- What Is a Software Audit in an Enterprise Environment?
- What Are the Strategic Business Value and Benefits of Software Auditing
- Improving Governance and Operational Visibility
- Reducing Risk Exposure Across Security and Compliance
- Controlling Costs Through License and Asset Clarity
- Supporting Modernization and Transformation Decisions
- Enabling Better Executive Decision Making
- What Types of Software Audit Do Enterprises Rely On?
- Software License Compliance Audit
- Software Asset Management Audit
- Software Compliance Audit
- Software Quality Audit
- Software System and Architecture Audit
- Internal Software Audit Versus Independent Audits
- Emerging Audit Scopes Driven By AI And Automation
- How Enterprises Perform Software Audits: A Structured Framework
- Before the Audit: Governance and Scope Alignment
- During the Audit: Assessment and Evidence Collection
- After the Audit: Translating Findings into Action
- What Are the Common Challenges in Enterprise Software Auditing?
- Legacy Systems With Limited Documentation
- Tool Sprawl And Fragmented Data Sources
- Organizational Resistance And Ownership Ambiguity
- Translating Technical Risk Into Executive Language
- Balancing Audit Depth With Operational Continuity
- Use Cases Where Software Audits Become Non-Negotiable
- Pre-Merger Or Acquisition Technical Due Diligence
- Legacy Modernization And Platform Re-Architecture
- Cloud Migration Readiness And Post-Migration Validation
- Preparing For Regulatory And Customer-Driven Compliance Reviews
- Recurring Security Incidents Or Performance Degradation
- Rapid Scaling Across Regions Or Business Units
- Vendor Rationalization And Software Portfolio Cleanup
- How Enterprises Prioritize Software Audit Risks
- Start With Severity And Likelihood
- Factor In Business Criticality And Dependencies
- Account For Regulatory And Contractual Exposure
- Balance Containment With Long-Term Remediation
- Risk vs. Effort Matrix: How CTOs Prioritize Audit Findings
- How Enterprises Use This Matrix in Practice
- Enterprise Software Audit Checklist: What A Comprehensive Audit Should Always Cover
- How Are Enterprises Moving Toward Continuous Software Auditing?
- Choosing the Right Software Audit Partner: What Enterprises Should Evaluate Before Engagement
- Proven Enterprise And Industry Experience
- Ability To Translate Technical Risk Into Business Outcomes
- Security, Compliance, And Governance Expertise
- Independent, Tool-Agnostic Assessments
- Post-Audit Remediation And Advisory Support
- Turning Software Audits Into Long-Term Enterprise Advantage
- FAQs
Key Takeaways
- Software audits now support enterprise governance, not just technical compliance checks.
- Effective audits focus on production reality, not isolated tools or static documentation.
- Enterprises use audits to guide major decisions, including modernization, cloud, and vendor strategy.
- Risk is prioritized by impact and exposure, not by the number of findings.
- Audit value comes from execution, when insights translate into remediation and delivery.
In large enterprises, software risk rarely announces itself through failure. It shows up quietly as rising run costs, stalled releases, security exceptions, or last-minute compliance escalations. Most organizations did not design their current software landscape. It evolved through years of acquisitions, cloud adoption, SaaS expansion, and tactical fixes layered onto legacy systems. What boards now see is not an IT problem, but a growing concentration of operational and financial risk embedded in software decisions.
That risk has a measurable impact. McKinsey & Company estimates that technical debt alone can consume 20% to 40% of an enterprise’s IT budget, limiting the ability to fund innovation and increasing exposure to outages and security gaps. When software assets, dependencies, and controls are not periodically audited, blind spots compound. Licensing non-compliance, misconfigured systems, and undocumented integrations move from operational inefficiencies to material governance issues with regulatory and reputational consequences.
As a result, software audits are no longer treated as periodic IT hygiene. In more mature organizations, they are embedded into enterprise governance and risk management cycles. Audit findings inform executive decisions on modernization, cloud investment, vendor rationalization, and risk prioritization. This shift reframes the software audit from a reactive control exercise into a decision-enabling mechanism, which leads naturally to a clearer understanding of what an enterprise software audit actually evaluates and how it is executed in practice.
What Is a Software Audit in an Enterprise Environment?
A software audit in an enterprise setting goes beyond checking code or running security scans. It is a structured software system audit focused on governance, operational visibility, and risk exposure across complex environments. The goal is to help leadership understand how software decisions affect cost, compliance, and business continuity at scale.
A software audit is often confused with other assessments, but the scope is broader.
- Software audit evaluates governance, controls, and enterprise risk
- Code review focuses on implementation quality
- Security testing identifies vulnerabilities
- Compliance assessment checks regulatory alignment
What enterprises actually evaluate during a software audit includes multiple layers of the technology stack.
- Applications and architectural dependencies
- Infrastructure across cloud and legacy systems
- Data access, controls, and usage
- Delivery pipelines, release governance, and third-party exposure
Enterprises typically combine internal software audit efforts with independent software audit services when objectivity, regulatory confidence, or executive assurance is required. This blended approach ensures decisions are based on complete visibility rather than isolated technical signals.
What Are the Strategic Business Value and Benefits of Software Auditing
Enterprise software environments rarely stay static. Systems evolve, teams change, vendors rotate, and delivery models shift. Over time, the gap between how software is expected to operate and how it actually runs in production widens. This is where the real benefits of software auditing emerge. A disciplined software audit program helps organizations recalibrate that gap using evidence rather than assumptions.
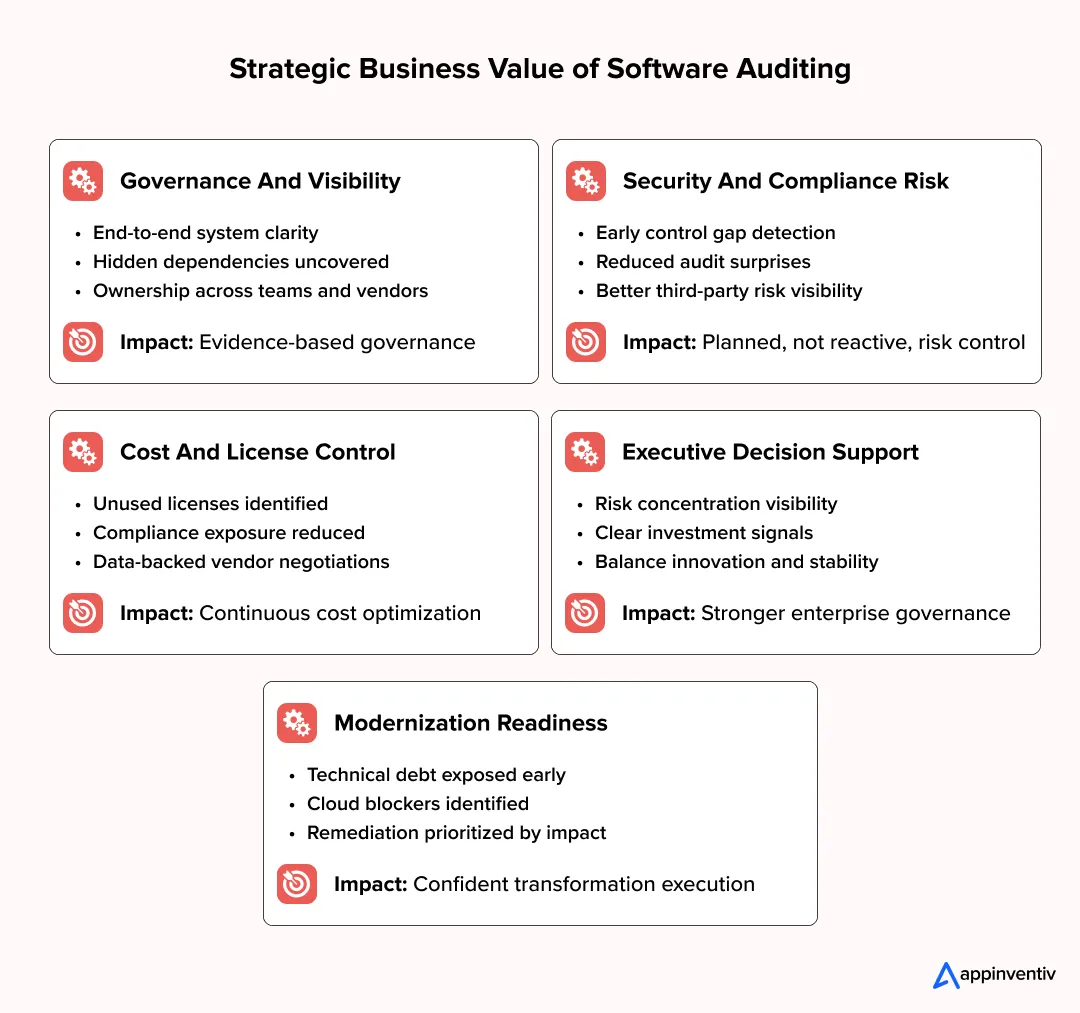
Improving Governance and Operational Visibility
As software portfolios expand, visibility tends to fragment across teams and platforms.
A structured software audit helps enterprises:
- See how applications, infrastructure, and data flows interact in real operating conditions
- Surface dependencies that were never formally documented
- Clarify ownership for systems that span multiple teams or vendors
- Restore governance where cloud and SaaS adoption diluted control
These insights support governance conversations with facts, not opinions.
Reducing Risk Exposure Across Security and Compliance
Risk often accumulates in areas that sit outside formal processes.
Through targeted software compliance audit and software quality audit efforts, organizations can:
- Identify control gaps and configuration drift early
- Validate compliance across regulatory and contractual obligations
- Detect unmanaged third-party and open-source components
- Reduce last-minute remediation ahead of formal audits
This shifts risk management from reactive response to planned control.
Controlling Costs Through License and Asset Clarity
License sprawl and tool duplication are common side effects of scale.
A focused software license audit and software asset management audit allows enterprises to:
- Identify unused or underused licenses
- Address non-compliant usage before it escalates
- Align spend with actual usage patterns
- Strengthen vendor negotiations with data
Cost control becomes continuous rather than corrective.
Supporting Modernization and Transformation Decisions
Major initiatives fail when underlying constraints are discovered late.
Audit insights support transformation by:
- Exposing technical debt that limits scalability
- Identifying systems that block cloud migration or re-architecture
- Prioritizing remediation based on operational impact
- Reducing uncertainty in planning cycles
This improves execution confidence for large programs.
Enabling Better Executive Decision Making
When audit findings are framed correctly, they move beyond IT.
For leadership teams, software audits provide:
- Clear visibility into where risk is concentrated
- Evidence to guide investment and remediation priorities
- Context for balancing innovation with operational stability
Used this way, software auditing strengthens governance and long-term resilience without slowing delivery.
What Types of Software Audit Do Enterprises Rely On?
Enterprise software ecosystems operate across distributed architectures, multiple delivery pipelines, and shared data layers. As a result, no single audit lens is sufficient. Mature organizations rely on multiple types of software audit, each targeting a different dimension of operational and governance risk. The value comes from knowing which audit to run, when, and why.
Software License Compliance Audit
License risk rarely sits in procurement records alone. It usually emerges from how software is actually used across teams, environments, and identities. A software license compliance audit focuses on identifying gaps between contractual entitlements and real consumption.
This audit examines:
- License entitlement versus actual usage using metering and reconciliation data
- Licensing models such as named user, concurrent user, core based, or usage based
- SaaS overconsumption and unused licenses identified through SSO, IAM, and CASB logs
- Contractual audit clauses, true-up thresholds, and vendor audit rights
- Shadow IT exposure surfaced through network traffic and identity activity
The primary objective is to reduce financial leakage and prevent vendor-initiated compliance actions that can lead to unplanned costs or renegotiations under pressure.
Software Asset Management Audit
While license audits focus on contractual exposure, a software asset management audit addresses visibility and control. Its goal is to establish a reliable system of record for software assets across the enterprise.
This audit evaluates:
- Discovery and inventory accuracy across on-premise, cloud, and SaaS environments
- Asset lifecycle management from provisioning to decommissioning
- Ownership and accountability for applications and tools across teams
- Redundant, orphaned, or underutilized software assets
- Integration between asset management tools, identity systems, and procurement workflows
A mature asset management audit enables better forecasting, cleaner audits, and stronger cost governance by ensuring enterprises understand what they own, what they use, and what they no longer need.
Software Compliance Audit
Compliance risk usually originates from configuration gaps, not missing policies.
A software compliance audit evaluates:
- Control alignment against frameworks such as SOC 2, ISO 27001, HIPAA, and PCI-DSS
- IAM enforcement including RBAC, MFA, and privileged access controls
- Data classification, encryption at rest and in transit, and key management practices
- Audit logging, log retention, and SIEM integration
- Configuration drift across environments caused by manual changes or IaC misalignment
This audit type is critical for regulated industries and customer assurance programs.
Software Quality Audit
Quality failures at scale are rarely caused by isolated bugs. They are architectural.
A software quality audit focuses on:
- Code maintainability, cyclomatic complexity, and technical debt indicators
- Architectural consistency across services and domains
- Fault tolerance mechanisms such as retries, circuit breakers, and graceful degradation
- Load handling, concurrency limits, and resource contention
- Test coverage across unit, integration, regression, and performance testing
These audits surface structural weaknesses that affect reliability and scalability.
Software System and Architecture Audit
Complex systems fail at integration points, not at individual services.
A software system audit evaluates:
- End-to-end architecture including microservices, APIs, and message queues
- Data flow consistency across synchronous and asynchronous integrations
- Dependency mapping and service coupling
- Single points of failure across compute, storage, and network layers
- Alignment between system design and non-functional requirements
This audit supports informed decisions around re-architecture and platform consolidation.t6
Internal Software Audit Versus Independent Audits
Enterprises typically balance ongoing oversight with independent validation.
- Internal software audit teams focus on continuous control monitoring, policy adherence, and SDLC governance
- Independent software audit services are used when neutrality, regulatory defensibility, or board-level assurance is required
This dual approach improves audit credibility without overloading internal teams.
Each audit type addresses a specific risk layer. When coordinated under a single audit strategy, they provide leadership with a defensible, system-level view of risk exposure, operational health, and readiness for change.
Emerging Audit Scopes Driven By AI And Automation
Once AI models move into production, traditional software audits stop being sufficient. Risk no longer sits only in infrastructure or access controls. It shows up in data pipelines, model behavior, and how AI outputs are used inside real business workflows. Enterprises that have already deployed AI are encountering this shift first-hand.
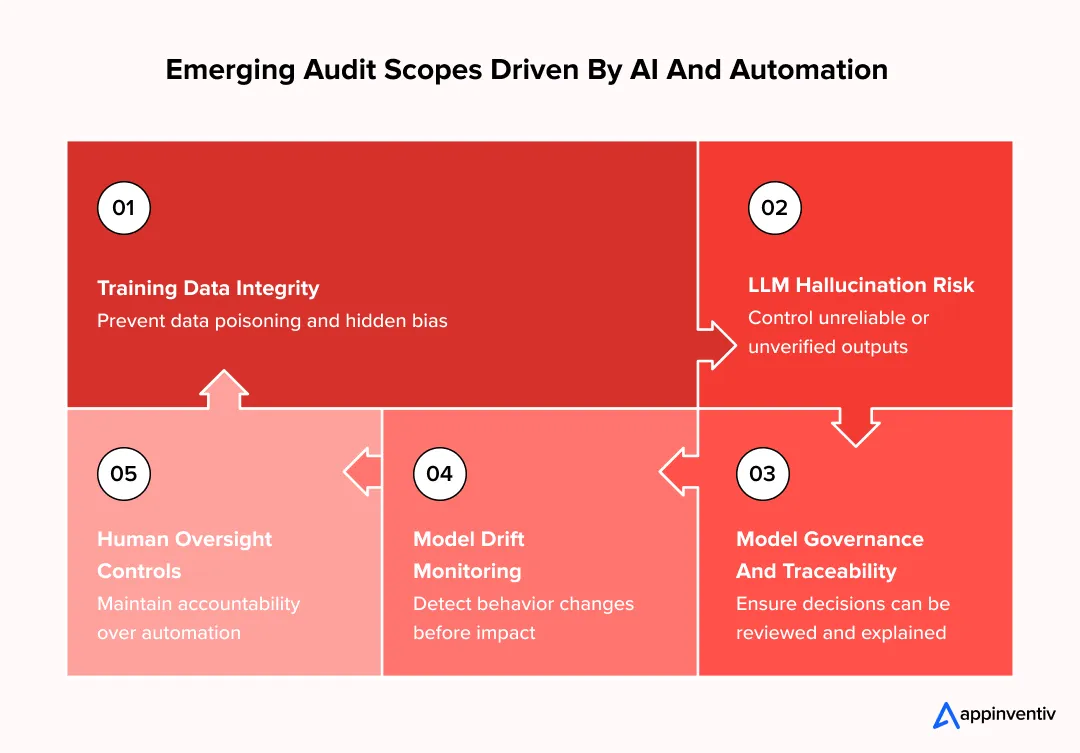
- Training data integrity and data poisoning risk: Audits now look closely at how training data is sourced, validated, and changed over time. Weak controls can allow biased, corrupted, or manipulated data to influence model behavior. In production, this rarely causes obvious failures. Instead, it leads to subtle decision errors that are difficult to trace and correct.
- LLM hallucination and output reliability risk: For generative AI systems, audits focus on how unreliable outputs are handled. This includes checking whether responses are grounded in verified sources, how confidence thresholds are applied, and what fallback mechanisms exist when outputs cannot be validated. In customer-facing or regulated environments, unmanaged hallucinations quickly become trust and compliance issues.
- Model governance and traceability: Enterprises increasingly audit whether AI-driven decisions can be reviewed after the fact. This means examining prompt design, output logging, versioning, and whether decision paths can be reconstructed when questions arise. Lack of traceability is treated as a governance risk, not a technical gap.
- Model drift and behavior change over time: AI systems change as data patterns shift. Audits assess how performance degradation is detected, how retraining is controlled, and whether changes in behavior are visible before they affect outcomes. This is especially important for models operating continuously in live environments.
- Human oversight and intervention controls: Mature audits also check whether meaningful human oversight exists. High-impact AI decisions are reviewed for escalation paths, approval workflows, and override mechanisms. Systems that rely entirely on automated output without intervention points are flagged as higher risk, regardless of accuracy metrics.
The takeaway is clear. AI in software audit is no longer about confirming that a model works in isolation. It is about ensuring AI systems remain understandable, controllable, and aligned with enterprise risk tolerance once they become part of day-to-day operations.
How Enterprises Perform Software Audits: A Structured Framework
In mature enterprises, a software audit usually begins after something feels off. Release velocity slows, security exceptions increase, or compliance reviews start raising uncomfortable questions. At that point, leadership needs clarity, not a surface review.
Effective audits are structured to explain “where risk is accumulating, why controls are breaking down, and what needs attention first.” The software audit process below reflects how audits are run when they are expected to influence real decisions.
Before the Audit: Governance and Scope Alignment
The preparation phase is where most audits either gain focus or lose credibility. Enterprises start by defining the audit around risk scenarios, not assets.
Audit objectives are typically aligned to triggers such as upcoming regulatory reviews, cloud migration plans, repeated incident patterns, vendor dependency concerns, or M&A activity. This alignment ensures the audit is anchored to material business risk rather than technical completeness.
Preparation work usually includes:
- Identifying in-scope systems based on business criticality, not system count
- Mapping ownership across product teams, shared platforms, security, and third-party vendors
- Defining scope boundaries across environments, regions, and data classifications
- Establishing access using least-privilege, read-only roles with time-bound credentials
- Validating architecture diagrams, dependency graphs, and service inventories against production reality
- Verifying the integrity of data sources such as logs, telemetry, license usage records, and CI/CD metadata
Before execution, enterprises perform a materiality assessment. Systems are ranked using criteria like revenue impact, regulatory exposure, dependency density, and failure blast radius. This step introduces accountability early and prevents effort from being diluted across low-risk systems.
During the Audit: Assessment and Evidence Collection
Execution focuses on observable system behavior rather than stated intent. Mature audits prioritize what systems do in production, not what policies claim they should do.
Assessment typically spans multiple technical layers:
- Reviewing service boundaries, coupling, and architectural patterns that affect scalability and fault isolation
- Examining identity and access controls including RBAC design, privilege escalation paths, secrets storage, and key rotation practices
- Assessing vulnerability management workflows, patch cadence, and exposure windows rather than static scan results
- Analyzing cloud and infrastructure configurations for network exposure, configuration drift, backup consistency, and availability design
- Reconciling license entitlements against actual usage using identity logs, usage telemetry, and billing data
- Inspecting CI/CD pipelines for approval gates, separation of duties, rollback mechanisms, and deployment traceability
- Validating process execution through interviews with engineers, SREs, security teams, and operations leads
At this stage, auditors pay close attention to mismatches. Gaps between documented controls and real workflows often reveal deeper governance and ownership issues.
After the Audit: Translating Findings into Action
Once evidence collection is complete, the audit shifts from analysis to prioritization. Enterprises do not treat every finding as equal, nor do they attempt to fix everything at once.
Post-audit work typically involves:
- Grouping findings by failure mode rather than listing isolated issues
- Scoring risk based on likelihood, impact, and systemic exposure
- Translating technical gaps into business consequences such as outage risk, compliance exposure, or operational drag
- Sequencing remediation based on enterprise risk tolerance and delivery capacity
- Assigning ownership across engineering, security, and business leadership
- Separating immediate containment actions from structural changes that require roadmap planning
The outcome is not just a software audit report. It is a decision framework that clarifies what must be addressed now, what can be planned, and what risks leadership is consciously accepting. This is where audits stop being diagnostic and start shaping enterprise behavior.
See how structured audits support governance, compliance, and risk prioritization.
What Are the Common Challenges in Enterprise Software Auditing?
Enterprise organizations encounter a consistent set of obstacles when conducting audits at scale. These challenges of software auditing are rarely about missing tools or technical skill. They arise from how software estates evolve over time and how responsibility is distributed across teams.
Legacy Systems With Limited Documentation
Many enterprises still depend on systems built years ago, often before modern documentation and governance standards existed.
This typically results in:
- Monolithic architectures with embedded business logic
- Custom integrations lacking version history or ownership records
- Critical operational knowledge residing with a small group of individuals
To manage this, mature organizations apply software auditing best practices that focus on reconstructing system behavior during the audit. Dependency mapping, runtime analysis, log inspection, and live walkthroughs with engineering teams are used to understand how these systems actually operate today.
Tool Sprawl And Fragmented Data Sources
Large organizations rely on multiple tools across monitoring, security, asset management, and delivery pipelines. Each tool provides partial insight, but none represent the full picture.
This leads to:
- Conflicting asset inventories
- Inconsistent software usage and licensing data
- Visibility gaps between cloud, SaaS, and on-prem environments
Experienced audit teams avoid chasing perfect data. Instead, they normalize inputs across systems, validate findings through sampling, and prioritize correlation over completeness to maintain audit momentum and decision relevance.
Organizational Resistance And Ownership Ambiguity
Software audits often surface gaps that teams were not prepared to address.
Common issues include:
- Systems shared across teams without clear ownership
- Delays in granting access or producing evidence
- Defensive reactions when findings are perceived as individual performance issues
Mature organizations reduce resistance by framing audits as governance initiatives rather than fault-finding exercises. Clear ownership models and executive sponsorship help keep the focus on enterprise risk rather than team-level blame.
Translating Technical Risk Into Executive Language
One of the most persistent challenges of software auditing is communication.
Audits lose impact when:
- Risks are described only in technical terms
- Severity is not tied to business impact
- Leadership cannot differentiate critical findings from low-priority noise
Effective audits translate technical gaps into outcomes such as downtime risk, regulatory exposure, customer impact, or cost escalation. This translation is essential for audit findings to influence decisions at the executive level.
Balancing Audit Depth With Operational Continuity
Audits that disrupt delivery quickly lose support.
Enterprises commonly struggle with:
- Audit activity overlapping with release cycles
- Performance degradation from intrusive scans
- Engineering time diverted from critical initiatives
Mature audit programs scope reviews around operational realities. Read-only access, phased execution, and risk-based sampling are used to limit disruption while preserving depth where it matters most.
Use Cases Where Software Audits Become Non-Negotiable
In most enterprises, the decision to run a software audit comes after something concrete breaks alignment. A deal feels riskier than expected. A cloud move exposes unknown dependencies. Compliance timelines start slipping. These are not abstract triggers. They are moments when leadership realizes it no longer has a reliable picture of how software actually behaves across the organization.
| Enterprise Scenario | What Breaks Down | Why a Software Audit Is Triggered |
|---|---|---|
| Pre-Merger Or Acquisition Due Diligence | Hidden licensing risk, fragile integrations, unclear data controls | Prevents post-deal surprises and delayed system integration |
| Legacy Modernization And Re-Architecture | Undocumented dependencies, growing technical debt, scalability limits | Stops guesswork from driving architecture and modernization decisions |
| Cloud Migration Readiness And Validation | Unknown data flows, inconsistent access controls, configuration drift | Ensures legacy risk is not replicated in cloud environments |
| Regulatory And Customer Compliance Reviews | Incomplete evidence, inconsistent control enforcement | Avoids failed audits and last-minute remediation pressure |
| Recurring Security Incidents Or Performance Issues | Repeated outages, controls failing in production | Identifies structural weaknesses instead of patching symptoms |
| Rapid Scaling Across Regions Or Business Units | Tool sprawl, process divergence, fragmented visibility | Restores governance without slowing expansion |
| Vendor Rationalization And Portfolio Cleanup | Redundant tools, unused licenses, fading ownership | Reduces cost leakage and unmanaged dependency risk |
Pre-Merger Or Acquisition Technical Due Diligence
During acquisitions, software risk is often underestimated because it hides behind revenue and growth narratives. Once integration begins, licensing gaps, brittle integrations, or undocumented data flows surface quickly.
Enterprises initiate audits here to understand:
- How tightly systems are coupled and where integration will stall
- Whether licensing terms survive ownership changes
- How security controls and data handling actually work in practice
- What remediation effort is required before systems can be consolidated
Without this clarity, post-deal surprises become inevitable.
Legacy Modernization And Platform Re-Architecture
Legacy systems rarely fail outright. They slow teams down, resist change, and accumulate exceptions over time.
Audits are triggered when organizations need to answer questions like:
- Which systems can realistically be modernized versus replaced
- Where undocumented dependencies will block re-architecture
- How technical debt is affecting scalability and stability
- What risks modernization will expose before they are addressed
At this stage, audits stop guesswork from driving architectural decisions.
Also Read: Legacy Application Modernization Strategy
Cloud Migration Readiness And Post-Migration Validation
Cloud initiatives often assume a cleaner starting point than reality allows. Hidden dependencies, inconsistent access controls, and weak observability only become visible after workloads move.
Enterprises use audits to:
- Map dependencies and data flows before migration
- Identify systems that need refactoring rather than lift-and-shift
- Validate access controls, logging, and monitoring after migration
- Catch configuration drift introduced during rapid cloud adoption
This prevents cloud environments from inheriting legacy risk at scale.
Preparing For Regulatory And Customer-Driven Compliance Reviews
Formal audits rarely fail because controls do not exist. They fail because evidence is incomplete or inconsistent.
Software audits are triggered when organizations need to:
- Verify that controls are enforced consistently across systems
- Ensure audit trails, logs, and access records are reliable
- Identify gaps early instead of during formal assessments
- Avoid last-minute remediation that disrupts delivery
This shifts compliance from reactive cleanup to planned execution.
Recurring Security Incidents Or Performance Degradation
When the same issues keep resurfacing, the problem is rarely the incident itself.
Enterprises initiate audits to:
- Identify structural weaknesses behind repeated outages or breaches
- Understand how failures propagate across systems
- Examine whether controls work only on paper or in production
- Reduce operational noise by fixing root causes
The audit becomes a way to stabilize the environment, not just patch it.
Rapid Scaling Across Regions Or Business Units
Growth introduces inconsistency faster than governance can react. Teams adopt tools independently. Standards drift. Visibility fragments.
Audits are triggered to:
- Rebuild a consistent view across regions and units
- Align access, deployment, and monitoring practices
- Reduce divergence without slowing expansion
- Restore control without centralizing everything
This keeps scale from turning into long-term risk.
Vendor Rationalization And Software Portfolio Cleanup
Over time, software portfolios become crowded. Redundant tools linger. Licenses go unused. Ownership fades.
Enterprises audit their portfolios to:
- Identify overlap and underutilization
- Understand contractual and licensing exposure
- Reduce dependency on critical vendors
- Support consolidation decisions with real usage data
These audits often uncover both cost inefficiencies and governance gaps.
Across all these situations, the trigger is the same. Leadership needs answers it cannot get from dashboards alone. When that happens, a software audit becomes less about inspection and more about restoring confidence in decisions that carry real operational and financial weight.
How Enterprises Prioritize Software Audit Risks
A software audit usually produces more findings than teams can address at once. The real challenge is deciding where attention should go first. Mature enterprises prioritize issues based on material impact and exposure management, not on how many findings appear in the report.
Start With Severity And Likelihood
Not every high-severity issue is urgent, and not every frequent issue is critical. Enterprises assess:
- How severe the impact would be if the issue materializes
- How likely it is to occur in real operating conditions
This prevents over-focusing on theoretical risks while missing patterns that repeatedly disrupt operations.
Factor In Business Criticality And Dependencies
Risk increases when issues affect systems that other services rely on.
- Revenue-generating and customer-facing systems are weighted higher
- Platforms with many upstream or downstream dependencies receive added priority
A small gap in a highly connected system can create outsized exposure.
Account For Regulatory And Contractual Exposure
Some risks must be addressed regardless of technical complexity.
- Compliance obligations and audit commitments
- Customer and partner contractual requirements
- Potential legal or reputational impact
These issues escalate quickly to avoid external consequences.
Balance Containment With Long-Term Remediation
Enterprises separate immediate risk reduction from structural fixes.
- Short-term actions reduce exposure quickly
- Long-term remediation is planned into delivery roadmaps
This approach allows teams to stabilize risk without disrupting ongoing initiatives.
Risk vs. Effort Matrix: How CTOs Prioritize Audit Findings
Not every audit finding deserves the same response. Enterprises that act fastest use a Risk vs. Effort lens to separate quick wins from long-term structural work. This helps leadership reduce exposure early while planning complex remediation without disrupting delivery.
| Impact / Effort | Low Effort | High Effort |
|---|---|---|
| High Impact | Quick Wins • Updating deprecated libraries and frameworks • Fixing misconfigured access roles or excessive privileges • Enforcing missing encryption or logging controls • Closing unused network ports or public endpoints | Strategic Investments • Decoupling monolithic systems • Re-architecting tightly coupled integrations • Migrating critical workloads to cloud-native patterns • Replacing legacy identity or access models |
| Low Impact | Housekeeping • Cleaning unused feature flags • Removing dormant test accounts • Documentation alignment | Defer Or Reassess • Low-value refactors • Cosmetic tooling changes • Non-critical platform upgrades |
How Enterprises Use This Matrix in Practice
- Start with High Impact, Low Effort items to reduce risk quickly and build momentum
- Plan High Impact, High Effort work into roadmaps tied to modernization or transformation programs
- Avoid over-investing in Low Impact findings unless they unblock future initiatives
This approach ensures audit remediation improves risk posture immediately while keeping long-term architectural work aligned with enterprise priorities and delivery capacity.
Enterprise Software Audit Checklist: What A Comprehensive Audit Should Always Cover
Enterprise audits tend to lose value when they become overly broad or overly technical. A practical software audit checklist keeps teams aligned on core areas that consistently affect risk, cost, and operational stability. The goal is not exhaustive inspection, but disciplined coverage of the areas that most often fail at scale.
The checklist below reflects what experienced enterprises expect to review in every meaningful audit.
| Audit Area | What Teams Typically Review | Why Enterprises Care |
|---|---|---|
| Architecture And Code Health | System structure, service boundaries, maintainability issues, accumulated technical debt | Signals long-term scalability and reliability risk |
| Security Vulnerabilities And Access Controls | Identity and access models, privilege levels, encryption practices, vulnerability handling | Directly impacts breach exposure and control strength |
| Compliance And Regulatory Gaps | Control consistency, audit evidence, logging, policy enforcement | Determines readiness for regulatory and customer audits |
| Infrastructure Efficiency And Resilience | Cloud and on-prem configuration, availability design, backup and recovery posture | Affects uptime, performance, and recovery during incidents |
| License Usage And Vendor Risk | Actual usage vs entitlements, dependency concentration, contract exposure | Prevents cost leakage and compliance penalties |
| DevOps Maturity And Release Governance | CI/CD controls, approval workflows, rollback capability, change traceability | Reduces production instability and release risk |
| Data Handling And Privacy Controls | Data access, classification, retention, monitoring | Limits regulatory, legal, and reputational exposure |
Used consistently, this checklist creates a shared baseline across audits. It helps enterprises maintain rigor without turning audits into open-ended investigations, while still leaving room to go deeper where material risk demands it.
How Are Enterprises Moving Toward Continuous Software Auditing?
In most enterprises, the problem is not that audits are done incorrectly. It is that they are done too late. By the time a traditional audit is completed, the environment it reviewed has already changed. New services are live, access has shifted, and configurations have drifted. Continuous auditing emerges as a response to that reality, not as a trend.
- Using software and usage signals to stay current
Enterprises increasingly rely on ongoing usage signals instead of periodic data collection. License consumption, access activity, application usage, and billing data are reviewed continuously to understand what is actually running and who is using it. This makes licensing risk, unmanaged SaaS adoption, and unexpected dependencies visible while corrective action is still practical. - Embedding audit controls into delivery workflows
Rather than reviewing changes after the fact, many organizations move audit checks closer to where change happens. Configuration validation, dependency analysis, and policy enforcement are built into DevOps pipelines. When a deployment introduces risk, it is surfaced immediately, while the context is still clear and ownership is obvious. - Detecting drift before it becomes exposure
Enterprise risk rarely appears overnight. It builds slowly through permission creep, configuration changes, and exceptions that become permanent. Continuous monitoring across identity systems, cloud platforms, and runtime environments allows teams to see this drift early, before it turns into a security or compliance issue. - Reducing disruption without weakening control
One of the most practical benefits of continuous auditing is operational. Teams spend less time preparing evidence or responding to audit requests. Oversight happens quietly in the background. Control improves, but delivery is not slowed by repeated review cycles.
For enterprise leaders, this shift is less about automation and more about alignment. Auditing moves from a periodic interruption to an embedded capability that evolves with the systems it governs.
Choosing the Right Software Audit Partner: What Enterprises Should Evaluate Before Engagement
For enterprises, the real risk is not choosing the wrong audit tool. It is choosing a partner who cannot operate within enterprise constraints. Audits break down when partners underestimate organizational complexity, overlook governance realities, or deliver findings that stall in steering committees. This is why enterprises evaluate audit partners based on their ability to work inside the system, not just assess it from the outside.
Proven Enterprise And Industry Experience
Enterprises do not struggle with lack of standards. They struggle with scale, legacy decisions, and competing priorities across teams.
Partners with real enterprise experience understand:
- Why ownership is distributed and often unclear
- Why documentation trails execution
- Why change moves through architecture boards and risk committees
This familiarity prevents unrealistic recommendations and reduces friction during audits, especially in environments shaped by years of acquisitions or regulatory pressure.
Ability To Translate Technical Risk Into Business Outcomes
A common enterprise frustration is receiving technically accurate findings that cannot be acted on.
Strong partners help solve this by:
- Explaining how risks affect availability, compliance timelines, or customer exposure
- Showing where risk concentration could slow growth or modernization
- Enabling leadership to prioritize without debating technical nuance
This translation is what turns audit findings into decisions instead of discussion points.
Security, Compliance, And Governance Expertise
Enterprise audits sit at the intersection of multiple oversight layers. When partners lack depth in any one of them, audits lose momentum.
Enterprises look for partners who understand:
- How security controls are validated, not just designed
- How compliance evidence is reviewed under scrutiny
- How audit findings feed into governance, risk, and compliance cycles
This context allows audits to support governance rather than disrupt it.
Independent, Tool-Agnostic Assessments
One of the fastest ways to lose enterprise trust is to blur assessment with implementation.
Enterprises value independence because:
- It protects the credibility of findings in executive reviews
- It avoids internal pushback tied to perceived vendor bias
- It keeps focus on exposure and control effectiveness
Tool-agnostic partners make it easier for organizations to accept findings without questioning intent.
Post-Audit Remediation And Advisory Support
The most common enterprise complaint is that audits end too early.
Enterprises need support with:
- Sequencing remediation without disrupting delivery
- Validating fixes in complex environments
- Aligning remediation with ongoing transformation initiatives
Partners who stay engaged beyond the report help audits deliver lasting value instead of becoming closed documents.
For enterprises, the right audit partner does not just identify issues. They reduce uncertainty, respect governance constraints, and support change over time. When that happens, the relationship evolves naturally into a strategic partnership built on trust and long-term alignment rather than one-off assessments.
Get expert support to reduce risk and move forward with clarity.
Turning Software Audits Into Long-Term Enterprise Advantage
At enterprise scale, a software audit is not about finding isolated gaps. It is about restoring confidence in systems that support growth, compliance, and customer experience. When audits are approached with the right structure and intent, they help leadership see where risk is accumulating, where decisions are being delayed by uncertainty, and where investment will have the highest impact. Done well, audits stop being reactive controls and start functioning as a foundation for better governance.
This is where software consulting services matter. Enterprises often need more than an assessment. They need context, prioritization, and guidance that fits their operating reality. At Appinventiv, audit engagements are shaped around real business outcomes, not just technical findings. Our experience delivering complex digital platforms, including large-scale consumer applications such as this Arts, Leisure, and Travel booking solution, gives us a practical understanding of how architecture, performance, and governance decisions play out in production environments.
Ultimately, audits create the most value when they connect directly to execution. Enterprises that pair audits with strong software development services are better positioned to act on findings, modernize safely, and reduce risk over time. Whether the goal is stabilization, transformation, or scale, the combination of audit insight and delivery capability allows organizations to move forward with clarity rather than caution.
If you are evaluating how audit insights translate into real-world execution, a focused conversation with our experts can help clarify next steps.
FAQs
Q. How Long Does A Software Audit Take?
A. The duration depends on scope, system complexity, and audit depth. For most enterprises, a focused audit covering critical systems typically takes a few weeks, while broader reviews spanning multiple platforms or regions may take longer. Clear scoping and ownership alignment significantly reduce delays when planning how to audit software effectively.
Q. How Does A Software Audit Support Regulatory Compliance?
A. A software audit helps organizations validate whether controls are implemented and operating as intended. It identifies gaps in access control, logging, data handling, and evidence readiness before formal reviews. This reduces last-minute remediation and strengthens defensibility during regulatory and customer-driven compliance assessments.
Q. What Is The Role Of ISO Standards In Software Audits?
A. ISO standards provide a structured benchmark for evaluating governance, security, and risk management practices. In software audits, they help assess whether policies, controls, and evidence align with accepted international expectations. Many enterprises use ISO-aligned audits to bring consistency across business units and regions.
Q. What Actions Should Be Taken After A Software Audit?
A. After an audit, enterprises should prioritize findings based on business impact, assign clear ownership, and define remediation timelines. Immediate containment actions are addressed first, followed by structural improvements aligned with long-term strategy. Organizations often engage a software audit company at this stage to validate fixes and guide remediation sequencing.
Q. What Risks Can A Software Audit Identify?
A. A software audit can uncover security exposure, licensing non-compliance, architectural weaknesses, operational inefficiencies, and governance gaps. It also highlights dependency risks and control failures that may not surface through routine monitoring or incident response.
Q. When Should A Business Conduct A Software Audit?
A. Enterprises typically conduct audits before major transitions such as acquisitions, modernization programs, cloud migrations, or regulatory reviews. Recurring incidents, rising software costs, or unclear ownership are also common triggers to hire software auditor support before risks escalate further.
Q. How Does AI Help In Modern Software Auditing?
A. AI enhances audits by analyzing large volumes of telemetry, configuration data, and usage patterns to surface anomalies early. It supports continuous monitoring, flags drift, and helps maintain accuracy across evolving environments. This reduces manual effort while improving consistency when following a structured software audit guide.
Q. Do Software Audits Cover Licensing And Usage Compliance?
A. Yes. Many enterprise audits include license and usage validation using a defined software license audit checklist and software license compliance audit checklist. These checks help identify unused licenses, over-deployment, and contractual exposure before vendors or regulators raise concerns.


- In just 2 mins you will get a response
- Your idea is 100% protected by our Non Disclosure Agreement.

The ROI of Strategic Insurance Technology Consulting for Legacy Modernization
Key takeaways: Insurance technology consulting delivers ROI only when modernization is tied to real workflows, not system replacement. Most legacy modernization failures stem from weak ROI definition and tracking, not from technology limitations. The strongest returns come from reduced operational friction, faster change cycles, and tighter claims and underwriting control. Delaying modernization incurs hidden costs…

Key Takeaways Use a scorecard-driven RFP and a technical assessment to compare vendors on capability, compliance, and delivery risk. Local partners provide regulatory and cultural alignment; hybrid teams often pair that with offshore cost efficiency. Start with a scoped pilot or MVP, milestone-based contracts, and clear IP/SLAs to reduce procurement risk. Require demonstrable security controls,…

A Strategic Framework for Proof of Concept Software Development
Key takeaways: Most enterprise PoCs fail due to a lack of decision clarity, not technical feasibility or innovation potential. A disciplined PoC framework reduces delivery risk before budgets, teams, and timelines are committed. Enterprise-grade PoCs validate feasibility, compliance, and scale assumptions under realistic operating constraints. Clear success metrics and governance turn PoCs into reliable inputs…