AI Is the Future of Ethical and Secure AI Adoption for Enterprises?
Industry 4.0 and Edge Expansion
Connected manufacturing and real-time industrial systems extend cloud operations into factories and field environments. Managed services must now unify governance across central cloud, edge, and operational technology systems.
Build cloud operations ready for sovereignty, AI, and regulation
How Appinventiv Delivers AWS Managed Services for Germany-Based Enterprises
German enterprises seeking AWS consulting services in Germany do not struggle to find cloud vendors. They struggle to find partners who can operate AWS environments under German regulatory accountability and audit scrutiny. Appinventiv’s managed services are built on a simple principle. Cloud operations must deliver continuous compliance, not periodic correction.
Our AWS consulting services in Germany approach starts with governance before technology. Regulatory controls, audit expectations, risk ownership, and decision rights are defined upfront. This ensures landing zones, identity models, security tooling, and service catalogs align with both engineering requirements and German compliance obligations.
Our managed operations generate continuous audit-ready evidence through automated control monitoring, immutable log retention, and structured change and incident trails. Security operations run 24×7 using AWS-native threat detection, defined escalation paths, and remediation runbooks aligned to enterprise risk teams. FinOps discipline is embedded through enforced cost attribution, optimization workflows, and executive-level spend visibility.
Operational Credibility at Scale
- 500+ cloud migrations executed
- 2000+ cloud deployments delivered
- 24×7 cloud operations monitoring
- 20+ hybrid-cloud environments built
- 35+ industries supported
- 50+ cloud experts onboard
- 5+ strategic cloud partnerships
Business Impact Delivered
- Up to 30% AWS cost optimization in Germany
- 99.90% availability SLA
- 2x infrastructure efficiency gains
After enterprise cloud migration to AWS, enterprises typically experience faster audit cycles, reduced security backlogs, improved recovery readiness, and predictable cloud economics within the first year. Let’s connect and build audit-ready cloud operations
Frequently Asked Questions
Q. What are AWS Managed Services in Germany?
A. AWS Managed Services in Germany are structured cloud operating frameworks that run continuous security monitoring, compliance enforcement, incident response, change control, and cost governance for AWS environments. They enable German enterprises to meet GDPR, BSI C5, NIS2, KRITIS, and DORA obligations by embedding audit-ready control execution into daily cloud operations.
Q. Why choose AWS managed services in Germany?
A. German enterprises choose AWS Managed Services to operate cloud environments under continuous compliance, security monitoring, and audit-ready governance. Regulatory frameworks such as GDPR, BSI C5, NIS2, and BaFin require continuous control execution and evidence retention. Managed services provide structured operations, 24×7 monitoring, defined incident handling, and cost governance that internal teams often struggle to sustain at scale.
Q. How do AWS managed services work for enterprises?
A. AWS Managed Services operate enterprise cloud environments through standardized or customized runbooks covering monitoring, change control, incident response, backup, security operations, and compliance checks. AWS or MSP partners execute daily operations while enterprises retain governance and risk ownership. This model ensures continuous enforcement of controls, generation of audit evidence, and predictable service levels across multi-account AWS estates.
Q. Are AWS managed services GDPR compliant in Germany?
A. AWS Managed Services can support GDPR compliance when environments are designed and operated correctly. This includes enforced encryption, controlled identity access, defined data retention, incident response workflows, and the generation of audit evidence. Managed operations ensure continuous monitoring and enforcement of these controls, thereby reducing risks such as misconfigured access, unmanaged logs, and inconsistent data-handling practices.
Q. What are the AWS compliance requirements in Germany?
A. AWS compliance in Germany (GDPR, BSI, ISO 27001) typically requires alignment with GDPR for data protection, BSI C5 for cloud security controls, NIS2 for cybersecurity operations, KRITIS for critical infrastructure resilience, and BaFin or DORA for financial outsourcing governance. Enterprises must prove continuous control execution, audit access, incident reporting, and evidence retention, not just compliant architecture designs.
Q. How much do AWS managed services cost in Germany?
A. Costs depend on environment size, workload criticality, compliance requirements, and operating model. Pricing typically combines a management fee with usage-based AWS consumption. While managed services introduce operational expenditure, enterprises often offset costs through reduced incident impact, lower staffing pressure, improved compliance efficiency, and FinOps-driven cloud optimization.
Q. Are AWS managed services worth it for enterprises?
A. For enterprises operating under German regulatory and audit expectations, AWS Managed Services are often worth the investment. They reduce compliance risk, improve resilience, provide predictable cloud governance, and scale operational capacity without expanding internal teams. The value lies less in tooling and more in continuous execution, accountability, and audit-ready cloud operations.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

Driving Business Resilience with Active-Active Multi-Region DR on AWS
For businesses handling high-value transactions, downtime is not an option. Even a few minutes of disruption can lead to lost revenue, unhappy customers, and reputational damage. In this success story, we showcase how we partnered with a customer to design an Active-Active multi-region disaster recovery (DR) architecture on AWS, achieving a Recovery Time Objective (RTO)…

Exploring Top Storage Solutions on AWS Marketplace
As the volume of data continues to grow, businesses are increasingly seeking efficient, scalable, and secure storage solutions. AWS Marketplace offers a variety of storage solutions to meet these needs, providing organizations with the flexibility to choose the best tools for their specific requirements. This blog will explore three top storage solutions available on AWS…

Understanding Amazon Glacier: A Comprehensive Guide
Amazon Glacier, a cloud-based storage service offered by Amazon Web Services (AWS), is tailored specifically for long-term data archiving and backup. It provides a secure, low-cost solution for storing large amounts of data that are infrequently accessed. Whether you are a well-established business looking to archive massive amounts of data or a startup needing a…