- What Is Identity and Access Management in Healthcare?
- The Growing Importance of Identity and Access Management in Healthcare
- Core Components of Healthcare Identity Access Management
- 1. Identity Lifecycle Management
- 2. Identity Verification and Fraud Prevention
- 3. Authentication and Authorization
- 4. Single Sign-On (SSO) and Federated Identity
- 5. Privileged Access Management (PAM)
- 6. Device and Third-Party Identity Management
- 7. Audit, Compliance, and Reporting
- Key Challenges in Implementing IAM in Healthcare
- 1. Complex and Fragmented Systems
- 2. Balancing Security with Usability
- 3. Handling Emergencies Without Breaking the Rules
- 4. Insider Threats and Human Error
- 5. Keeping Up with Compliance
- 6. Budgets and Growth
- 7. Vendors and Devices Everywhere
- Benefits of Modern IAM Solution in the Healthcare Industry
- Best Practices for Building a Secure and Scalable IAM Program
- 1. Start with Zero Trust
- 2. Use Multi-Factor Authentication and Single Sign-On
- 3. Build IAM Around Real Workflows
- 4. Automate Wherever Possible
- 5. Keep an Eye on Behavior
- 6. Train, Remind, Repeat
- 7. Measure What Matters
- Real World Use Cases of Identity and Access Management in Healthcare
- Example 1: PeaceHealth – Role-Based Access for 24,000 Users
- Example 2: Multi-State Health Insurer – Centralized IAM for 200 Applications
- Example 3: CHU de Montpellier – AI-Powered IAM with Microsoft Azure
- The Future of Identity and Access Management in Healthcare
- Building Trust Through Technology: The Appinventiv Approach
- FAQs
Key Takeaways
- Healthcare runs on trust, and Identity and Access Management is what keeps that trust intact by protecting every login, record, and device.
- A modern IAM system does more than secure passwords, it connects people, systems, and data safely across hospitals and clinics.
- AI and automation are changing how IAM works, spotting risks faster and taking routine security tasks off the IT team’s plate.
- Better access control means better patient care, stronger compliance with laws like HIPAA, and fewer disruptions in treatment.
- The future of IAM lies in decentralized identities, passwordless access, and smarter authentication, making digital healthcare more secure and seamless for everyone.
Every hospital today runs on identity. From doctors logging into EHR systems to patients accessing lab reports online, every interaction depends on verifying who’s on the other side. That’s why Identity and Access Management in Healthcare has quietly become the backbone of digital health security.
Healthcare data breaches continue to top all industries, with the report citing average cost of healthcare data breach estimating an average cost of USD 7.42 million per incident. Each breach reminds us how fragile trust can be when access isn’t tightly controlled.
A well-built Identity and Access Management for Healthcare framework doesn’t just block unauthorized users, it ensures clinicians, patients, and devices can securely access what they need, exactly when they need it. In this blog, we’ll break down the core components, challenges, and best practices that define IAM in modern healthcare system
What Is Identity and Access Management in Healthcare?
Every day, thousands of people log into hospital systems — doctors updating charts, nurses checking test results, patients viewing reports, vendors running diagnostics. Behind all this activity lies one critical system keeping things safe, an Identity Management in Healthcare.
Think of it as the digital security guard for the healthcare world. It verifies who someone is, decides what they can access, and keeps an eye on everything happening inside. Without it, one stolen password or unchecked device could expose thousands of patient records in minutes.
A strong identity management in healthcare framework doesn’t just authenticate people; it manages their entire journey. From the moment a new employee joins to the day their access is revoked, IAM ensures permissions match their role and responsibilities.
Modern healthcare identity and access management also covers more than humans. Machines and devices — like connected ventilators, wearable sensors, and telehealth systems — are now part of the same network. That’s why IAM in healthcare has become as much about maintaining patient safety as it is about cybersecurity.
When implemented right, it helps organizations stay compliant, protect data, and ensure that care continues without disruption. In short, it’s what makes digital healthcare trustworthy.
The Growing Importance of Identity and Access Management in Healthcare
Trust lies at the heart of healthcare. When patients enter a hospital or log into a tele-health app, they expect that their data will stay secure and private. Yet in today’s digital world, that trust is under constant pressure.
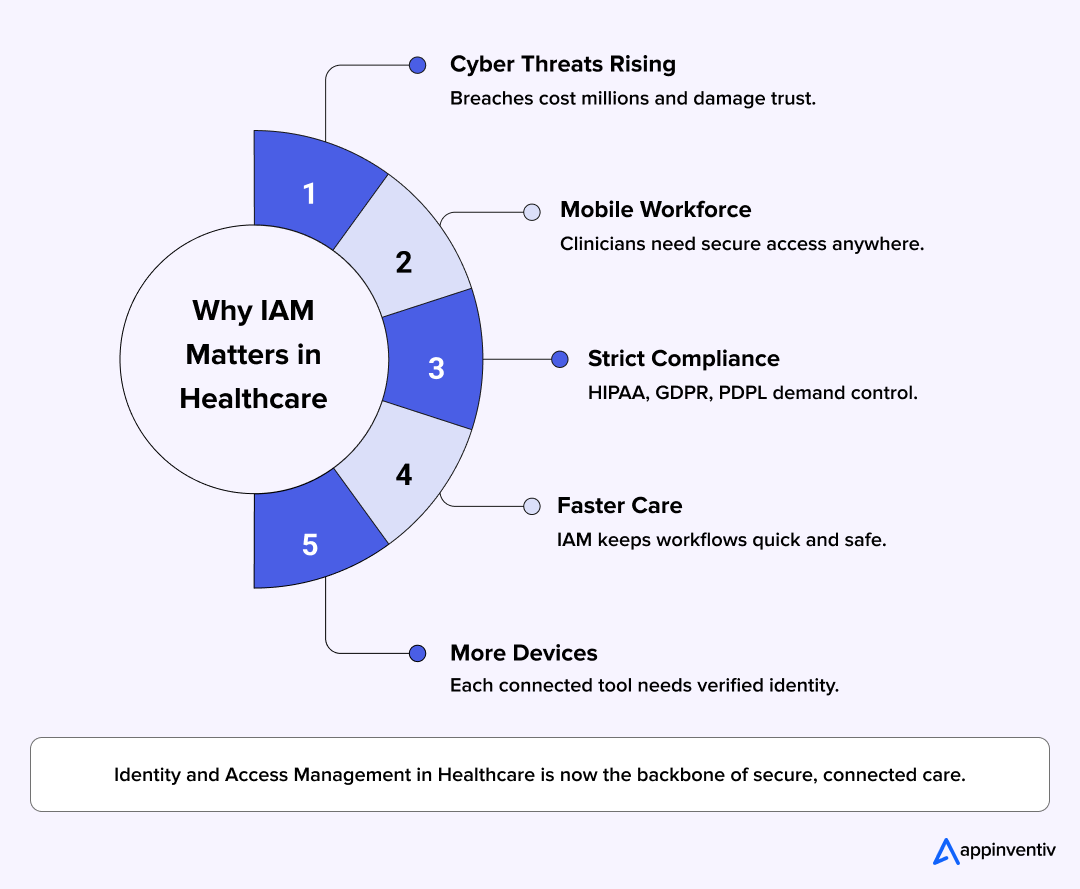
Every new connection, whether it is a mobile device, a cloud-based system, a remote consultation, opens up another chance for something to go wrong. That is why effective identity access management in healthcare is not just a technical control, it is a vital piece of the care puzzle.
Here’s why this topic demands attention right now:
- Hospitals today face rising cyber threats, and healthcare data security breaches carry some of the greatest financial and reputational risks. According to McKinsey, provider organisations still incur some of the highest costs when breaches happen.
- Healthcare work has gone mobile. Doctors and nurses access systems from the clinic, from home, from their mobile devices. The demand for secure, legitimate access is higher than ever.
- Regulations aren’t optional. Laws like HIPAA, GDPR and PDPL require that access to patient data be tightly managed and auditable.
- At the same time, care must not be delayed. Slow authentication or broken access flows can disrupt treatment. Healthcare IAM needs to keep care teams moving, not slow them down.
- The volume and diversity of data and devices are exploding. From wearable monitors to IoMT systems, every identity counts—whether human or machine.
In short, the importance of identity and access management for healthcare has moved from maybe helpful’ to ‘outright essential’. As healthcare digitalises, the organisations that build access strategies will be the ones patients trust and clinicians rely on.
Core Components of Healthcare Identity Access Management
Building strong Identity and Access Management in Healthcare is like designing a hospital’s digital heartbeat. Everything, from who logs in, to which system they touch, to how data moves, all that depends on the working of IAM quietly in the background.
Here’s what goes into a solid Healthcare IAM foundation.
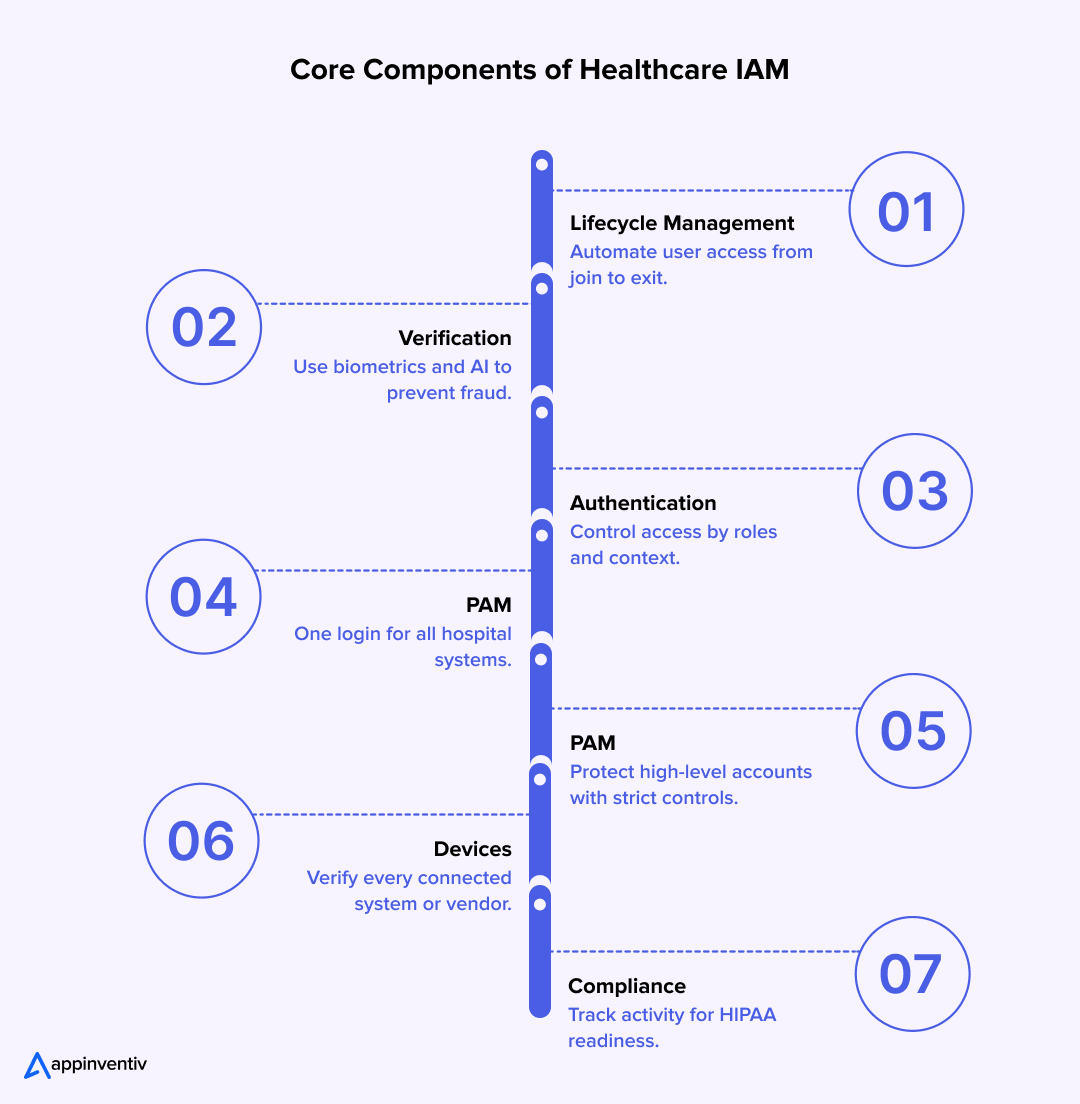
1. Identity Lifecycle Management
Hospitals are full of movement. Doctors rotate between departments, new nurses join, contractors come and go. Every individual requires the right access and at the right time – and nothing less.
That’s where identity lifecycle management steps in. It automatically:
- Set up new user accounts when someone joins.
- Updates their permissions when roles change.
- Cuts off access the moment they leave.
This might sound routine, but it’s often where breaches start. A single forgotten login can become a doorway for misuse. Automating these steps keeps systems lean, secure, and compliant.
2. Identity Verification and Fraud Prevention
In healthcare, identity errors can cost more than money, as they can put lives at risk. Verifying every user, whether it’s a clinician, vendor, or patient logging into a telehealth portal, has become essential.
Modern identity management in healthcare uses:
- Biometric scans or smart cards for quick staff verification.
- AI-based monitoring to flag suspicious login attempts.
- Regular rechecks of vendor and third-party credentials.
With so many people and devices connecting daily, fraud prevention isn’t just about catching bad actors — it’s about making sure every login belongs to the person it claims to.
3. Authentication and Authorization
Think of this as the front door and the master key. Authentication proves identity; authorization decides what that person can do once they’re inside.
Modern healthcare identity and access management systems use layered protection — multi-factor authentication for stronger logins and access rules based on roles, attributes, and context. A nurse might see lab results but not billing data. A doctor might access patient charts but not security settings.
The goal is simple: give people what they need to do their job, nothing more, nothing less.
4. Single Sign-On (SSO) and Federated Identity
Anyone who’s worked in a hospital knows the frustration of juggling multiple logins. SSO solves that. One secure sign-in unlocks all authorized systems, saving time and reducing password fatigue.
Using standards like OAuth2 and OpenID Connect, SSO links everything with EHRs, telemedicine tools, lab software, and more while keeping sessions encrypted and traceable. When done right, it feels invisible to users but airtight to intruders.
5. Privileged Access Management (PAM)
Some logins hold the keys to the kingdom. These “superuser” accounts are necessary but dangerous if left unchecked.
Privileged Access Management locks them down by:
- Storing credentials in encrypted vaults.
- Recording every session for audit trails.
- Limiting how long high-level access stays active.
It’s quiet insurance against insider mistakes or intentional misuse, and it’s one of the most critical pieces of IAM in healthcare cybersecurity.
6. Device and Third-Party Identity Management
Security in healthcare no longer ends with people. It now includes connected devices, smart monitors, diagnostic tools, and partner systems that all talk to each other.
A strong identity and access management solution assigns each device its own digital identity. That way, only trusted machines and vendors can communicate with hospital networks. It’s like giving every device its own badge before letting it through the door.
7. Audit, Compliance, and Reporting
No matter how advanced a hospital’s systems are, compliance is what keeps it safe from penalties and reputational damage. IAM platforms simplify this by tracking every access request and every change made.
Detailed reports help organizations prove compliance with HIPAA and other regional standards. As Deloitte notes, healthcare organizations that unify their identity systems reduce risk exposure and improve audit readiness.
When you combine all these pieces, identity and access management for healthcare becomes more than a security tool — it becomes an operational framework. It helps people work faster, keeps patients safe, and quietly guards every digital doorway in the system.
Key Challenges in Implementing IAM in Healthcare
Setting up Identity and Access Management in healthcare sounds easy until you actually try to do it. Hospitals deal with thousands of users every day from doctors to nurses, technicians to even cleaning staff, all needing access to different systems at different times. The more you try to control, the harder it gets to keep things simple.
Here are the few challenges of identity and access management in healthcare:
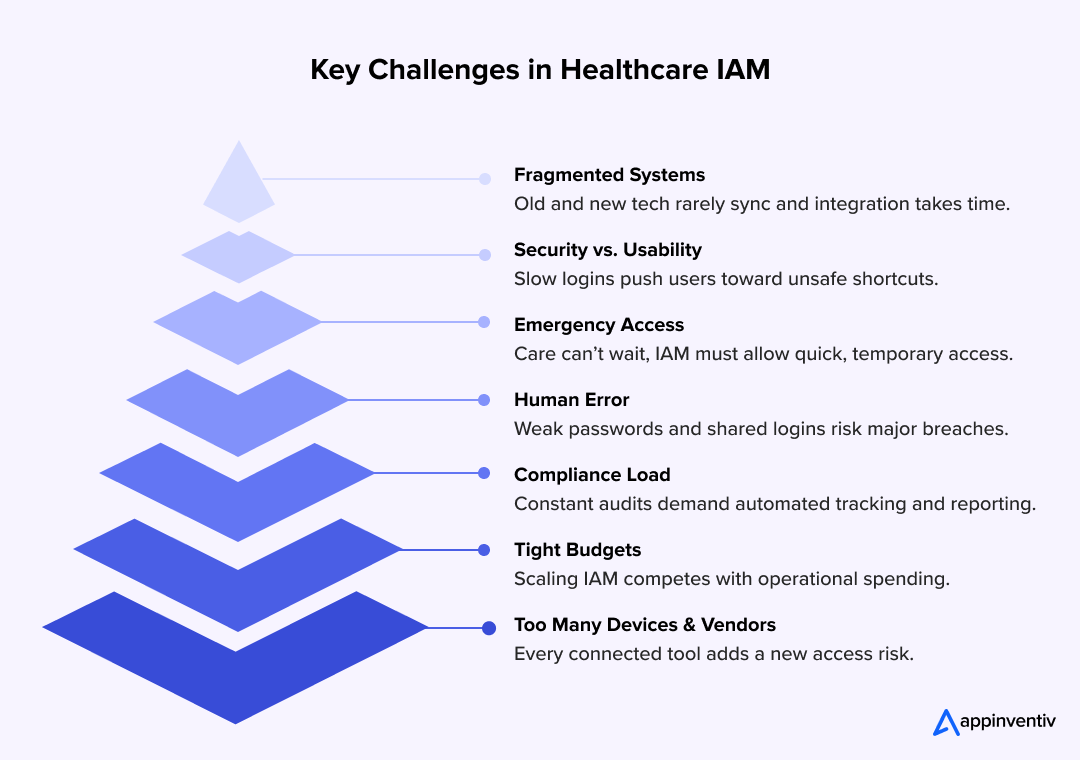
1. Complex and Fragmented Systems
Most hospitals run on a mix of old and new technology. You’ll find one department using a 10-year-old EHR, another on a brand-new cloud platform. Getting them to talk to each other is like teaching different languages to a group of people overnight.
What works: Don’t replace everything at once. Start by connecting the systems that share the most sensitive data to modernize legacy systems in healthcare. Use a single IAM layer to manage access between them. Once that’s stable, expand. Slow progress is better than a total shutdown.
2. Balancing Security with Usability
Doctors hate waiting for logins. Nurses too. The longer it takes to access a system, the more frustrated they get, and the frustration will lead to shortcuts. Shared passwords. Sticky notes on monitors. You name it.
What works: Design IAM around how people actually work. Add single sign-on for faster entry. Use biometrics where possible. The goal isn’t to make people follow more rules, it’s to make security invisible while still keeping it strong.
3. Handling Emergencies Without Breaking the Rules
Emergencies don’t wait for approvals. When a patient’s life is on the line, doctors need access now. IAM systems that are too rigid can end up slowing down treatment, which defeats the purpose of implementing IAM in the first place.
What works: Set up an emergency access system with strict time limits. Let senior staff authorize temporary access instantly, but make sure every click and change gets recorded. That way, care isn’t delayed, and accountability stays intact.
4. Insider Threats and Human Error
No system can fix human behavior. People reuse passwords, forget to log out, and sometimes share credentials just to get things done faster. In healthcare, one small mistake can expose hundreds of patient records.
What works: Train often, but keep it practical. Show real examples of what went wrong elsewhere and how it could have been avoided. Use IAM tools that spot unusual activity such as a nurse logging in at 3 a.m. from a new device. Instances like this should notify the security team before it becomes a bigger problem.
5. Keeping Up with Compliance
Every few months, there’s a new law or policy. HIPAA, GDPR, PDPL and the acronyms never stop. Each requires proof that you know who accessed what and when. For hospitals already short on staff, this can feel like a full-time job.
What works: Automate what you can. Most modern IAM systems can log and report every access automatically. It takes pressure off teams and keeps the audit trail clean and ready when needed.
6. Budgets and Growth
Security tools are not cheap, and hospitals are often forced to pick between better tech or more hands on the floor. On top of that, every merger or expansion means a new set of systems that need integration.
What works: Start small. Focus on the areas that face the highest risk like patient data, lab systems, and telehealth platforms. Choose IAM solutions that scale easily. Cloud-based systems usually work better for that since they grow as you do.
7. Vendors and Devices Everywhere
It’s not just people logging in anymore. Every connected device from infusion pumps to imaging machines has its own access point. Add contractors and vendors into the mix, and the security perimeter becomes impossible to see.
What works: Treat every device and vendor account like a temporary guest. Give them access only to what they need and nothing more. Review those permissions regularly. If a contractor finishes a project, their login should disappear the same day.
At the end of it, successful identity and access management for healthcare is not about perfection. It’s about awareness. The hospitals that get it right are not the ones with the fanciest tools, but the ones that make IAM part of everyday work simple, steady, and consistent.
Benefits of Modern IAM Solution in the Healthcare Industry
Modern identity and access management solutions are quietly reshaping how hospitals protect data and manage people. When built right, IAM supports care teams instead of slowing them down.
- Stronger protection for patient data: Centralized systems limit who can see or change sensitive records, keeping information safe from unauthorized use.
- Easy compliance: A HIPAA compliant identity management setup automatically logs every access attempt and makes audits straightforward.
- Time saved for clinicians: Single sign-on and automated provisioning cut down repetitive logins, letting doctors and nurses move quickly between tools.
- Smarter connections across digital health: Good identity management in digital health brings EHRs, telemedicine apps, and medical devices into one secure framework.
- Clear accountability: Every action is traceable, which helps security teams act fast if something looks unusual.
- Built for growth: Modern IAM expands easily as hospitals add new facilities, staff, or connected devices.
The benefits of modern IAM solutions in the healthcare industry go beyond compliance. They help create a digital environment where care feels seamless, secure, and human again.
Best Practices for Building a Secure and Scalable IAM Program
Every healthcare organization knows why Identity and Access Management matters. The real question is how to make it work every day, for everyone and not just for the IT team. Good IAM is equal parts technology, habit, and culture. It should make work smoother, not harder.
Here are the practices that help hospitals and clinics get there.
1. Start with Zero Trust
Zero Trust is not a product. It’s a mindset. It means no one, not even someone inside your network is trusted automatically. Every login, every request, gets verified.
For healthcare, this matters because users change constantly. Consultants come and go, nurses move across departments, vendors update devices remotely. Zero Trust makes sure every connection earns its place before entering.
2. Use Multi-Factor Authentication and Single Sign-On
Passwords alone are too weak. Adding another step, like a fingerprint or one-time code, keeps accounts safe even if a password leaks.
Pair that with single sign-on so staff only log in once to access multiple systems. It saves time, reduces password fatigue, and keeps logins consistent across tools.
3. Build IAM Around Real Workflows
The best IAM setups don’t fight daily routines, instead they blend into them seamlessly. If a doctor switches between an EHR and a lab portal, both should recognize the same identity instantly.
Before rolling out a new system, spend time shadowing your teams. Watch how they actually use technology. Then design access controls that fit those patterns, not the other way around.
4. Automate Wherever Possible
Manual access management breaks down quickly in a large hospital. Automating tasks like account creation, updates, and removals reduces delays and human error.
Automation with smart technology in healthcare also helps compliance. Every change gets logged, every permission update tracked. That record makes audits easier and keeps regulators satisfied.
5. Keep an Eye on Behavior
Once the system is running, monitoring doesn’t stop. IAM tools can now track behavior to spot unusual activity, like a staff member logging in from two locations at once or a sudden spike in data downloads.
Catching small inconsistencies early prevents bigger problems later. Think of it as continuous hygiene rather than crisis control.
6. Train, Remind, Repeat
No security system works if people don’t use it correctly. Most breaches happen because someone clicked a bad link or shared a password to save time.
Make IAM training a regular part of onboarding and refreshers. Keep it short and realistic. Instead of showing slides, share real stories, tell them what went wrong, why it happened, and how simple habits could have stopped it.
7. Measure What Matters
Good security should show results. Track how long it takes to remove access when someone leaves, how many failed logins happen each week, and how many compliance alerts get closed.
Small improvements over time prove the system is working. These numbers also help justify future investments when budgets come up for review.
When done right, identity and access management for healthcare doesn’t get in the way of care — it supports it. It helps hospitals stay compliant, builds trust with patients, and gives staff one less thing to worry about.
Real World Use Cases of Identity and Access Management in Healthcare
Imagine a hospital where clinicians log in once and gain access to patient records, check diagnostics, and update treatment plans, seamlessly. That’s not fiction anymore, it’s the direction being shaped by AI and automation in healthcare IAM. Below are few real world examples showcasing exactly the same:
Example 1: PeaceHealth – Role-Based Access for 24,000 Users
Focus: Large-scale role-based IAM deployment
PeaceHealth implemented a centralized identity and access management system across ten medical centers and hundreds of clinics. The organization defined over 5,000 roles and enabled 100 percent role-based access for 24,000 caregivers. This structured model reduced redundant permissions, improved audit readiness, and made onboarding significantly faster.
Example 2: Multi-State Health Insurer – Centralized IAM for 200 Applications
Focus: Scalable identity governance and automation
A major U.S. health insurer serving 5 million members modernized its IAM framework with Infosys. The new system automated provisioning for 24,000 users and integrated over 200 applications. Risk-based behavior analytics improved monitoring, while self-service tools enhanced the user experience for employees and partners.
Example 3: CHU de Montpellier – AI-Powered IAM with Microsoft Azure
Focus: AI and automation for healthcare identity management
CHU de Montpellier, one of Europe’s leading teaching hospitals, partnered with Microsoft Azure AI to modernize access and identity workflows. The system uses AI to detect suspicious login behavior and automate identity provisioning across departments. Clinicians now spend less time managing logins and more time with patients, while IT teams maintain real-time visibility into access activity.
The Future of Identity and Access Management in Healthcare
The future of Identity Management in healthcare is about making technology work quietly in the background so people can focus on care. What’s coming next is not more security layers, but smarter ones.
- Hospitals will move toward decentralized identities, where patients keep control of their own information and decide who can access it. Blockchain authentication will make every access traceable and trustworthy, giving healthcare leaders full visibility without extra paperwork.
- Passwordless access will become normal. Biometrics and secure devices will replace complex passwords that slow people down. AI in healthcare will play a bigger role too, learning from behavior and flagging risks before they become breaches.
- As connected devices multiply, hospitals will start managing their identities just like human users. A scanner, a wearable, or a diagnostic tool will have its own secure identity — each verified before it ever touches patient data.
The change will not happen overnight, but it is already underway. The healthcare organizations that start now will be the ones patients trust most in the digital decade ahead.
For a deeper dive into the future of health tech, explore our healthcare trends blog.
Building Trust Through Technology: The Appinventiv Approach
At the heart of every great healthcare system is trust. Patients trust that their data will stay private. Doctors trust that the systems supporting them will never fail. And leaders trust that their technology partners understand what’s at stake. That is what makes Identity and Access Management in Healthcare more than a cybersecurity topic — it is a commitment to safe, connected care.
At Appinventiv, that commitment drives everything we build. For over 10 years, our team has helped healthcare enterprises strengthen their digital core through secure and intelligent systems. We have delivered 500+ digital health platforms and partnered with 450+ healthcare clients, combining technology and empathy to improve how care is delivered.
One project that reflects this philosophy is YouCOMM, an in-hospital communication platform that empowers patients to call for assistance instantly. It streamlines nurse coordination, enhances patient safety, and demonstrates how technology can serve people without getting in their way.
Through our healthcare IT consulting services, we help enterprises evaluate their existing digital infrastructure, identify vulnerabilities, and design IAM frameworks that align with compliance needs and operational realities.
Alongside that, our custom healthcare software development services ensure every solution we create is secure, scalable, and tailored to the organization’s unique workflow. From EHR integrations to cloud-based identity platforms, our work stays focused on one goal — protecting lives through better digital experiences.
Appinventiv continues to help healthcare organizations build trust where it matters most: between patients, professionals, and the technology connecting them.
Let’s build your secure, compliant healthcare IAM solution.
FAQs
Q. What is Identity and Access Management in Healthcare?
A. It’s a framework that keeps hospital systems safe by controlling who can see what. In simple terms, Identity and Access Management in Healthcare makes sure every doctor, nurse, or staff member has the right access to the right data at the right time. It helps hospitals protect patient records, avoid data breaches, and meet privacy laws like HIPAA.
Q. Why Do Healthcare Organizations Need Robust Identity Access Management?
A. Hospitals run on data, and that data moves fast between departments, apps, and devices. Without strong identity control, there’s a real risk of unauthorized access. A robust IAM setup keeps information secure, supports compliance, and gives teams the confidence that every access is legitimate. It’s as much about protecting patients as it is about keeping operations steady.
Q. How Does Healthcare Identity Access Management Improve Patient Care?
A. When access works smoothly, care moves faster. Clinicians can view test results, update records, or share information instantly, without security barriers getting in the way. IAM also keeps that data accurate and private, helping teams collaborate safely and give patients the confidence that their information is handled responsibly.
Q. What Role Does Automation Play in Healthcare Identity Access Management?
A. Automation removes most of the repetitive work. It sets up new accounts, adjusts permissions when roles change, and closes access when someone leaves. It can also watch for strange activity, such as a login from an unusual device, and alert the security team immediately. For large healthcare networks, automation keeps IAM efficient and consistent.
Q. How Often Should Healthcare Organizations Review Their IAM Implementation?
A. A good rule is to review IAM once a year. But if a hospital grows, merges, or adds new systems, it should happen sooner. Regular reviews make sure the access rules still fit how people actually work and that security settings keep up with new technology and regulations.
Q. What Can IAM Do for Healthcare?
A. IAM brings order to complex healthcare systems. It connects people, processes, and technology in a way that protects data without slowing down care. With a modern setup, hospitals get better compliance, faster workflows, and safer patient experiences. In short, Identity and Access Management in Healthcare turns security from a barrier into an enabler — one that supports both care delivery and trust.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.
How to Build a Custom Pediatric EMR and EHR System?
Key takeaways: Clinical Precision: Custom systems accommodate pediatric-specific data points like percentile curves and weight-based longitudinal dosing. Interoperability: Seamless data exchange via HL7 FHIR ensures your practice stays connected to pharmacies, labs, and state registries. Regulatory Resilience: Built-in compliance with HIPAA, HITECH, and MACRA/MIPS reduces legal friction. Enhanced Engagement: Parent portals reduce administrative overhead by…

Change Management in Healthcare: Principles, Processes, and Models
Key Takeaways Change in healthcare fails quietly when ownership, workflow alignment, and follow-through are missing. Successful change management in healthcare focuses on adoption, not just system implementation. Clinical workflows and workforce capacity determine whether transformation sticks or stalls. Governance, clear accountability, and post-go-live support matter more than the model used. Sustainable healthcare transformation depends on…

A Practical Guide to Building Your Mental Health Chatbot - Use Cases, Cost, & ROI
Key takeaways: Mental health chatbots work when they know their limits. They’re most useful as a gentle first step, not as a stand-in for real care. Good chatbot design is more about judgment than AI. Clear boundaries, calm responses, and safety matter more than smart language models. Enterprises invest in chatbots to make support easier…